In a December 21 vulnerability report, Cisco warned users of a critical flaw in its CloudCenter Orchestrator cloud-management platform. The vulnerability, CVE-2016-9223, is related to a misconfiguration in the platform that allows access outside of the CloudCenter Orchestrator. The main issue, and why this vulnerability is considered critical, is that an attacker can leverage this outside access to eventually gain root privileges on the program.
As stated in the Cisco report, the vulnerability affects “all releases of Cisco CloudCenter Orchestrator (CCO) deployments where the Docker Engine TCP port 2375 is open on the system and bound to local address 0.0.0.0 (any interface).” To check for this particular vulnerability, an administrator should open CCO and enter the command “netstat -ant | grep 2375.” As seen in the screencap below, the Cisco vulnerability report shows what an admin then will see if the flaw exists in their CCO version:

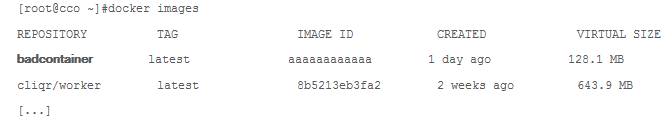
Additionally, as you will see in the subsequent screencap, using the docker images command can reveal malicious content caused by the flaw:
There are a few ways to handle this critical flaw. The first recommendation that Cisco gives to administrators is to bind the Docker Engine port to local host 127.0.0.1 by following these steps:
1) Issue the su command to obtain sudo privileges
2) Enter the system directory using the following command: cd /etc/systemd/system/
3) Edit the docker.socket file with your chosen editor and change the ListenStream value to the following: ListenStream=127.0.0.1:237
4) Reload with the systemctl daemon-reload && systemctl restart docker command
Additionally, customers of CloudCenter Orchestrator can install free updates released by Cisco that the company assures will take care of the vulnerability. To properly install the 4.6.2 patch you should make sure that you have upgraded hardware that can handle the memory needed in the patch.
It is recommended that administrators of Cisco CCO take care of this vulnerability as soon as possible. The last thing you need is some malicious hacker gaining access to your network via root privileges.
Photo credit: Cisco, Zengame



