Creating and Configuring ISA Firewall Networks (2004) [v1.02]
By Thomas W Shinder MD, MVP
Got Questions? Go to:
http://forums.isaserver.org/ultimatebb.cgi?ubb=get_topic;f=26;t=000168 and ask!
The new ISA firewall (ISA Server 2004) sees the network environment in a significantly different way than does ISA Server 2000. If you’re a dyed in the wool ISA Server 2000 firewall admin, you’re well aware that it saw the network in terms of trusted and untrusted networks: trusted networks were on the Local Address Table (LAT) and untrusted networks are not on the LAT. Only communications between LAT and non-LAT hosts were exposed to the ISA Server 2000 stateful application layer inspection and stateful packet inspection mechanisms. Connections between LAT hosts were not exposed to ISA Server 2000’s stateful inspection routines.
LAT-based networking significantly limited the number of multinetworking scenarios the 2000 ISA firewall could support. For example, ISA Server 2000 really didn’t allow you to create multiple internal network DMZs, and public DMZs had to use public addresses. Even when you went ahead and created a public address DMZ, ISA Server 2000 didn’t perform stateful application layer inspection on communications moving between the Internet and the public address DMZ. This essentially reduced the level of security applied provided to the ISA Server 2000’s DMZ hosts to that seen with a typical stateful packet inspection-only hardware firewall (which isn’t much).
The good news is that the new ISA firewall (ISA Server 2004) applies both stateful filtering (stateful packet inspection) and stateful application layer inspection on all interfaces. For example, you can install 22 network interface cards in the new ISA firewall and stateful inspection is preformed on all these interfaces.
Not only is stateful inspection applied to all physical interfaces, the ISA firewall applies the same stateful filtering and stateful application layer inspection to VPN remote access client and VPN gateway connections. In addition, in contrast to the ISA Server 2000 firewall, the new ISA firewall prevents connections to itself and severely locks down connections that can be initated outbound from the ISA firewall itself.
Stateful Inspection Across ISA Firewall Networks
A key feature of the ISA firewall’s stateful inspection mechanisms is the concept of the ISA firewall Network (with a capital “N”). The ISA firewall performs stateful inspection on all communications traversing different ISA firewall Networks. An ISA firewall networks includes all IP addresses located behind a specific network interface.
For example, take a look at the figure below. This ISA firewall has four NICs:
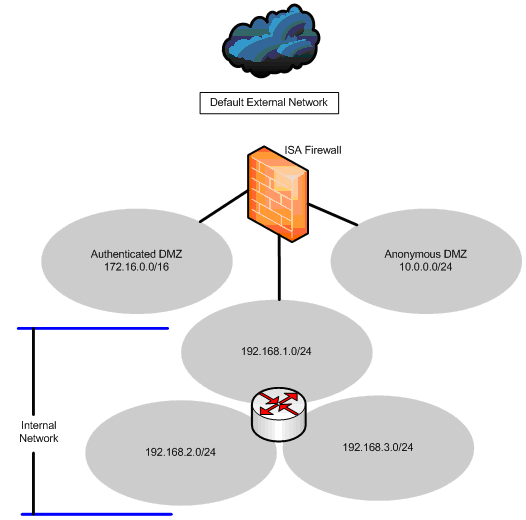
Each of these Network interfaces defines an ISA firewall Network. These Networks are defined as follows:
ISA FIREWALL NOTE:
The routing table on the ISA firewall in this example must configured with routes to network IDs 192.168.2.0/24 and 192.168.3.0/24, since these are non-local (not directly connected) networks. The gateway address for these routes would be the interface on the LAN router that interfaces with the same network as the interface the ISA firewall uses on the Internal Network.
The ISA firewall applies stateful packet inspection/stateful filtering and stateful application layer inspection on connections made from one ISA firewall Network to another ISA firewall Network. For example, stateful inspection is applied to connections in the following scenarios:
Pay close attention to the capitalization! When we use the term Network with a capital “N”, it refers to an ISA firewall Network. When we use network with a lower case “n”, it refers to a generic network. In addition, pay close attention to the capitalization used when network names are used.
For example, there is only one default Internal Network, which is defined during installation. However, you can create multiple internal Networks. Also, while there is a default External Network, which includes all addresses not defined on the ISA firewall, the external network interface might be connected to a DMZ segment between itself and an upstream front-end firewall or router. In this case, the network ID used on this DMZ segment can be used to create a custom external Network.
Another thing to be aware of is that stateful inspection is not performed on connections between hosts located on the same Network. For example, stateful inspection is not performed on connections in the following scenarios:
Hosts on the same ISA firewall Network connect directly to one another; they must not loop back through the ISA firewall. This becomes a bit problematic for Web Proxy clients, since Web Proxy clients may loop back through the ISA firewall to reach internal resources, and even Firewall clients may loop back if you haven’t configured your DNS infrastructure correctly.
In fact, on the “on subnet” network ID (on subnet meaning on the same network ID as local interface of the ISA firewall), SecureNAT clients are problematic, because you must not configure SecureNAT clients on the on subnet network to use the ISA firewall as their default gateway. Instead, you configure them to use the LAN router are their gateway.
ISA FIREWALL ALERT:
For a detailed discussion of these issues, including configuration options for “on subnet” hosts on an ISA firewall Network containing multiple networks and network IDs, please refer to our discussions on this subject in chapter 4 of Configuring ISA Server 2004
A solution to the Web Proxy and Firewall client problem is to configure Web Proxy and Firewall clients to use Direct Access to reach hosts on the same ISA firewall Network. I’ve covered Direct Access comprehensively in other articles on this site, and did a long dissertation on the subject in the ISA Server 2000 in Education Kit. If you haven’t check out the ISA in Education kit, you owe yourself the pleasure of doing so. There’s a ton of great info in that kit.
The key concept when it comes to ISA firewall Networks is that the NIC is the root of each Network. All addresses located behind a specific NIC installed on the ISA firewall are part of the same ISA firewall Network. There are only three exceptions to this rule:
. This is a built in Network that is defined as all addresses bound to each interface, physical or VPN, on the ISA firewall machine itself. Addresses are dynamically added or subtracted from the Local Host Network when you bind new addresses to any of the ISA firewall’s NICs
. This is a built-in Network that is defined by the addresses currently in use by VPN connections. These included both remote access VPN client connections and VPN gateway connections used to established VPN site to site links.
. This Network is used when you enable VPN Quarantine on the ISA firewall. VPN Quarantine is a very interesting and potentially powerful feature included with the ISA firewall, which allows you to “pre-qualify” VPN clients (such as checking them for latest hotfixes and other security updates) before they are moved from the Quarantined VPN Clients Network to the VPN Clients Network. The problems with the VPN Quarantine feature is that you have to be a rocket scientist to figure it out, and we even know a rocket scientist who can’t figure it out. The problem with VPN-Q is that you need to have very advanced scripting or programming skills to get it to do what you want it to do.
Let’s create a new ISA firewall Network to demonstrate the procedures and the available options.
Creating a New ISA Firewall Network
Consider the following scenario: you have installed the ISA firewall software on a machine with two NICs, one NIC is the external interface and one NIC is the internal interface. The internal interface is connected to the default Internal Network. During setup, you defined the addresses used by the default Internal Network and the ISA firewall’s setup routine created the Network for you.
Now you want to create a new Network that will be used by wireless LAN clients. You plan to connect a WAP to this network and allow untrusted wireless hosts access to the Internet and also allow trusted clients VPN access to the Internal Network. You install a third NIC into the ISA firewall machine and assign the IP address 10.10.10.1/24 to the WLAN network interface. The WAP will assign IP addressing information to the WLAN hosts, such as an IP address and a default gateway. The WLAN hosts will be assigned a default gateway that is the IP address on the WLAN Network’s interface on the ISA firewall.
Next, you want to configure this interface as the root of an ISA firewall perimeter Network that includes all addresses in network ID 10.10.10.0/24. You will then be able to use the WLAN ISA firewall Network to define access controls between it and other Networks.
Perform the following steps to create the new perimeter Network on the ISA firewall:
- In the Microsoft Internet Security and Acceleration Server 2004 management console, expand the server name and then expand the Configuration node. Click the Networks node.
- Click the Networks tab in the details pane and then click the Tasks tab in the Task Pane. On the Tasks tab, click the Create a New Network link.
- On the Welcome to the New Network Wizard page, enter a name for the new Network. In this example, we’ll name the new ISA firewall Network WLAN Network. Click Next.
- On the Network Type page you have a number of options. These are:
Internal Network
An internal Network is one that you consider an internal network. In general, we consider a network an internal Network when that Network does not contain any Internet facing hosts (that is to say, it doesn’t contain any hosts that Internet users can connect to via publishing rules).
Perimeter Network
A perimeter Network is one you consider to be a perimeter network. In general, we consider any network containing Internet facing hosts to be a perimeter network. In ISA firewall terms, any network on which you want to place published servers would be a good candidate for a perimeter network. Perimeter Networks are also good for untrusted hosts. Note that for both internal and perimeter Networks, you will have the option to configure properties of the Network in a similar way. We’ll look at what I mean by this later in this section.
VPN Site-to-Site Network
A VPN Site-to-Site Network is a special Network that you use to define the remote site Network for VPN site to site connections
External Network
An external Network is one that always contains untrusted hosts, such as a partner network that might connect to you Networks via VPN links to an upstream firewall/VPN server or gateway.
In this example, we’ll make our WLAN Network a perimeter Network. Select that option and click Next.

- On the Network Addresses page you define the addresses you want to use for the new Network. The best way to add new addresses is to use the Add Adapter button. If the routing table on the ISA firewall is properly configured, all the correct addresses will be added to the new Network. Click the Add Adapter button.
- In the Select Network Adapters dialog box, put a checkmark in the checkbox next to the NIC representing the DMZ interface. In this example, I’ve renamed the adapters in the Network and Dial-up Connections window to make them easier to identify. We’ll select the DMZ interface and then put a checkmark in its checkbox. Its important to select the adapter first, so that you can see the addresses it will add in the Network Interfaces Information box. Click OK.

- Click Next on the Network Addresses page.

- Click Finish on the Completing the New Network Wizard page.
- Click Apply to save the changes and update the firewall policy.
- Click OK in the Apply New Configuration dialog box.
- The new WLAN Network appears in the list of Networks.

Now, in order to communications to move between the WLAN Network and any other ISA firewall Network (including the default External Network), you must create a routing relationship between the WLAN Network and the destination Networks. In this example, we expect the WLAN Network to communicate with hosts on the Internet. We won’t be creating Access Rules that allow the WLAN Network to communicate with the Internal Network, so we don’t need to define a route relationship between the WLAN Network and the Internal Network.
The only access WLAN hosts will have to the WLAN Network and the Internal Network will be via VPN connections. By default, there is already a Route relationship between the VPN Clients Network and the Internal Network, so we don’t need to define a new relationship to allow VPN clients to connect to the Internal Network hosts.
However, there is no default route relationship between the WLAN Network and the default External Network, so we will need to create that relationship using a Network Rule. Network Rules allow you to set either a NAT or Route relationship between any two Networks. Route relationships are reciprocal and NAT relationships are one-way. This can be a potentially confusing issue, so make sure to check out our new book Configuring ISA Server 2004 for all the gory details and deployment scenarios.
Perform the following steps to create the route relationship:
- On the Networks node in the Microsoft Internet Security and Acceleration Server 2004 management console, click the Network Rules tab in the details pane of the console.
- In the Tasks tab, click the Create a New Network Rule link.
- On the Welcome to the New Network Rule Wizard page, enter a name for the Network Rule in the Network rule name text box. In this example, we’ll name the rule WLAN Network to External. Click Next.
- On the Network Traffic Sources page, click the Add button.
- In the Add Network Entities dialog box, click the Networks folder and then double click on the WLAN Network entry. Click Close.

- Click Next on the Network Traffic Sources page.
- On the Network Traffic Destinations page, click the Add button.
- In the Add Network Entities dialog box, click the Networks folder and then double click the External entry. Click Close.
- On the Network Relationship page, select the Network Address Translation (NAT) option. Click Next.

- Click Finish on the Completing the New Network Rule Wizard page.
- Click Apply to save the changes and update the firewall policy.
- Click OK in the Apply New Configuration dialog box.
- The new Network Rule appears in the list of Network Rules.

Configuring ISA Firewall Network Properties
At this point you can create Access Rules that control traffic between the WLAN Network and the Internet. You can also enable Web Proxy and Firewall client support for this Network. In order to do this, click on the Networks tab in the details pane of the Network node. Double click the WLAN Network. This brings up the WLAN Network Properties dialog box.
Here you can configure Firewall client settings, Web Proxy client settings, and much more. One thing you might want to do is configure Web Proxy client settings. Click the Web Proxy tab and put a checkmark in the Enable Web Proxy clients checkbox. Click OK and then click OK to save the changes to the firewall policy.

There are some fancy tricks you can do for authentication for hosts on the WLAN Network (or any other ISA firewall Network you create). We discuss these options in detail in our book, Configuring ISA Server 2004.
The example we discussed in this article is based on a WLAN configuration we’ve set up in several businesses and use in our own business, and it works a treat. If you’re interested in a detailed account of the configuration on how to create perimeter Networks for your WLANs, let me know and I’ll schedule an article on the subject.
I hope you enjoyed this article and found something in it that you can apply to your own network. If you have any questions on anything I discussed in this article, head on over to http://forums.isaserver.org/ultimatebb.cgi?ubb=get_topic;f=26;t=000168 and post a message. I’ll be informed of your post and will answer your questions ASAP. Thanks! –Tom
If you would like us to email you when Tom Shinder releases another article on ISAserver.org, subscribe to our ‘Real-Time Article Update’ by clicking here. Please note that we do NOT sell or rent the email addresses belonging to our subscribers; we respect your privacy.




