A business email compromise (BEC) campaign is quite the opposite of what we see in terms of popular cyberattacks. The attacks rely heavily on social engineering rather than pure technical knowledge, and the victims are more than willing targets. Typically business email compromise attacks focus on CEOs in spear-phishing attacks, but a current campaign originating in West Africa is deviating from this focus.
In a report from Ronnie Tokazowski of the security firm Flashpoint it was noted how, between March 28, 2017 and August 8, 2017, mass phishing campaigns were carried out via malicious PDFs that sought email credentials. The targets of the campaign were in numerous industries, which Tokazowski notes in the following statement:
These malicious PDFs targeted a range of verticals, including universities, software and technology companies, retailers, engineering organizations, real estate firms, and churches, with the goal of harvesting user credentials.
The attack is fairly rudimentary when it comes to the actual mechanics of phishing. The potential victim targeted by the BEC campaign receives an email that is obviously official looking enough that they might be tempted to click on the attached PDF. Upon opening the document, the user is met with the below prompt:

Upon clicking the link, the user is redirected to a page (pictured below) that asks for login credentials for the targeted organization in order to download the supposed “secure online document” from the original prompt:
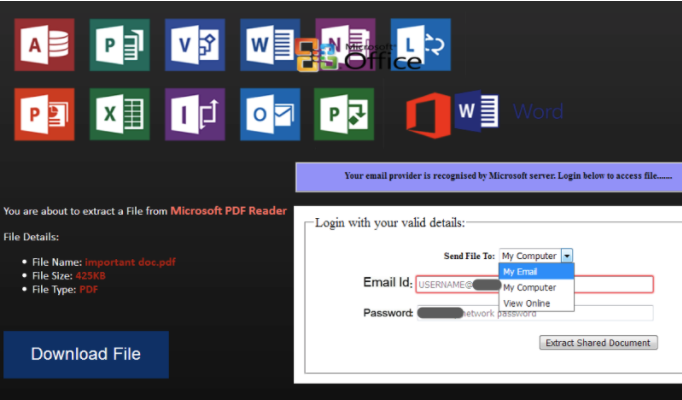
With valid credentials, the attackers now have an “in” to their particular target. The data is valuable for anything from privilege escalation to gaining access to sensitive data via email monitoring. The possibilities are truly endless when login credentials are more or less handed over to you with the victim being none the wiser.
It may seem a tad ridiculous to some, especially in the InfoSec world, that anybody would fall for this type of attack, but the reality is that many do. The Flashpoint report notes that, “while BEC actors… are broadly considered among the lowest-skilled cyber threat actors, they have been responsible for more than $5 billion in fraud in the last three years.”
Phishing scams like BEC aren’t going away any time soon, and the attacks are getting a broader reach in terms of targets seemingly by the day. Educate yourself on this so that you don’t accidentally hand off your login to black hat hackers.
Photo credit: Shutterstock



