Phishing attacks are consistently one of the most effective means that threat actors use to compromise user accounts. Most in the security world know how to recognize and deflect the bait emails utilized in a phishing scheme, but recently this has not been the case.
As reported by Mark Maunder at the cybersecurity blog Wordfence, there is a current phishing campaign primarily against Gmail users that, according to various posts, is extremely deceptive to even the most savvy security professional. The attack works by initially sending an email from an already infected account that belongs to a known contact.
The email itself shows an attachment, but this is actually an image rendering of a legitimate Gmail attachment. Upon clicking on the “attachment” for a preview a tab opens with a prompt to login to your Google account. The page itself looks like a carbon copy of the regular Google account login (see below)
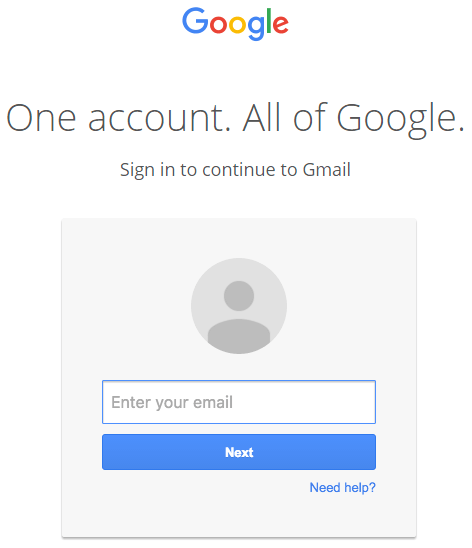
Upon entering the login information, you immediately give the hackers access to your actual Google account, which according to Maunder, not only gives access to emails but “a wide variety of other services that you use by using the password reset mechanism including other email accounts, any SaaS services you use and much more.”
A big reason why the bait for the login is taken has to do with the address bar. If there is any suspicion that a link may be misrepresenting itself, the first thought of any security-minded individual is to check the URL. The problem is, rather than some sketchy combination of characters, the address bar shows accounts.google.com which is deceiving many.
To protect against this attack, Mark Maunder recommends in his report that you must “check the browser location bar and verify the protocol, then verify the hostname.” What you’ll notice is that, in the images below, the fake link has information before the https, the lock, and the address. The legitimate link on the other hand will start with the lock symbol, then the https etc.
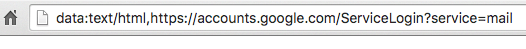
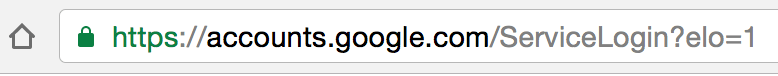
(real)
Additionally, and this cannot be stressed enough, enabling two-factor authentication can help you avoid a hack should you make the mistake of logging into a malicious link. It is not foolproof and it can still be hacked, but 2FA will make it much more difficult to gain access to your account.
In short, never think you are safe, even if you have been in the InfoSec game for a long time.
Photo credit: Mark Maunder



