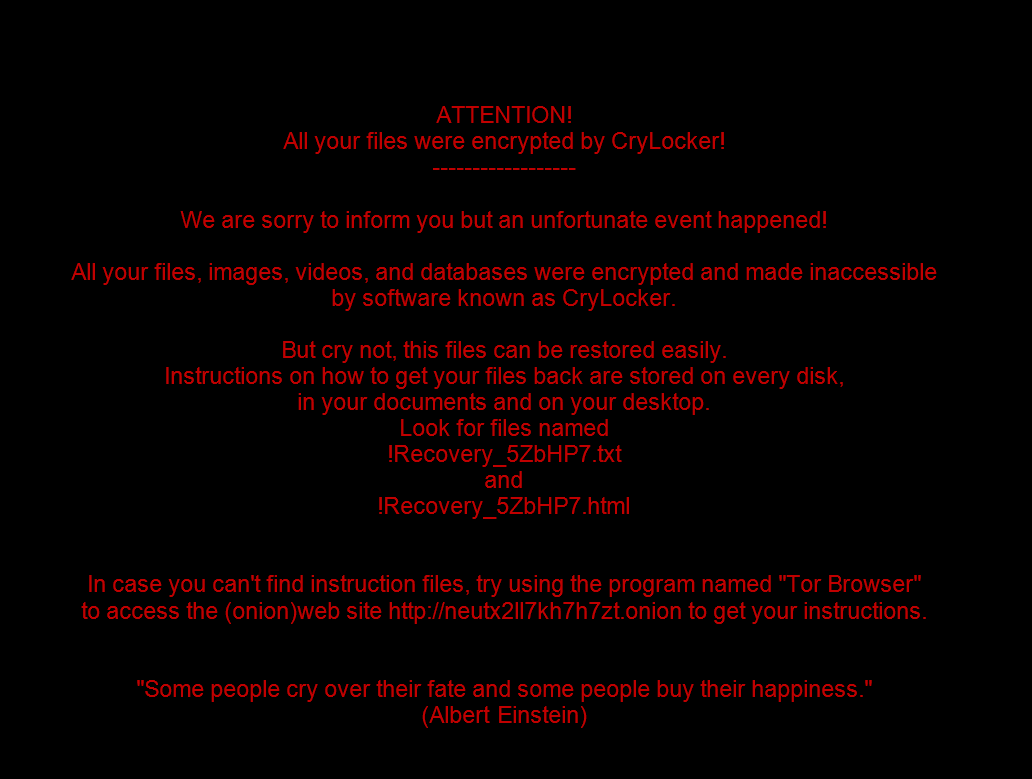
Cyber criminals who employ ransomware usually abide by a rather predictable set of actions. After the victim takes the bait and infects their computer, the payload encrypts their files until a (usually bitcoin) ransom is paid. The newest ransomware to be discovered by security researchers, named CryLocker, is taking the cyber attack to another level. Not only does this ransomware hold the target’s data hostage, but it can also effectively doxx the victim of the attack.
The ransomware was discussed in a report involving security researchers Lawrence Adams, MalwareHunterTeam, and Daniel Gallagher. According to them, CryLocker utilizes UDP to send stolen data about the infected machine and its owner to “4096 different IP addresses… to obfuscate the location of the Command & Control server so that authorities cannot seize it.” Additionally CryLocker proceeds to upload the information to Imgur via a fake PNG file that contains the same encrypted data.
Next comes the doxxing, as the program employs “WlanGetNetworkBssList function to get a list of nearby wireless networks and their SSIDs” through the Google Maps API. The researchers behind the report believe that this info is used to “generate an image of the victim’s location using Google maps. This could then be used to further scare the victims into paying the ransom.” This has not yet been confirmed by the 8,000 or so victims of CryLocker, but considering that ransomware is often based around fear this is quite likely the case.
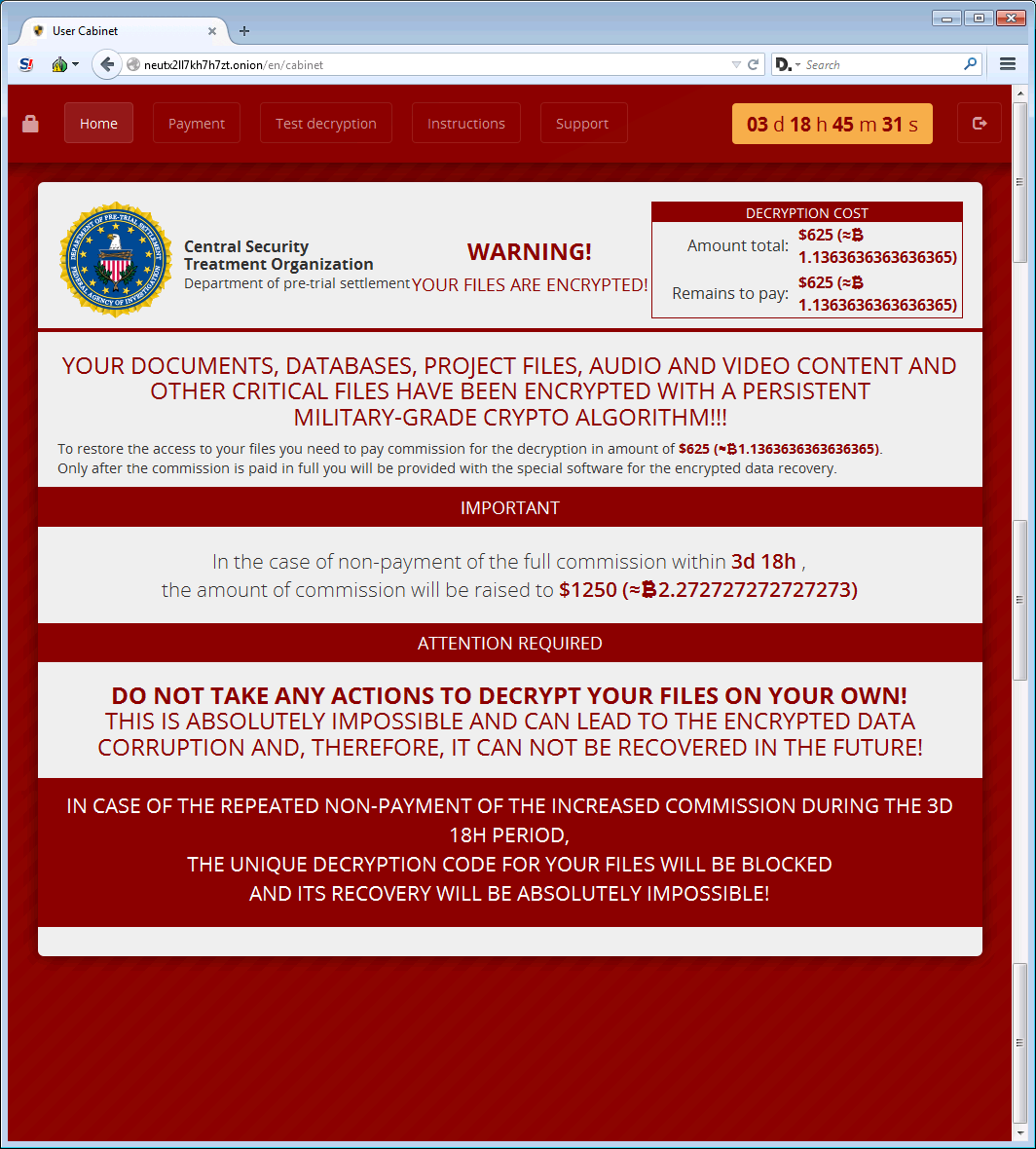
Should the victim choose to pay the 1.1 bitcoin ransom, their only option is through a Tor site named User Cabinet. The page shows a link to the fake organization Central Security Treatment Organization, which utilizes a seemingly official federal government logo. This is a pretty standard tactic for ransomware; scaring people into thinking an official government agency is after them.
Since there is no way to decrypt the files at this time without paying the ransom, the best thing users can do is employ defensive tactics online. Don’t open sketchy links or emails, don’t download anything that comes from an unknown source, and have a strong antivirus and firewall installed. CryLocker could usher in a really nasty age of ransomware infections, as we may see doxxing become the norm in an attempt to get victims to pay up. The best thing researchers can do at this point is figure out ways to remove the malware, decrypt the files, and ultimately chase down the culprits with haste.
Photo credits: Pixabay, Bleeping Computer



