The saga of Cerber ransomware has been an extremely complex one. First noticed by security researchers around March 2016, the ransomware has developed into multiple versions (it’s now at version 5.0), and has gained popularity on a global scale with hackers. As is with many kinds of ransomware, the Cerber strain originates in malvertising, compromised web pages, and also email campaigns. If you are unlucky enough to become infected by Cerber, read below to see what happens in your computer and also how you can possibly fight it.
Once Cerber invades a system, it will first see what country the device is being used in, according to Bleeping Computer’s Lawrence Abrams. This is perhaps a window into the attackers’ mindset or origin, but, regardless, if you are in the nations of Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, or Uzbekistan, Cerber will promptly terminate.
If you do not live in these nations, the ransomware will begin encrypting based on specific file extensions (seen in the extensive list below):
Upon infection, you are subjected to the standard modus operandi of ransomware. By this I mean that once your machine is fully infected and files are encrypted, you are met with a message that gives instructions on how to decrypt. The ransom is a demand in the hackers’ favorite currency of bitcoins with the promise you will gain access to your files once you pay the fee. The most recent notice following infection can be seen below:

Depending on the version, other items on your computer may be encrypted. For instance, in the current version of Cerber, researcher BloodDolly states that Cerber will “skip 640 bytes, compared to 512 bytes in previous versions, when encrypting a file and … any file that is smaller than 2,560 bytes will not be encrypted.”
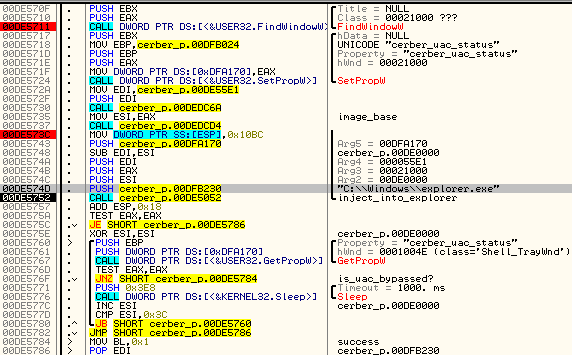
The havoc that Cerber creates is not just extended to file encryption, as MalwareBytes researchers report that it will “bypass Windows User Account Controll (UAC) and deploy itself with elevated privileges.” This process is shown below:
Depending on the version, there are ways to fight Cerber. The main way is attempting manual removal. Unfortunately, this process is delicate and could destroy your machine if you are not careful. If you wish to attempt this, which frankly is risky and I advise against, I recommend this article from the great team at VirusResearch.org.
The other option is twofold. Firstly utilizing, in safe mode, a malware removal program. Many major companies are aware of this ransomware and have configured their programs to, at the very least, remove the actual malware. The problem is this will not decrypt the files. Your only option in this case is likely waiting for decryption software. At the moment any decryption software only works on Cerber versions 1 and 2. Anything that decrypts using version 3 and above does not currently exist and, unfortunately, it leaves you high and dry if you did not back up your files via external hard drive.
The best way to defend against Cerber is to be diligent in noticing malicious links. You may not have any other options outside of this based on what we know about the ransomware.
Photo credit: Pixabay, Bleeping Computer, MalwareBytes



