Firewalls are a key part of a defense-in-depth protection strategy used for safeguarding an organization’s network. Network intrusions are happening with increasing frequency from both internal and external sources, so protecting your business assets from these intrusions is a must. A firewall works by examining incoming IP packets and blocking any that it believes may be intrusive in their intention. Firewalls come in a variety of types and configurations from different vendors, and most enterprise networks have a number of them deployed at different points in their network.
A common strategy many IT professionals recommend is that you should put one brand of firewall at the edge of your business and a different brand in your internal data center. But this is old-school thinking, as my colleague Andrew Perchaluk explains in some detail in this article. Andrew, a senior systems administrator at the University of Manitoba in Winnipeg, Canada, provides us with some insight and tips from his own experience managing Active Directory environments. Andrew is a husband, father, and dog lover who has been working in the information technology industry for almost 20 years and who enjoys sharing his experiences with others in the IT pro community. For more information about Andrew see his LinkedIn profile. You can also follow him on Twitter. Let’s now hear what Andrew has to say on this topic of debunking this common approach to implementing network firewalls.
Firewalls infrastructure: Single vendor or multi-vendor?
Cisco defines a traditional firewall as a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. In today’s enterprise, there is now a greater adoption rate of next-generation firewalls (NGFWs), which are deep-packet inspection firewalls that move beyond traditional port/protocol inspection and blocking. They add application-level inspection, intrusion prevention, and bring intelligence from outside the firewall such as the ability to use Active Directory or Exchange as sources to help correlate firewall sessions to users and desktops all in real-time. There is also a trend toward software-defined and stretched datacenters, part of which means implementing virtual appliances or software firewalls in various locations.
Most medium to large businesses will have multiple firewalls to manage, because you have to protect your perimeter, your datacenter, and now even your cloud-based systems. Because of this issue and with the increased adoption of NGFWs, it’s now even more important to consider the question: “Should we use one vendor for all firewalls or multiple vendors?” I’ve heard the comment time and time again over the years and even recently by some IT professionals in conversations that “you need to have two different brands of firewalls, one brand at the edge, and one brand in the datacenter.” The figure below shows the traditional firewall model with two vendors:
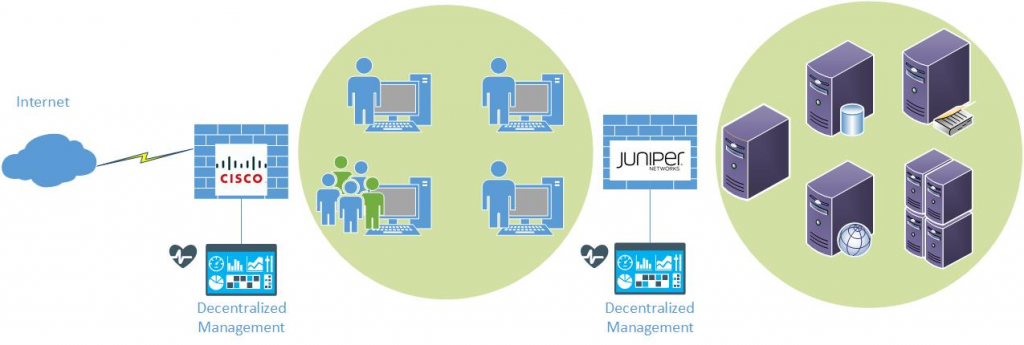
In this article let me explain why in the majority of cases this type of thinking is incorrect and can actually increase your risk of a data breach!
How do data breaches occur?
The vast majority of firewall breaches don’t occur because of a vulnerability in the code or a hidden flaw in the firewall. They occur because of firewall misconfigurations — some stats show that over 95 percent of breaches are due to this. For example, Breach Level Index states that over 3,000 data records are lost or stolen every minute, or 4.4 million per day, and that 96 percent of breached data is not encrypted. It might never be possible to prevent 100 percent of breaches, but it is possible to limit the misconfigurations that are made by simplifying our environments.
Contracts, support, and administration
There are many things that take up time for network admins and their managers:
- Renewing software or hardware contracts with a vendor.
- Purchasing additional hardware to expand the capacity of existing firewalls.
- Calling a vendor for support with a network issue or for known vulnerability information.
- Reviewing firewall logs or incoming threat analysis.
- Proper testing before making any changes.
- Preparing for and updating software and firmware on firewalls.
Having multiple firewall vendors mean that you have to perform these and other steps multiple times, which increases time spent and reduces productivity!
This isn’t the movies
The reality is that the hacker has nothing but time on his side. Despite all the depictions, firewalls are not simply a wall or blockade that the “bad guys” have to defeat to advance. There is no stopwatch or time limit for them. The way they actually get in is by finding a path that hasn’t been blocked yet. Most companies don’t become aware for weeks or months they have been hacked. Once the hackers are through the firewall, they can take their time and perform discovery. So if you’ve misconfigured your firewalls and left such an opening, it doesn’t matter if you have multiple vendor firewalls. Once the hacker has gotten through one of them, they have lots of time to get through the next one. So, needless to say, if you have two or three vendor firewalls, all with different methods of configuring rules and updating firmware, the chances of an error occurring that might leave one of these openings is higher than if you have just one.
Plan to go with a single vendor
For firewalls, using a single vendor solution like the one shown in the next diagram (an example of a hybrid cloud datacenter depicting a firewall model from only one vendor throughout) means the following:
- Less administrative complexity.
- Central management, i.e. one place to make changes and monitor.
- All the logs and threat data are the same format.
- Lower training requirements.
- Lower costs and greater discounts maintaining one brand of firewall.
- Ease of future scalability.

Don’t make things harder
Network administration is already complex enough, and with the trend of many businesses moving toward hybrid clouds and software-defined datacenters, it’s only going to get tougher. If you have multiple firewall vendors in your environment you are only adding to this complexity, and the chance of a misconfiguration leading to a breach is much higher. One brand of firewall doesn’t mean you’ll only have to support one vendor for everything else, but at least when it comes to firewall management your life will be simplified. Instead of having to deal with a second brand of firewall in your environment, you can now take any cost and time savings and implement other network or security products to protect your business, such as web application firewalls and cloud access security brokers.
If you currently have multiple firewall solutions in your environment, now might be the perfect time to start coming up with a plan to consolidate. Do some research, such as when your support contracts end for each. Look at your options for replacement such as cost, functionality and central management. And start consolidating!
Photo credit: FreeRange Stock




Stumbling upon this in 2021 it is of course still a very relevant concept.
As a hacker I’d say you are missing one key point with NGFW of a singular brand.
When I get through a PA (NGFW) and the next firewall is a similar PA, chances are higher that I will know which types of algorithms to use and obfuscate traffic with.
For medium to large businesses using 2 (NGFW) firewalls in this sort of setup ProviderCPE->Firewall->router/switch->Firewall->agg. switch, I would recommend using 2 different vendors (company wide) for NGFWs.
Great comment. Thanks!