Introduction
The state of security within the Windows realm is a little out of control. There are so many “sides” to the issue, but the reality is always the same. The reality of securing a Windows environment is just like the remainder of the IT and OS world. Every OS is vulnerable and typically the “top dog” is attacked due to the shear mass of computers that the virus/worm can hit. In the case of ConFlicker, the story is the same. The “sides” include those that say Microsoft is insecure, Microsoft does not know how to secure an OS, Microsoft is secure if people just patch their computers, Microsoft is secure if companies do not allow users to be local Administrators, and the list goes on. For ConFlicker, the patch was made available within hours of the worm showing itself, but still the number of computers that are infected continues to grow. Why is this the case? Logic would show that computers are not being patched properly! This article will cover some methods that you can use to help secure a desktop from becoming infected with the ConFlicker worm, based on how the worm is attacking the system.
Basic Information about ConFlicker
ConFlicker has had two variations since it was first introduced in November of 2008. The first was not as severe as the second, which makes sense. You can read information that was posted about ConFlicker by Microsoft in their security update MS08-067 here. The next generation of ConFlicker was then unleashed in December 2008, which has a more widespread and lethal attack. You can read about the new worm here.
ConFlicker, in its newest form, will attack the system at various points, attempting to embed itself wherever possible, in hopes that it will not be detected, plus it will be very hard to remove it if detected. ConFlicker will attack the following areas of your computer:
- Creates hidden DLL file with various names in Windows System folder.
- Creates hidden DLL file under %ProgramFiles%\Internet Explorer or %ProgramFiles%\Movie Maker folders.
- Creates entry in Registry under HKCU\Software\Microsoft\Windows\CurrentVersion\Run.
- Loads itself as a service in the Registry under HKLM\SYSTEM\CurrentControlSet\Services.
- Attempts to copy itself onto target machines under the ADMIN$ share using current credentials of logged on user.
- Attempts to “hack user passwords” of target machine’s local SAM using common weak passwords.
- Creates remote scheduled task on target machine (if username and password is compromised).
- Copies itself to all mapped and removable drives.
- Creates an autorun.inf file on all drives which will exploit the AutoPlay feature if enabled, thus launching the worm on the infected share during autorun.
- Disables the viewing of hidden files.
- Modifies the system’s TCP settings to allow a large number of simultaneous connections.
- Deletes the Registry key for Windows Defender.
- Resets System Restore Points.
- Downloads files from various Web sites.
As you can see, ConFlicker is a very active worm, infecting a variety of different parts of the operating system, folders, Registry, and other key areas of the system.
Obtaining the Patch
The best solution to defending against ConFlicker is to obtain the patch from Microsoft here.
You will notice that Windows Vista and Windows 2008 are only “Important” level of vulnerability, due to the capability of these operating systems to protect and secure more efficiently than previous versions.
Group Policy Settings to Help Protect Against ConFlicker
First and foremost, if the user of the desktop that is being attacked is NOT a member of the local Administrators group, the worm will have a tough time infecting the computer. So, in order to negate this situation, you can use Group Policy Preferences to remove the user account from the local Administrators group. This policy is located under User Configuration\Preferences\Control Panel Settings\Local Users and Groups. You will just configure a Local Group policy for “Administrators”, then you will select the radio button that says “Remove the current user”, which is shown in Figure 1.
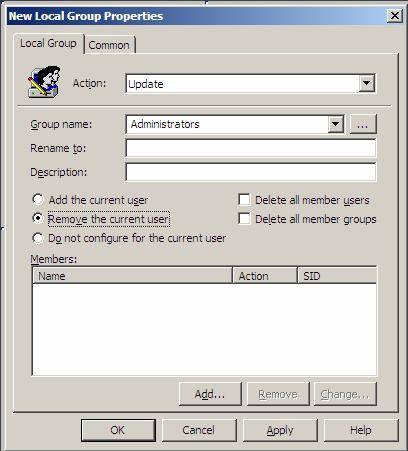
Figure 1: Removing the current user account from the local Administrators group
Since the worm will attempt to enumerate and then attack the local list of usernames on a target computer, you should also ensure that there are no additional user accounts in the local SAM of each desktop. This can easily be remedied by using the same policy shown in Figure 1, but to also enable the deletion of all member users from the Administrators group, which is shown in Figure 2.

Figure 2: Removal of all member users from local Administrators group
Note:
In Figure 2, the Domain Admins group and local Administrator account can be forced into the local Administrators group, which is a best security practice.
Although this next setting is not available for Windows XP or Server 2003, it is an excellent configuration for Windows Vista and Server 2008. Group Policy controls all areas of User Account Control and can centrally manage how UAC is set for both Administrators and standard users. UAC should be enabled and then prompt for consent (for Administrators) and silently deny elevation (for standard users). This will prohibit viruses, worms, and other malicious software from performing tasks that modify the operating system files and Registry. These actions should only be performed in the foreground when the user is attempting to perform one of the administrative tasks. ConFlicker attempts to write to and modify numerous protected files, folders, and registry entries behind the scenes. These UAC settings can be found under Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options. Figure 3 illustrates the full list of UAC settings that can be configured.

Figure 3: UAC settings control access on Windows Vista and Server 2008 computers
Note:
For more information on configuring and understanding UAC, refer to “Top 5 Security Reasons to Use Vista“.
A final set of Group Policy settings that need to be configured are related to passwords for user accounts. Since ConFlicker attempts to guess passwords, it is important to ensure that the Password Policies are set to have long and complex passwords. This is typically done in the Default Domain Policy for Active Directory domains, but can also be configured in the local GPO for stand alone computers. The settings for Password Policies are located under Computer Configuration\Windows Settings\Security Settings\Local Policies\Account Policies, which are shown in Figure 4.

Figure 4: Password Policies restrict how weak or strong a password can be for user accounts.
A final Group Policy setting is configurable for the control of AutoPlay. Since ConFlicker will write to removable devices which are controlled by AutoPlay, the worm can be initiated just by placing an autorun.inf file on the removable device. However, if AutoPlay is disabled, this action is not allowed. To disable AutoPlay via Group Policy, go under Computer Configuration\Administrative Templates\Windows Components, as shown in Figure 5.

Figure 5: AutoPlay can be disabled via Group Policy
Summary
ConFlicker unfortunately is thriving due to the lack of action by the industry as a whole. The patch has been available and the ability to disable the worm has also been available since the worm was released. If administrators, companies, and users would take action to deny the worm further infiltration, there would no longer be a threat. Until then, the worm will continue to spread. That is why you need to take action immediately to stop this worm from propagating. The best action is to configure Group Policy to deny the access to the system and help improve the security of the passwords on the system. Denying access of ConFlicker to the system is easy, as long as the system is configured to not allow behind the scenes access as Administrator. Passwords are easily protected and should be configured to be long and use complexity. With these settings in place, your systems will be protected from worms like ConFlicker.




