The world of IT security, since its very early stages, has never faced a shortage of cyberattacks. Last year witnessed some of the newest, most advanced, and deadliest cyberattacks and breaches in history. The growth of new malware and the rise of ransomware and phishing have collectively disrupted the way the businesses and organizations work. Malware and cyberthreats are advancing at an unprecedented pace and attackers are evolving their methods and techniques to create advanced malware. One such new strain of malware is fileless malware, which now encompasses approximately 15 percent of known cyberattacks. Various industries including banking, telecoms, government organizations, and IT enterprises were victimized by fileless malware in 2017.
What is a fileless malware?
Fileless malware, as the name suggests, is a type of cyberattack that doesn’t use any files in the process. Fileless attacks are also referred as non-malware attacks as these cannot be detected by most traditional antivirus solutions.
An undetectable threat
Even the most legitimate and secure operating systems and applications have vulnerabilities that can be exploited by attackers. And the irony here is that these loopholes often aren’t known until the damage has already been done. Fileless malware is also created on a similar basis and is typically unleashed using PowerShell scripts.

Unlike most of malware, these fileless infections don’t place any payload files on the hard drive of the system. Instead, the malware code resides purely in the memory components of the system such as the RAM or the registers without leaving a trace on the machine’s file systems. As a result, traditional antivirus products cannot identify this attack, and without any measures, the hackers can cause all sorts of damage to the system.
How does it work?
There are various ways of being hit by a fileless attack. Irrespective of the mode of intrusion, the working of this malware is the same. Here is a general scenario, which elucidates the working of fileless malware attack.
When a user clicks or opens a malicious link or visits a compromised website through a browser, the fileless malware lands into the system’s memory such as RAM through faulty Flash players or any other browser plugin enabled to run the scripts. Flash is one of the most common attack vectors due to its large number of vulnerabilities.
Once the malware lands into the memory of the system, it can take control of the native administrator tools and scripting languages such as PowerShell or netsh.exe using the administrative access over the system. Once this has been done, the attackers can have complete access to all your confidential data and can demand a hefty ransom in order to give you back the access to the data.
What are its effects?
Fileless malware possesses various properties and characteristics that make it unique among other malware or cyberattacks. They are stealthier, as they have the ability to avoid being detected by security products. They reside in the system’s memory, they take down the system’s primary scripting language, and execute their own commands with admin access. This can not only grant the attackers access into the systems but can also take down the entire system and its data. If fileless malware is provided with encrypting codes, they can also encrypt the user’s data leading to the ransomware. Although the memory in the system gets flushed when switched off, they have the ability to reside in the system for the longest possible duration, giving them the persistence needed to do the damage.
Avoiding fileless malware infections
So how do we avoid or fight against something that remains untraceable? Here are some of the most effective ways of detecting and avoiding fileless malware infections, according to security experts.
Behavioral analysis
While most endpoint security measures such as antivirus fail to detect fileless viruses, experts suggest that fileless malware can be tracked down on the basis of system behavior. Since the malware resides in the primary memory of the system, it can hinder the regular functioning of the system, which might result in reduced performance or unresponsiveness of the system. Users need to analyze these behavioral deviations and significant changes in the system’s usual functioning to detect this malware.
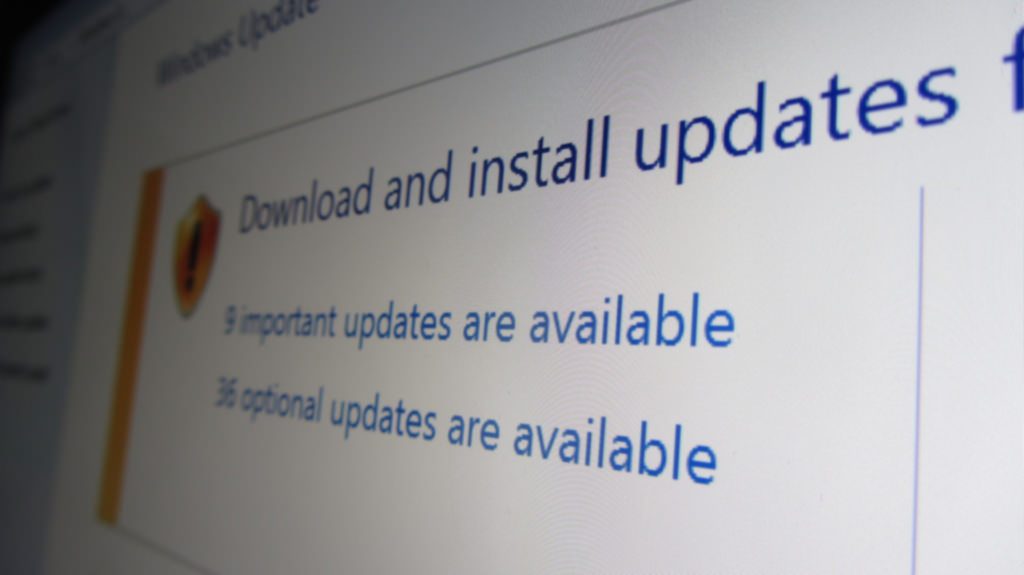
Stay updated, never overlook security updates
Almost all the software solutions and application vendors provide timely updates to improve the performance and increase the security of their products. However, we, the end users, often overlook these updates. Irrespective of the type of cyberattack, faulty or outdated software serves as one of the easiest means for attackers to intrude into the systems. As mentioned above, fileless malware creeps into the system typically through faulty browser plugins and Flash players. Therefore, it is absolutely essential to stay updated and keep all the software and applications in your system updated.
Restrict running unnecessary scripting languages
Fileless malware carries functions through scripting languages and other management frameworks that are native to the operating systems. In most of these attacks, PowerShell or Windows Management Instrumentation (WMI) frameworks are utilized as a medium to run the harmful scripts, which takes down the system. Therefore, disable these default scripting modes when not in use to curb the possibilities of fileless cyberattacks.
Strengthen the firewall to control the network traffic
Firewalls play a major role in intrusion prevention and blocking connections to unsecured sites. Most fileless malware intrudes into the system through phishing or by accessing harmful sites. Firewalls need to be properly set up so that the network traffic is effectively controlled.
In addition to the measures above, there are several other essentials such as the use of advanced endpoint security, proper role and network monitoring, whitelisting applications, and more, which can help fight back against these cyberattacks.



