Back in September 2019, Microsoft acquired the Semmle code analysis platform. Since then, they have worked hard to build it into GitHub in the form of code scanning, a GitHub security feature that developers can use to analyze the code in a GitHub repository to identify possible security vulnerabilities and coding errors. This code scanning feature is available in public repositories on GitHub, and it is also available in private repositories owned by organizations provided they have an Advanced Security license.
GitHub code scans can be scheduled to run on specific days and at specific times. Alternatively, you can configure repositories to trigger scans when a specific event occurs, such as when a push has occurred. When a code scan identifies a potential vulnerability or error in your code, an alert is displayed in the GitHub repository. Then once you have fixed the coding problem that triggered the alert, GitHub automatically closes the alert. To learn how to enable code scanning for a repository, see this page on the GitHub docs site.
The code scanning mechanism built into GitHub is also extensible and comes with a collection of third-party add-ons. One of these add-ons was developed by 42Crunch, and it adds the capability of performing REST API static analysis on code in a GitHub repository. This enables you to get your APIs analyzed for security flaws on each code change in the repository or code submission and to see any issues identified right in the GitHub security center. All issues identified with this add-on come with a list of relevant 42Crunch knowledge base articles, which allows you to see where the flaw is in your code, read about the potential exploit scenario, and learn 42Crunch’s recommendations for remediation.
Since APIs drive most modern applications being developed today, the transition underway towards ubiquitous use of microservices, mobile applications, and cloud-native applications has led to an enormous proliferation of APIs. Formerly, most enterprise development focused on building components of monolithic applications communicating within a single server; now, organizations typically have a plethora of standalone APIs talking to each other over the network. This change in approach to writing enterprise apps has the side effect of significantly expanding the attack surface. This has led to an increase in API attacks due to new vulnerabilities being discovered almost weekly in popular APIs used for developing enterprise apps. In fact, the research and advisory firm Gartner has predicted that within two years, APIs will likely become the most common attack vector used for attempting to exploit coding vulnerabilities in enterprise services and apps.
As someone who works in the IT field, this worrisome trend concerns me, and I’m sure it worries you too. Fortunately, however, 42Crunch’s REST API Static Security Testing tool, which is available as a GitHub Action, can help you close many of those vulnerabilities to keep your code secure. Using this GitHub Action (there are many more you should check out as well in the GitHub Marketplace) allows you to discover any REST APIs in your GitHub repository and audit each API using more than 200 security checks provided by 42Crunch that cover industry best practices for authentication, authorization, transport, and data validation. The resulting audit is then used to analyze any vulnerabilities discovered and presents you with a prioritized alert list you can use to take steps to address these vulnerabilities. And finally, it enables you enforce API security by establishing criteria for your CI/CD workflows and automated pull request checks.
Looking at REST API Static Security Testing at work
Since I wanted to learn more about 42Crunch’s REST API Static Security Testing tool, I reached out to Dmitry Sotnikov, the Chief Product Officer at 42Crunch. Dmitry graciously obliged my request for more info by demonstrating for me some of the capabilities of their REST API Static Security Testing tool. For the benefit of those of you who have similar concerns to mine about the security of their API-driven modern apps, here are several screen captures from my conversation with Dmitry, along with some descriptive comments he has provided to explain what we can see in them:
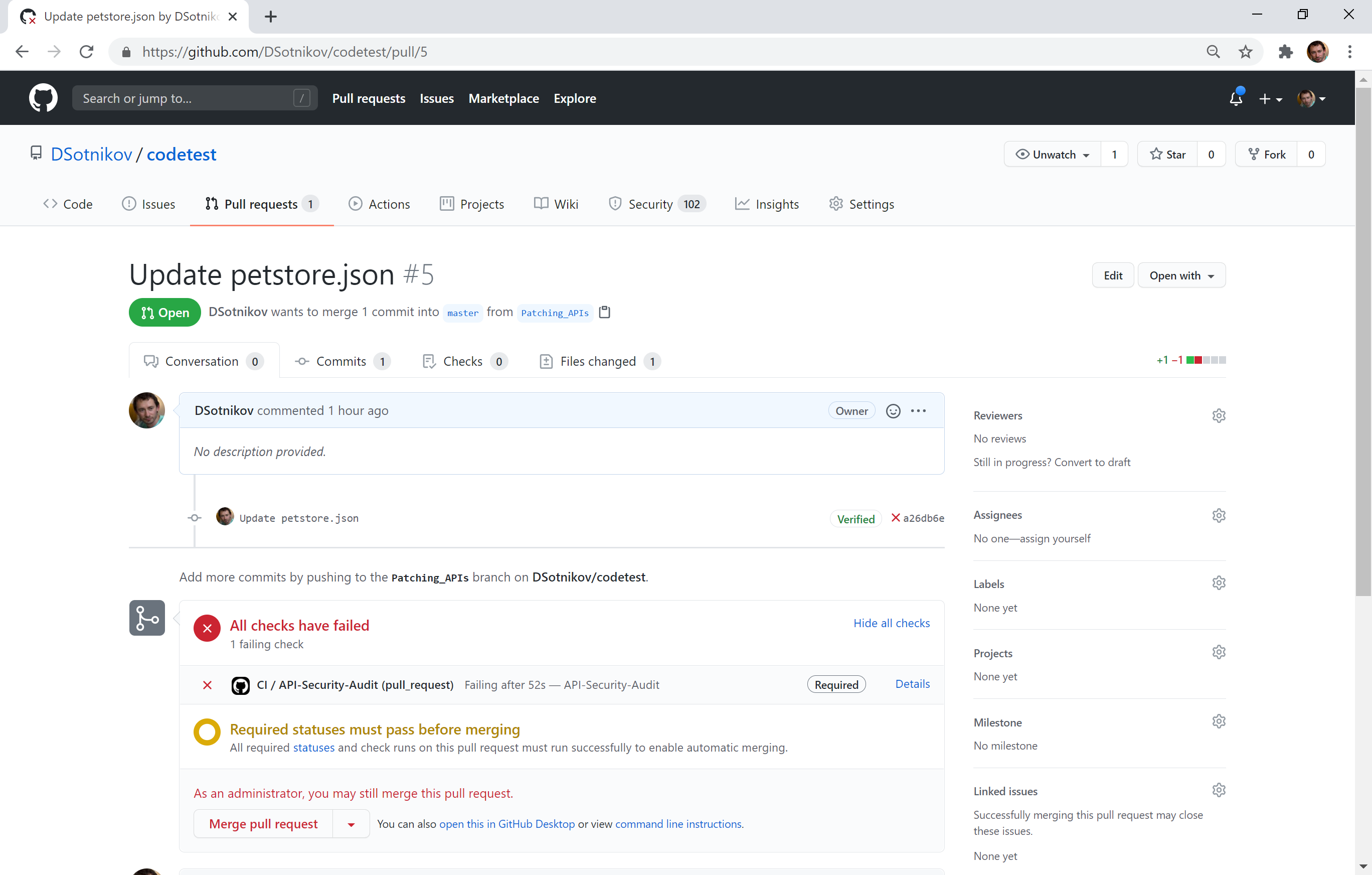
Dmitry says that “This first figure shown above illustrates how companies can use the 42Crunch Action to make GitHub run security checks for REST APIs in their repositories. The screenshot shows how a code change that negatively affected the security of the APIs got blocked by an automated Pull Request review.”
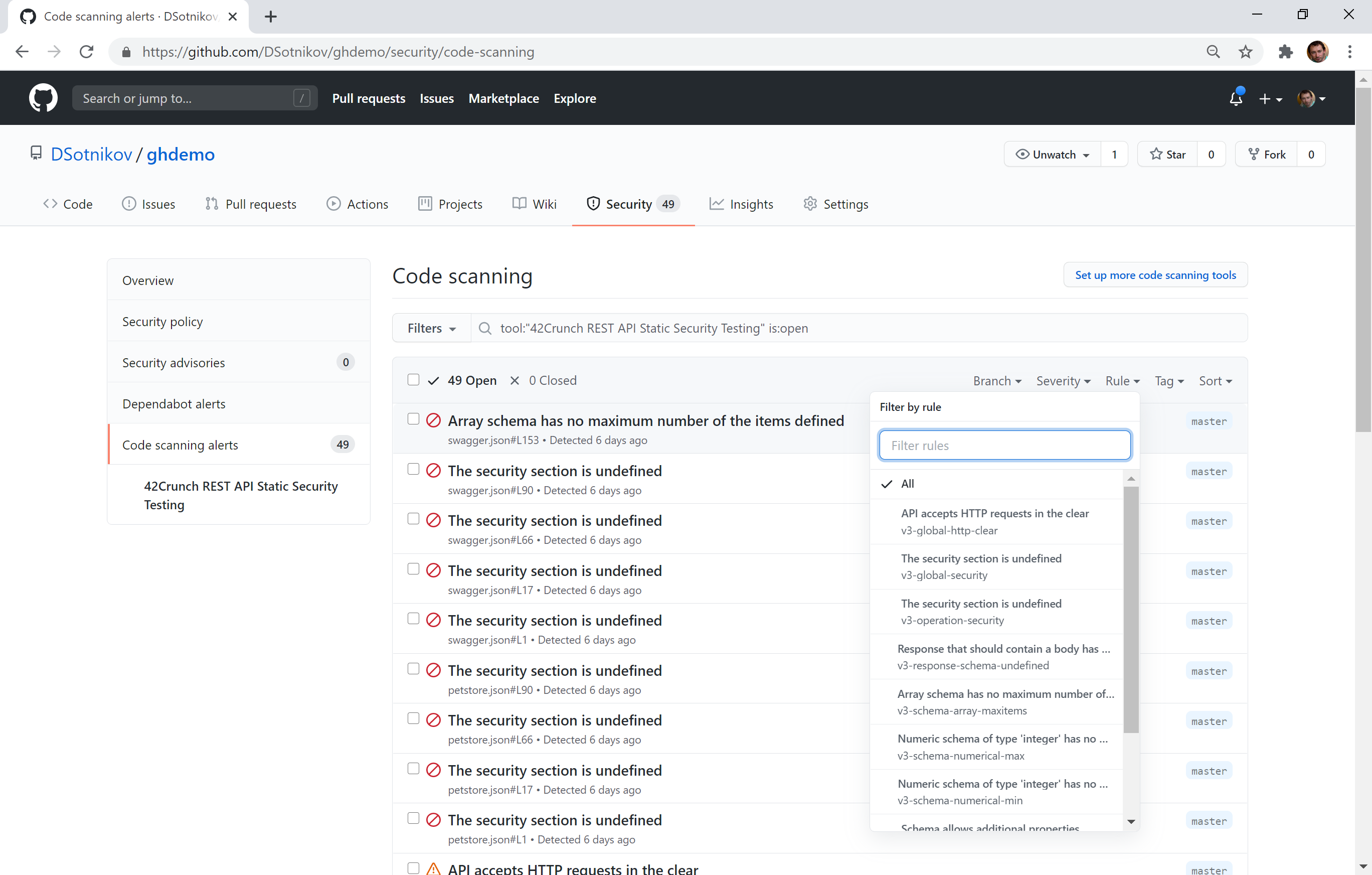
“Figure 2, which is shown next above,” says Dmitry, “displays all of the API security issues found within the repository get reported on GitHub’s Security tab. The issues that are displayed can then be filtered if desired by branch, severity, rules, or tags. The security issues that have been identified can then be resolved manually by the developer’s actions or get automatically resolved when the vulnerability gets fixed in the API itself.”
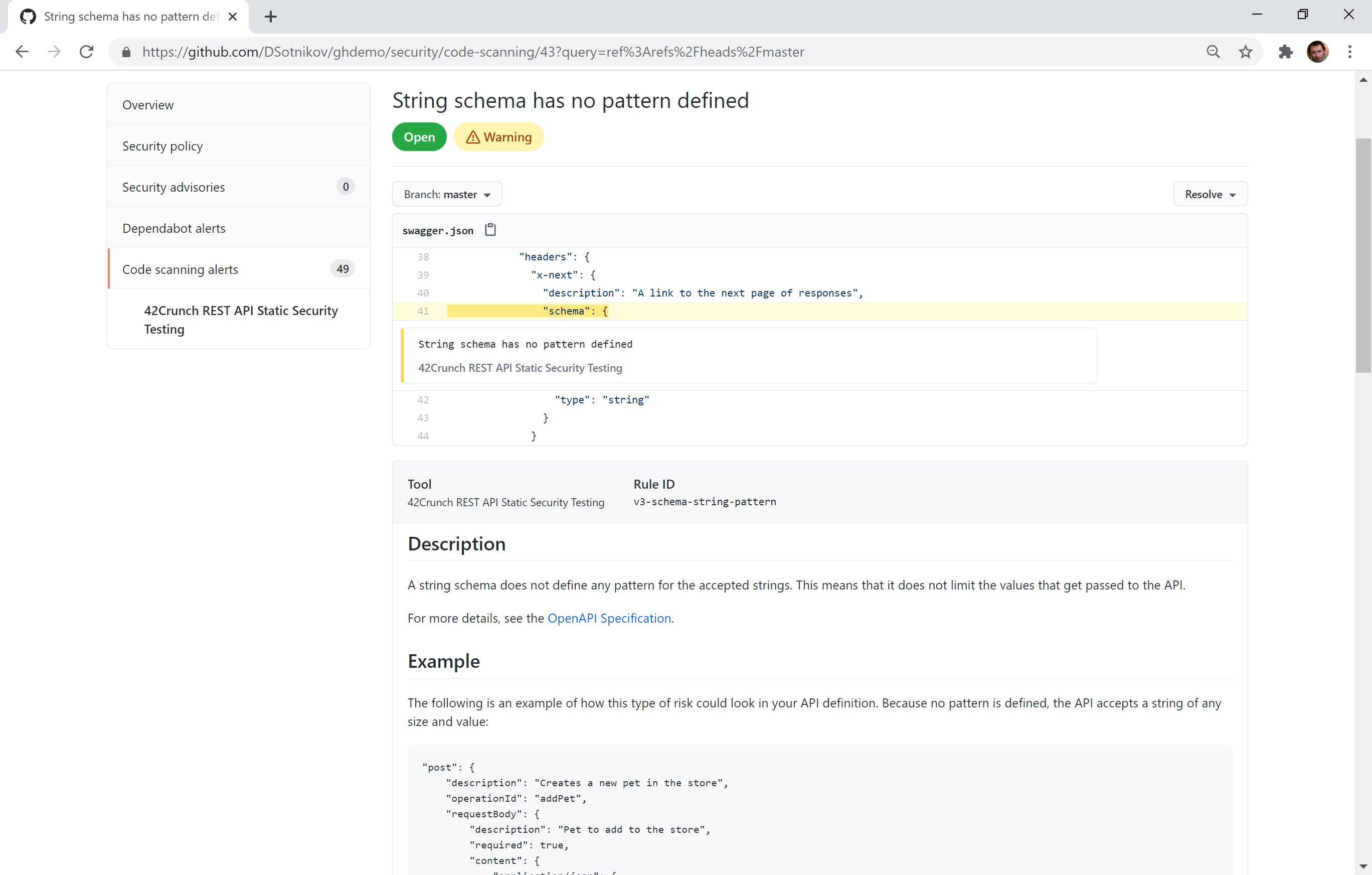
“This third and final figure shown above demonstrates how developers can click on any of the Code Scanning alerts to see the location of the issue in the API contract. For each issue selected like this, the tool explains the vulnerability, its potential exploit scenario, and explains how to remediate it.”
Delivering a seamless DevSecOps experience
The future of enterprise code development is definitely DevSecOps. But what does this methodology actually mean? DevOps was envisioned as a way of shortening the systems development lifecycle, and it consists of a set of practices that combine software development (Dev) and IT operations (Ops). DevSecOps builds upon the rapid-release cycle nature of DevOps by including some additional practices that enable security decisions to be made at the speed and scale of the DevOps life cycle. By enabling REST API security to be delivered as code, the 42Crunch’s REST API Static Security Testing tool provides a significant contribution toward making DevSecOps a reality in our fast-paced world of modern enterprise software development. If you’re a DevOps developer that uses GitHub, be sure to check out this tool today.
Featured image: Shutterstock