Like many networking platforms Cisco ACI offers the ability to have multiple tenants. A tenant is generally a container that allows you to keep resources isolated. For example I might have tenants for dev and prod or I might have separate tenants for each department in my company. Usually public cloud providers will have a tenant for each of its customers. It’s a security construct that allows you to basically keep things separated.
In this blog I’ll go through creating a tenant using the ACI APIC GUI.
1. Login to the ACI APIC GUI
2. Click on Tenants from the menu bar.
3. Click on Add Tenant from the sub menu bar
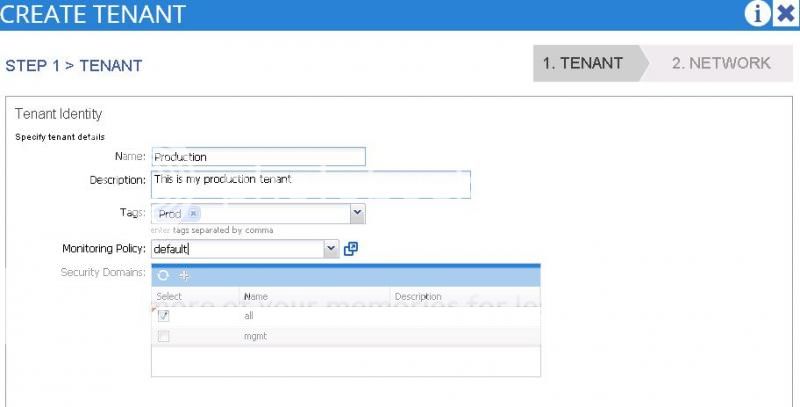
4. in Step 1 of the Add Tenant wizard give it a Name, optional Description, ptional Tag, optional Monitoring Policy, and a Security Domain.
5. We can then click Finish and we’ll have a brand new Tenant which we’ll see up in the sub-menu bar.
As shown in the picture after Step 4 I chose the “all” security domain. “All” is a default security domain. However, I can add other security domains and isolate them even more. These security domains tell me which users have access to that particular tenant. So, if I had created a security domain for Production, given users roles, and attached them to that security domain then I might want to choose my Production security domain instead of “All.”
We can also use this wizard to create a network for this tenant if we click Next instead of Finish, but I’ll save that for the next blog.
Looks simple enough (which is a good thing!!). If you were to implement a tenant for PRODuction and a separate tenant for DEVelopment, what would happen if the DEV team said they wanted temporary access to a PROD resource? Is the tenant construct in APIC set in stone and unpenetrable, or can you link resources if necessary? I would prefer the former but experience tells me the latter will be requested sooner or later.