In June 2017, news about a massive data leak of close to 200 million American voters, exposing details such as their names, phone numbers, birthdates, phone numbers, and political opinions broke out on the Internet. This time, the data leak was attributed to a simple user error of not using recommended security settings, which left the data exposed on AWS S3, accessible by anyone with an Internet connection. This has been a massive reminder to the global enterprise IT think tank about the risk of IaaS platforms such as AWS. Of course, Amazon has invested millions of dollars into ensuring that its cloud services are secured by military-grade encryption, but a super-powerful cyberattack or a misconfiguration mishap can never be ruled out. The implications for enterprises are loud and clear — IT leaders in general, and data security decision makers in particular, need to understand that they can’t just rely on Amazon for their cloud data and systems security. In this guide, we’ll cover AWS security tips and methods that will help you make your cloud storage more secure than before.

Why do you need to bother about AWS security?
Amazon uses a shared responsibility business service delivery model, where it assumes full responsibility of its cloud systems, physical computers, software setup, connections, and servers. It even includes the responsibility of detecting and diffusing cybersecurity attacks such as intrusions and fraudulent access attempts. However, the responsibility of managing security configurations is entirely on the customer. Any systems and connects made to AWS by a company must be secured by the enterprise on its own. Also, applications that use AWS identity and access management systems (IAM) are governed by the same shared responsibility system.
AWS security tips: Enable CloudTrail
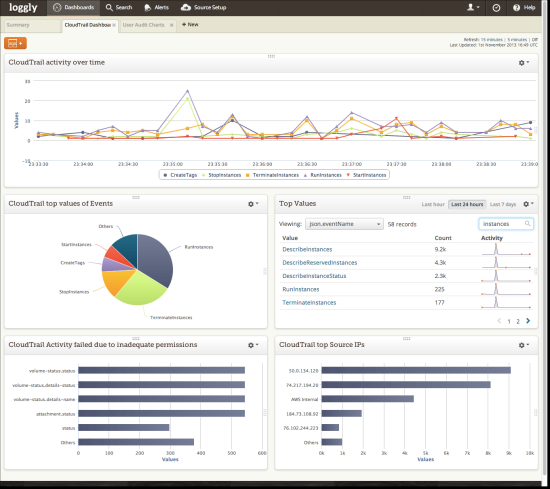
Make sure that CloudTrail is enabled for all AWS services you use. This creates extensive activity logs for all kinds of user activities in AWS services. The major advantage is that this creates a clear audit trail, which can help you uncover potential cyberattacks in progress, and in some cases, can help diffuse attack attempts. Include all services within the scope of CloudTrail, including nongeographic services like CloudFront. Multiregion logging is also worth doing, because if you find activity in logs indicating activity in a geography where you don’t use AWS, it’s a red signal in terms of a potential cyberattack.
Multifactor authentication on root account
Your root account has access to all AWS resources, that’s how critical it is. Multifactor authentication helps add additional layers of protection to weed out possibilities of unauthorized access. A safe practice is to have a secured and dedicated device to receive one-time passwords, instead of linking it to a mobile phone. This dedicated device must also be placed in a restricted environment, with automated alerts to help you detect attempts of theft. When you use a mobile phone device for the one-time passwords, there’s a tangible risk of device theft contributing to compromising the security of your root account’s access.
You can take your AWS security a notch higher by setting up multifactor authentication to delete CloudTrail buckets. This ensures that anybody who’s able to access your AWS account is not able to manipulate the CloudTrail logs to hide their activities.
Strong passwords
No list of AWS security tips is complete unless we also remind you about using strong passwords. Seems like cybersecurity advocates will never get to stop circulating reminders about this well-known yet often ignored practice. Weak passwords are undeniable testimony to security laxity in an enterprise’s data and IT systems management approach. A good practice is to mandate 14 character-long passwords, with at least one upper case character, one number, and one symbol. Password expiry periods anytime longer than 90 days need immediate readjustments. Also, your users must never be able to set the same passwords as before. Ignore these password policy guidelines at your own peril!
Virtual private cloud: A massive security enabler
Amazon virtual private cloud is a virtual network that operates within your enterprise’s AWS account. This approach helps isolate the network from other resources. Then, virtual network is not routed to the Internet by default. Most importantly, you can apply a lot of access control mechanisms using security groups to minimize potential attack surface, thus keeping your AWS experience much secure.
Bastion host for secure shell security
Consider implementing a bastion host to get access to your Linux instances that are deployed in a private VPC subnet. This helps you by avoiding the need of exposing SSH service of the Linux instances, and also helps in centralization of SSH access to all systems. On the whole, this delivers advantages around minimization of attack surface, access control, monitoring, and auditing of SSH access.
More options to leverage and secure AWS
Apart from the AWS security tips above, here are some more:
- Access to most commonly used ports must be restricted; these ports include MSSQL, FTP, SMTP, DNS, MongoDB, and CIFS, among others.
- Never allow the use of access keys for root accounts because that’s too much a risk given how any unauthorized access could effectively paralyze the operations of your enterprise.
- Unused, abandoned, and dysfunctional accounts increase the attack surface area for your AWS account; make sure such accounts are automatically expired after a set period of inactivity (such as 90 days).
- Turn on access logging for S3 buckets to make sure that tracking access requests becomes easier; this can help avoid security breaches, and can also help combat one once it happens.
- Restrict access on EC2 security groups to avoid cyberattacks such as DDoS, brute force, and man in the middle.
Ultimately, it’s your responsibility
AWS has elevated its status as the cloud storage and computing backbone that’s helping global business machinery stay strong. If your enterprise depends on AWS for supporting critical applications, you just can’t afford any security lapses around the same. Adopt the AWS security tips, tricks, and best practices suggested in this guide and bolster the security of your company’s AWS account. Remember, ultimately, it’s your responsibility, not Amazon’s.



