Ever since Microsoft released Windows 2000 way back when, the options for delegating certain tasks have been available. The concepts of delegation can be a bit confusing, but in the core of what the delegation provides is essential to an efficient network. Without the use of delegations, you are stuck with only default groups that grant administrative privileges over certain tasks and objects. For example, without delegation over user and group accounts, a user must be placed in the Account Operators group to be given the ability to just manage users, groups, and computers in the domain. Of course, a user could also be placed in the Domain Admins or Enterprise Admins groups, but this would grant them far too many privileges than just managing accounts. In a similar manner, placing users in the Account Operators group also grants them too many privileges, such as modifying not only user accounts, but all administrative accounts. Delegation solves this issue, by allowing very granular delegations to objects and tasks throughout the enterprise.
Breaking down Delegation
As you evaluate making your network administration more efficient by implementing delegation, you will need to consider a few things:
- Who will receive the delegated privileges?
- What task should the group of users be delegated?
- Which objects should the group be delegated control over?
- Where is the delegation performed?
- What specific permissions do I configure to accomplish the delegation?
If we tackle each of these items separately, we can get to the bottom of each faster when we need to put the rubber to the road.
For the first, it is ideal to create groups which will be granted the delegations. This way, it is easy to add more users and just as easy to remove the user from having the privilege.
For the second point, not all tasks can be delegated. So, a list of possible delegations should be created. We will create these lists later on, per tool where the delegation can be established. Once you have a list of delegations to choose from, it is much easier to pick and choose which ones you want to dole out.
For object delegation, you will need to get granular in what you want to delegate. Do you want to allow others to control user accounts, or just some of the properties of users accounts? You can also choose from groups, computers, organizational units, Group Policy Objects, etc.
One of the most important concepts is to know where to go to configure the delegation. There are three primary tools that you have to configure delegations. We will break down all three tools later on.
Finally, once you get into the tool and know what you want to delegate, you still need to know which “clicks and boxes” will accomplish your goals. Some delegations are easy, where others require you to do some testing and evaluation before you can be assured you are done.
Active Directory Users and Computers
Active Directory has a complete, comprehensive delegation component. If you are not using delegation within AD, you are missing out on one of the most important reasons to move to AD. Delegation within AD allows the administrator of AD to configure groups of users to have access to certain tasks. The benefit of this is that tasks can be very detailed and reduction of overall administrative control is limited to only those tasks that should be granted to the group of users.
In my opinion, the key to understanding delegation within AD is what the possibilities are. Microsoft added quite a few options when they went to Server 2003, but there are still unlimited options for delegating administrative control. Here is a list of objects that are typically configured with delegated controls:
- user accounts
- group accounts
- organizational units
- computer accounts
Although I list all of the objects that can be controlled, it is important to understand the limitations of delegating to each object. Specifically, I want to discuss what delegations are possible for user, group, and computer accounts.
- reset passwords
- manage user accounts
- manage groups
- modify group membership
- add computer to OU
- computers have little control… use user rights via GPOs
Some of the delegations can be seen in Figure 1.

Figure 1: ADUC delegation wizard
Group Policy Management Console (GPMC)
The GPMC provides an environment that not only allows for administration of GPOs, but also protection of who can manage the GPOs. With the advent of the GPMC all of the GPO management and delegation is now encompassed within this tool. I want to be clear in that the GPMC only provides delegation of GPO management, not any other AD management delegations. So, anything like controlling OUs, users, groups, etc must be done within the ADUC.
For the delegations that come with the GPMC you have the following delegation options:
- Create GPOs
- Edit GPOs
- Delete and manage security of GPOs
- Link GPOs
- Read GPO settings
Some of these delegations can be seen in Figure 2.

Figure 2: GPMC delegations to control and manage GPO management
Since the creation of GPOs is done for the “domain,” there is no mechanism to control this just for an OU. However, you can delegate who can link GPOs to OUs, which gives you a bit of control over tasks like these that you might want to be delegated at a more granular level. Linking GPOs is delegated at the domain, OUs, or sites, since these are the only nodes where GPOs can be linked. Editing, managing, deleting, and reading GPOs is delegated at each GPO, giving you very granular control over these delegations.
Advanced Group Policy Management (AGPM)
The final piece to the delegation model for AD and GPOs is AGPM. This tool provides the grand finale for GPO management. The GPMC is great, for what it does. However, it lacks key management features that the AGPM fulfills. AGPM provides the following features over GPMC:
- offline editing of GPOs
- change management of GPO edits
- roll-back and roll-forward to archived GPOs
- automatic backups of GPOs as the are modified
Some of these delegations can be seen in Figure 3.
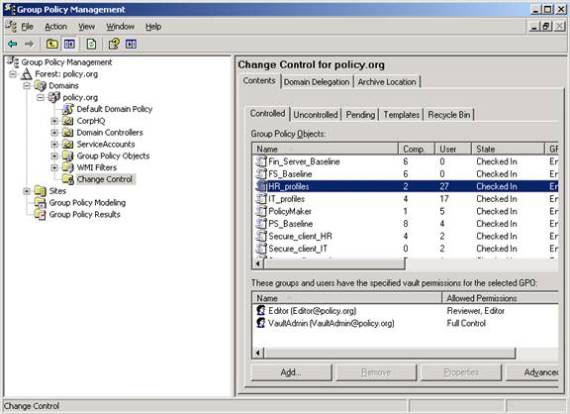
Figure 3: AGPM delegation management options
Within AGPM you can delegate the tasks to anyone in the company. The AGPM interface provides a perfect solution for you to allow an administrator to edit a GPO, but those edits won’t affect production computers until another administrator, with deployment delegation, approves the changes.
Summary
With these three solutions you have almost everything you would ever need for delegating responsibilities and tasks for AD and GPO objects. The ADUC provides an excellent solution for AD related tasks, outside of GPO management. GPO management can be done within both the GPMC and AGPM. The combination of both of the tools provides an excellent solution for complete GPO management. Once you have your delegations established in these tools, you will have a more efficient management model and you will be ensured that administrators can alter only what you have specified.



