In a report published on August 24, researchers at the cybersecurity firm Proofpoint revealed their findings on a new ransomware that just surfaced in the same month. Dubbed Defray ransomware, it is not currently widespread, instead focusing on specific localized targets, especially in the health-care and education sectors. The name Defray comes from the hostname of the command and control (C&C) server, “defrayable-listings[.]000webhostapp[.]com,” uncovered in the first attack.
Proofpoint noted in its report the nature of the Defray ransomware attack, at least what is known currently as this is more or less brand new to the InfoSec community. Defray ransomware is being distributed in small campaigns that are launched via Microsoft Word document attachments in emails. The emails, at least so far, are all spear-phishing attacks that are tailored at the specific victim, be it an individual or group of individuals on a distribution list. The victims are located in either the United Kingdom or the United States, but as it is with most ransomware, if the campaigns are successful the geographic targets will widen.
Should a user take the bait and execute the ransomware (contained within an .exe file) on the Word document, Defray will begin mass file encryption. Additionally, as Proofpoint noted, a user will be met with the following message via a .txt file:
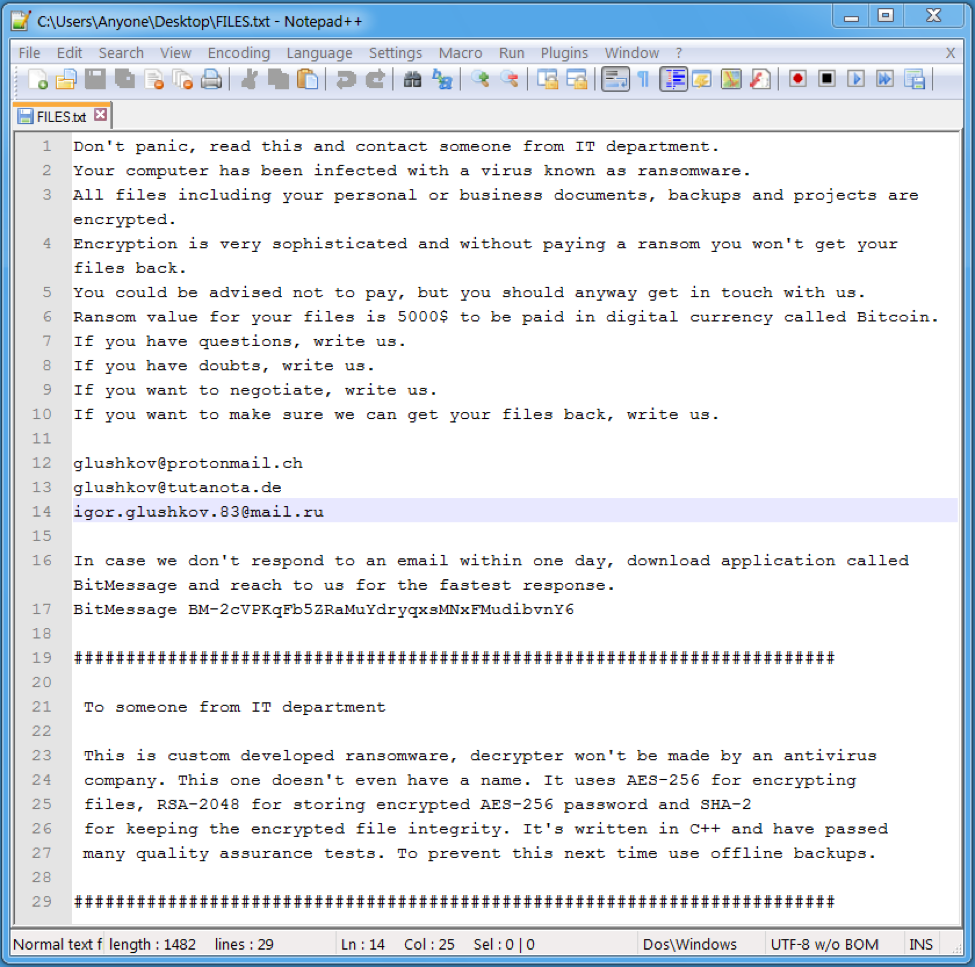
The demand for $5,000 in bitcoin seems steep, but ransomware authors have become more brazen over time. As Proofpoint notes in the report:
The ransom note … follows a recent trend of fairly high ransom demands; in this case, $5,000. However, the actors do provide email addresses so that victims can potentially negotiate a smaller ransom or ask questions, and even go so far as to recommend BitMessage as an alternative for receiving more timely responses. At the same time, they also recommend that organizations maintain offline backups to prevent future infections.
There is still much to study about Defray as it is the “new kid on the block” in the ransomware game. Proofpoint, as well as other researchers, have stated that they will continue to monitor the ransomware to see if the attacks stay small and also if the ransomware becomes purchasable via the Dark Web.
In the meantime, be wary of any email that seems legit but asks you to open file attachments.
Photo credit: Flickr / CafeCredit



