We belong to an era of technology where most business transactions and communications take place over the Internet. Considering the fact that more than 250 billion emails are being sent a day by more than 7 billion active internet users, it is quite evident that the Internet plays a significant role in our lives. With so many people using the Internet, there is an exponentially increasing threat to data that is transferred over the Internet. To overcome these aforementioned threats and prevent any unauthorised access to the content, there are some special protocols implemented in the transport layer of a network system to safeguard online data.
Transport layer security (TLS) is the successor of the secure socket layer (SSL) and is one of the world’s most powerful public key cryptographic systems to secure web browsing sessions. TLS/SSL primarily aims at providing privacy and data integrity between two parties connected over the Internet. Moreover, they secure a very wide range of business applications, including client-to-server, server-to-server, emails, virtual networking, and various other networking based applications.
Wondering how these protocols safeguard your valuable online data?
TLS/SSL protocols operate from the transport layer in a network architecture and does the job of providing security to the content transferred over the Internet. These protocols ensure that the data is transferred from sender to receiver without any intruder’s interference. However, users have to be very careful in implementing TLS/SSL protocols to ensure the safety of their data.

Best practices in TLS and SSL (what to do)
Using secure cookie flags
Cookies are made to store small amounts of valuable data which is sent from the server to the client’s web browser to track and store user’s browsing information. During these transactions, cookies are subjected to attacks and are subjected to theft by intruders through packet sniffing, cross-site scripting, sessions hijacking, and more. To avoid these aforementioned threats, users are advised to enable the ‘secure flag’ which restricts a cookie transfer only through a secure TLS connection, safeguarding them from all sorts of intruder attacks.
Always prefer using HTTPS links
HTTP and HTTPS are seemingly similar yet a different set of protocols. Hypertext transfer protocol secure (HTTPS) is an encrypted version of HTTP which is connected through the transport layer. In HTTPS, all the connected computers agree to a common code, which usually encrypts data during information transfer over the Internet. When information reaches the destination, it is decrypted, and thus, the required information is retrieved without any valuable data being accessed by intruders or hackers.

Certificate management
A digital certificate is an important tool in TLS/SSL which secures information transfer through the Internet. A digital certificate is referred to as an electronic passport that allows system to make a transaction securely using public key infrastructure. These digital certificates are issued by official authorities. A digital certificate includes the serial number, name of the certificate holder, expiration date, and a copy of the owner’s public key. Since these certificates come with an expiry date, it is the user’s duty to keep checking the validity of these certificates and to revoke them in a timely manner to avoid cyber-attacks.
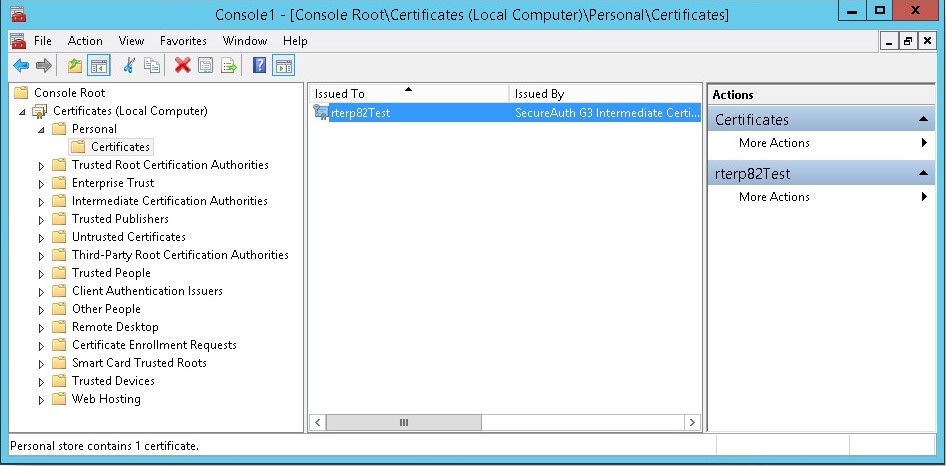
Digital certificates which are issued by the user and not by certificate authorities are known as self-signed certificates. Anyone can create these certificates and these certificates can also encrypt the data to ensure data integrity. However, self-signed digital certificates are relatively easy to break in. Moreover, these certificates often result in authentication errors and are made using less secure hash and cipher technologies, making then vulnerable to attacks.
Since these digital certificates play a vital role in securing transactions, it is the responsibility of user to manage them properly.
Use of TLS/SSL on all login/authentication pages
In any web application or an online transaction, a login/authentication page acts as a gateway to enter a system. Therefore, these authentication pages have to be safeguarded using the TLS standards. These login and authentication pages have to be secured before, during, and after an authenticated login. In case, these pages are not secured through TLS/SSL, intruders and attackers can easily enter a system which can result in the loss of data. An intruder who enters the system through these authentication pages might get access to the entire system’s valuable data in an unencrypted form, resulting in a severe loss.
Keep sensitive data out of URLs
HTTP is designed in such a way that it enables the users to communicate in a request/response pattern as seen in a client-server protocol. When designing a web page, the developer has to be very cautious when implementing GET/POST methods.
Sensitive data such as passwords and other authentication details must never be passed through the GET method. The GET method can expose sensitive data to outside world in the URL, aiding intruders to attack the system.
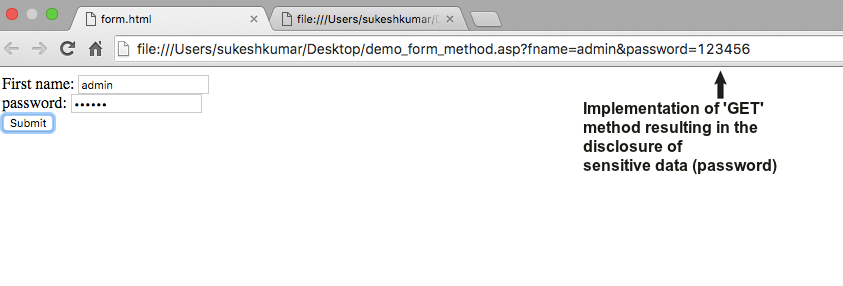
Instead, the POST method is a more suitable alternative to the GET method when submitting sensitive data over the Internet. POST requests cannot be cached and they do not remain in a user’s browsing history, making the data safe and secure.
Implement TLS on all networks dealing with sensitive data
Intruders might not always be outsiders. There are various occasions where sensitive data is stolen from within an organisation. Most network administrators implement TLS standards on external networks, neglecting the security of internal networks. Internal networks are usually restricted to authorised employees. Thus, breaking into an individual’s account is a simple task for intruders when compared to attacking the entire system externally. Therefore, both organisation and its employees must follow the TLS/SSL security protocols to avoid intruder’s attacks.
In various occasions, users falsely believe that implementing TLS/SSL security standards on their websites/transactions will secure them. However, it’s not always the case. Users have to be very cautious to keep their data secure. Even after all security measures of TLS/SSL, users commit common mistakes that negate the effectiveness of TLS and SSL, making data vulnerable, and thus, paving a way for cyber data-thefts.
Worst practices in TLS/SSL (What not to do)
Redirecting to an insecure page
Most of us might have come across this situation at least once during our browsing sessions. When we click on a link in a web page, the browser pops up an alert message saying the site is not trusted, do you wish to continue? Often, we neglect the warning and proceed to that insecure page. This is an open invitation for various kinds of phishing pages and several other sorts of abuses.

Mixing non-TLS content with TLS content
Having an HTTPS link to the webpage doesn’t always means that it is secure. For example, if a HTTPS-secured page contains even a single frame or an image or any other minor element which is not HTTP-secure, that particular website cannot be considered secure. Most of the commonly-used browsers don’t warn the users regarding insecure website elements, so it’s the duty of an individual to inspect each element very carefully before implementing secure information on a web page.
Attaching your private key along with the data
Your private key is a user/account specific security key that is meant to decrypt encrypted data and vice versa. Before any message or data is passed through the Internet, it is often encrypted and sent to avoid intruders’ intervention. This encrypted data can be decrypted using the public and private keys which are restricted only to the sender and receiver. The public key is attached to data and is transferred along with it, and is accessible to everyone. However, a private key is the ultimate private tool to decrypt the content. Users often attach their private key along with the data, making it vulnerable to external attacks.
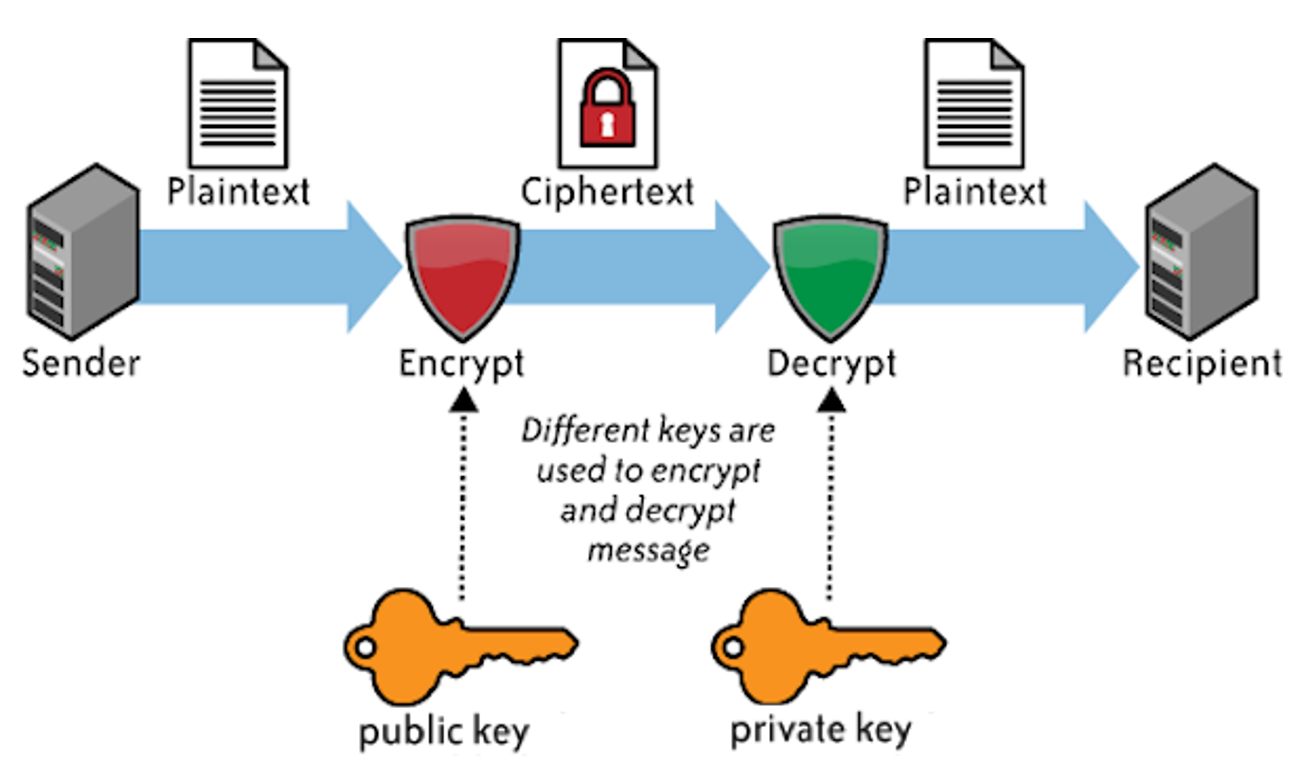
Negligence or improper use of these valuable security assets can result in loss of data integrity and thus might lead to various other complications.
The world of TLS/SSL might be hard to understand. However, understanding them properly is crucial to data integrity, safety, and privacy of your network. Therefore, be careful with how you use these protocols, because at the end of the day, our best practices are driven by goals to keep your network safe and secure.



