Since Microsoft announced that Group Policy was moving into its end of life phase, I have reluctantly started using Intune as a replacement. It makes sense because it rides along with the Microsoft 365 subscriptions that my clients are using now. We were heavy Group Policy users, so this is going to be a long process. As my clients have moved more and more into the cloud, I’ve been looking for a way to recover some of the automation that we had on-premises. As a consultant, my team and I are supporting many clients each in their own tenant and it just isn’t efficient to have to re-create policies each time. I’d like to be able to create a set of standard ones, have them at the ready and then import them into new client tenants. Recently, I came across a GitHub repository that has really helped me move forward on that goal.
If you have the same goal, then David Falkus is the man you want to know. He only has two GitHub repositories but they are great ones. The one that I’m using is called Microsoft Graph PowerShell Intune Samples. David is also very responsive. There were a couple of errors that I brought to his attention and he responded right away with updates. I’m no developer, so I really appreciate that he has provided these samples. As an IT generalist, I’ve become quite good at modifications to existing scripts and these samples provide an excellent starting point. Here’s a link to David you so can follow him. LinkedIn shows David as a Senior Program Manager at Microsoft.
Licensing requirements
To be able to import and export policies, we must have a small conversation about licensing. As you know you can’t mention the word Microsoft without having to discuss licensing. In this case, you will need to have a Microsoft 365 Business plan or one of the other Office 365 plans that include Intune and Azure AD plan 1 at a minimum. EMS is the usual way to add-in these features in the Office 365 plans but the new Microsoft 365 plans with their emphasis on security include them in the packages.
If the account you are using does not have the proper permission or the tenant does not have the required licensing, you will get a message similar to this one.
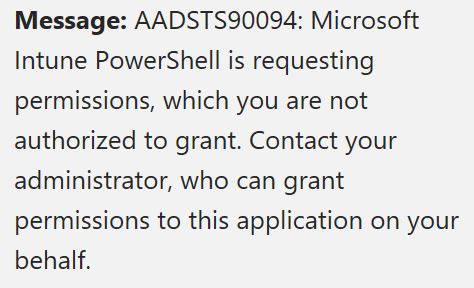
How to download your Intune policies
There are essentially two categories of Intune policies: compliance or configuration. Each requires its own PowerShell script. We’re going to get those PowerShell scripts from here.
You may as well download the scripts for exporting and importing the policies at the same time. Here are the ones that you’ll want to download but do check out the others too. For the purpose of this article download the scripts CompliancePolicy_Export.ps1, CompliancePolicy_Import_FromJSON.ps1 and DeviceConfiguration_Export.ps1, DeviceConfiguration_Import_FromJSON.ps1. Save them to someplace that is easy to reference with a command later. I create a c:\temp folder for this purpose.
Now let’s download our policies. Open Windows PowerShell ISE as administrator. Choose open from the menu, browse to the location where you stored the scripts and open it. As you can see from the screenshot, I renamed mine to make them easier to read.
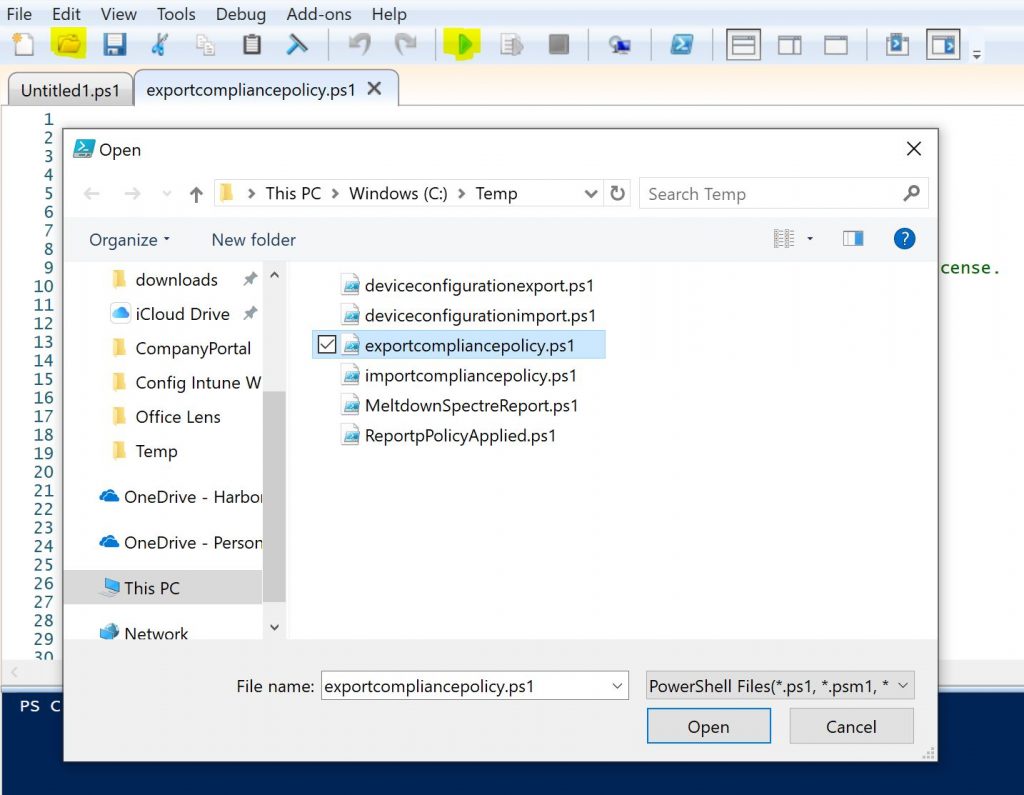
Once you have it loaded, press the green arrow to run the script.
You’ll be immediately asked for the username that you want to authenticate with. Enter the UPN (user principal name), the email address, of an admin account.
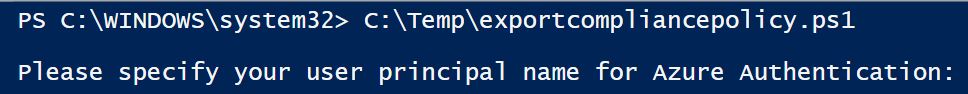
The next thing the script does is add the Azure AD PowerShell module for you. After that, it’s going to ask for the path where you want the export file to go. It is going to export your policies as a .json file. JSON is a JavaScript file. You’ll use this file later to import your policy into the next tenant.
![]()
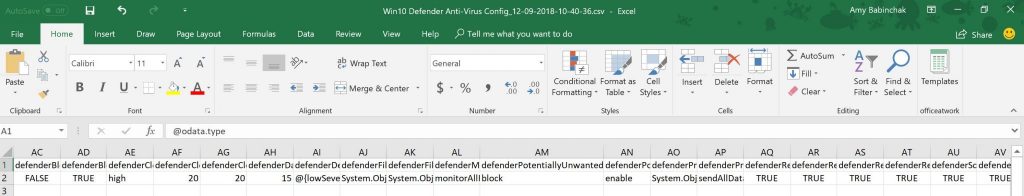
You may or may not have noticed that I’ve been using the plural for policy — policies. This is because the script downloads all of your compliance policies at once. Thankfully it does create separate JSON files for each one of your policies. As you can see in the screenshot below, I have two such policies in this tenant. One is called Win10 Defender On and the other simply iPhone. Both policies have now been downloaded and saved in the folder I specified.
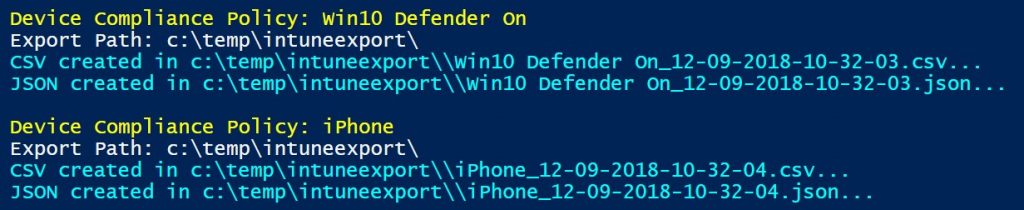
Take a look at the name of those files though. Pretty ugly. I mean useful, sure, as good reference material to help you remember when you downloaded the policy and therefore a reminder to perhaps download a fresh copy sometime in the future to capture your latest policy configuration. But for the purpose of importing just like I did above, I make a copy and then give the copy a simpler name. You’ll thank me later.
Now we need to run through the same procedure to export our configuration policies. The result should again be a JSON file for each of your policies.

What about those CSV files that were also generated? Those are Excel files that contain the settings in your policy. Essentially, it’s the same thing as the JSON file just in a different format. Consider it documentation material.
How to import Intune policies into a different tenant
So now that we have our reference policies exported, we’re ready to import them into a different tenant.
Note: If you’re doing this right away after running the export script, be sure that you’ve disconnected your previous session. Otherwise, you will not get the proper prompts to log into the destination tenant.
Just as above you’ll be immediately asked for the credentials for an admin account. Be sure that you are using one that has permission to Azure AD.
The script will then import the Azure AD module and ask for the name and location of you the JSON file that you’d like to import.
I have two compliance policies that I want to import. This script imports them one at a time, which is fine with me. Upon successful import, you’ll see the details of the settings that were imported.
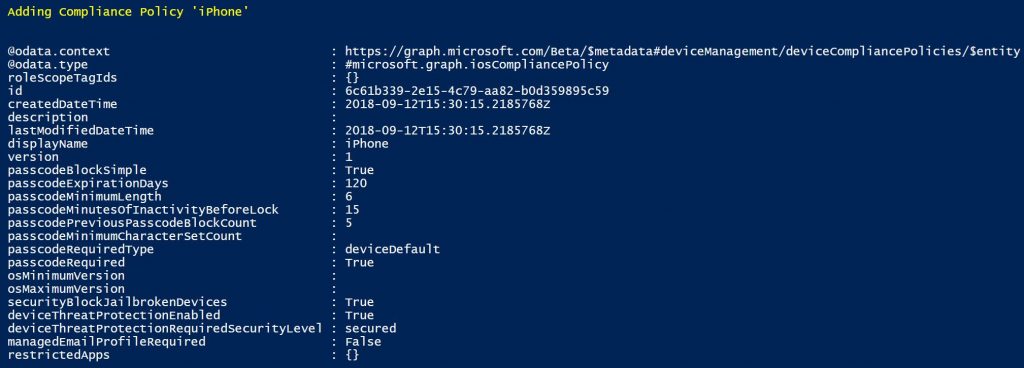
Next to the “:” for each item are the policy settings that were imported. This lets you double check your work. To import the next compliance policy, simply follow the same procedure.
As noted above, I also have a number of device compliance policies that I exported. To import those, I’m going to use the device configuration import script. This time I’m happily still authenticated to the tenant and have the Azure AD module loaded so I can speed through. All I need to do is specify the JSON file that I want to import.

Just like when we imported the compliance policies, the device policies script will screen output a list of the settings from your JSON file that it has imported.

Using the imported policies
The process of importing the policies into a tenant does not put them into production. It merely adds them to the policy list. You have to take the next step of assigning them to the groups that you want them to apply to.
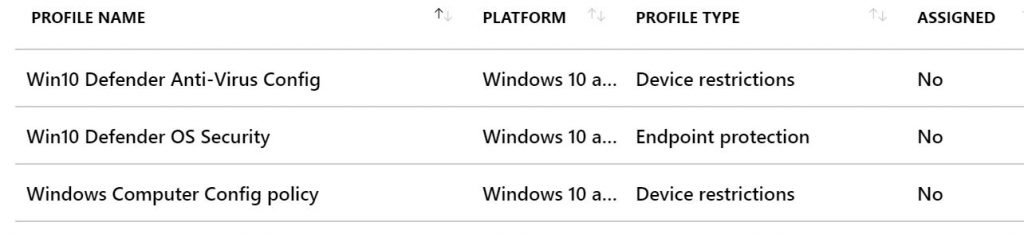
You can assign these policies using another script or you can do it manually. If your clients are like mine, then the groups are often enough unique to the business so at this point I prefer the manual method of assigning each policy to the appropriate group.
If you want to use a script to assign them this one is available from the same repository we’ve been using. You’ll be asked for the name of the group that you want to assign it to.
To assign them manually you’ll use the Intune console, select the policy, press assignments, select the group, and finally save your selection.

If you are new to Intune but familiar with Group Policy it may surprise you to discover that Intune does not distinguish between users and devices. You’ll recall that with Group Policy, a user policy needed to be assigned to a group of users and a computer policy needed to be assigned to groups that contained computers. With Intune, a policy that configures a Windows 10 device can be assigned to a group of users. Azure AD is a different animal and you’ll encounter such differences regularly.
It is also good to know that you can’t create a group here. You need to have first created the group of users or devices that you want to apply your policy to. You can do that either in Intune or Azure AD. The result will be a new group in Azure AD regardless of where you create it from. For those that have been using Intune for a long time, that’s a new thing. Previous to Intune’s move into Azure it very frustratingly had its own groups. That is no more. It’s all Azure AD now!
GitHub to the rescue
I’m very happy to have discovered this GitHub repository. It is prebuilt scripts like this that will make the adoption of Intune a reasonable process for IT admins. The process of using the scripts is straightforward. Caution is taken by not having them become active immediately and you can automate further from here if you like. I hope that one day, scripts like this will move from GitHub into a scripts repository within Azure AD. That would be pretty sweet and would save us a lot of hunting around for the assistance we need to make management of multiple clients happen.
Featured image: Pixabay




I would pump the brakes a bit on issuing the statement that group policy is heading towards its end of life phase. That would be like saying that Active Directory is heading towards its end of life and I don’t think either are nearing that at all.
Definitely helpful, thank you.
Not sure if this is expected behavior or not, but in my case the export script for configuration profiles only exported profiles of type “Custom”, not any of the ones of types Administrative Templates, Wi-Fi, or Endpoint Protection.
Getting multiple errors when running the script. Expected behaviour?
The ampersand (&) character is not allowed. The & operator is reserved for future use; wrap
an ampersand in double quotation marks (“&”) to pass it as part of a string.
At C:\Users\blablabla\Desktop\Scripts\IntuneDeviceConfiguration_Export.ps1:178 char:190
+ … ata-ga-click=”(Logged out) Header, go to Features”>Features <span cla …
+ ~
The '→Customer stories <span cla .
Looks like some characters were changed by conversion to HTML. Change those back to acsii and it should work fine.
Excellent article! Thank you, Amy!
As Anon mentioned, this isn’t exporting all the policies, unfortunate.
I’ve found that the script, as is, will not export “Administrative Template” policies. I’ve amended the script to include them, but the json for said policies are just blank. None of the data from the policy is actually exported except for the date of creation and policy id. Is there a possible fix for this?