iOS security has been in the news a lot lately, especially with the latest OS update. It appears that the negative attention the company is attracting now is self-inflicted due to flawed Apple password policies. The issue seems, at least currently, with how the iOS device prompts users to input passwords.
In a blog post entitled “iOS Privacy: steal.password,” mobile app developer Felix Krause ripped into the Apple password prompts, stating that a hacker could ask “users politely, they’ll probably just hand over their credentials, as they’re trained to do so.” What Krause is referring to is the fact that hackers, using a phishing attack, could potentially take advantage of Apple’s frequent popup password prompts. As Felix states:
Users are trained to just enter their Apple ID password whenever iOS prompts you to do so. However, those popups are not only shown on the lock screen, and the home screen, but also inside random apps, e.g. when they want to access iCloud, GameCenter or In-App-Purchases.
The problem lies with the ease that a hacker can utilize an app, just by showing an UIAlertController, to mimic the prompt that asks for Apple password and ID. To prove his point, Krause developed a proof-of-concept attack within the iOS infrastructure that allowed him to mimic, with pinpoint accuracy, the prompts that Apple uses to ask for credentials.
As shown in the below image, there is no discernible difference between the legitimate prompt and the phishing attack:
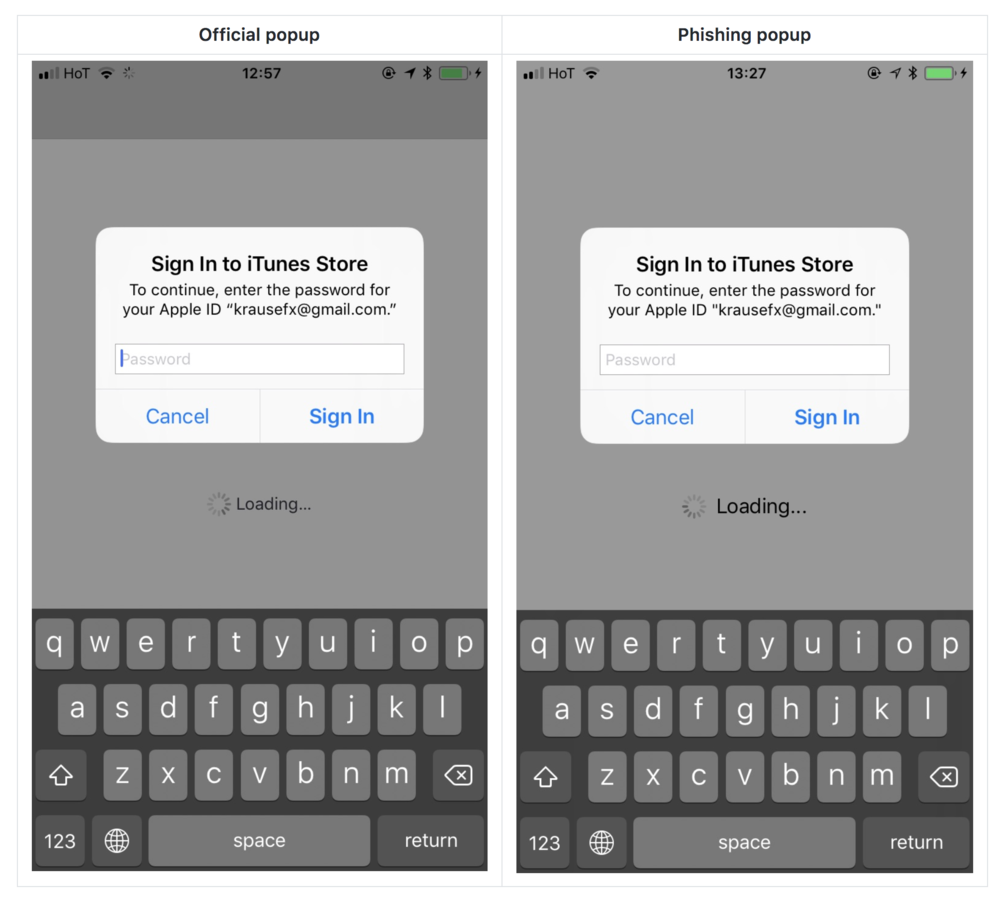
The likelihood of this proof-of-concept attack being used in iOS apps is a high probability. The ease with which Krause was able to engineer this attack is not a fluke, but likely something well known to malicious app developers. Felix points out that, while Apple does a great job of protecting users from phishing attacks, it is very plausible that an attack can take place following the vetting process (much like recent attacks against Google Play apps). Examples of attack methods given included using “a remote configuration tool to enable a feature only after an app is approved by Apple” and, via time-based trigger, “skip running certain code for the first week after submitting the binary, meaning the code will only run once the app is either approved or rejected.”
Felix Krause recommends Apple adopt a policy in which, instead of collecting the credentials via prompt, the user is instead instructed to open the “settings” app. Additionally Krause recommends that users, upon receiving a credential prompt, hit the “home” button. If the popup closes after doing this, it is a phishing attack as “if the dialog and the app are still visible, then it’s a system dialog. The reason for that is that the system dialogs run on a different process, and not as part of any iOS app.”
The moral of the story here is that, no matter how much vetting any company does, malicious apps can and will come for your data. Don’t give them the chance if it can be avoided.
Photo credit: Wikimedia



