We introduced the basic concepts of Amazon’s Identity and Access Management (IAM) service in a previous article here at TechGenix. The focus of this article is on how you can do a couple of simple tasks that will bolster IAM security, which you can apply to your AWS cloud. Let’s get started!
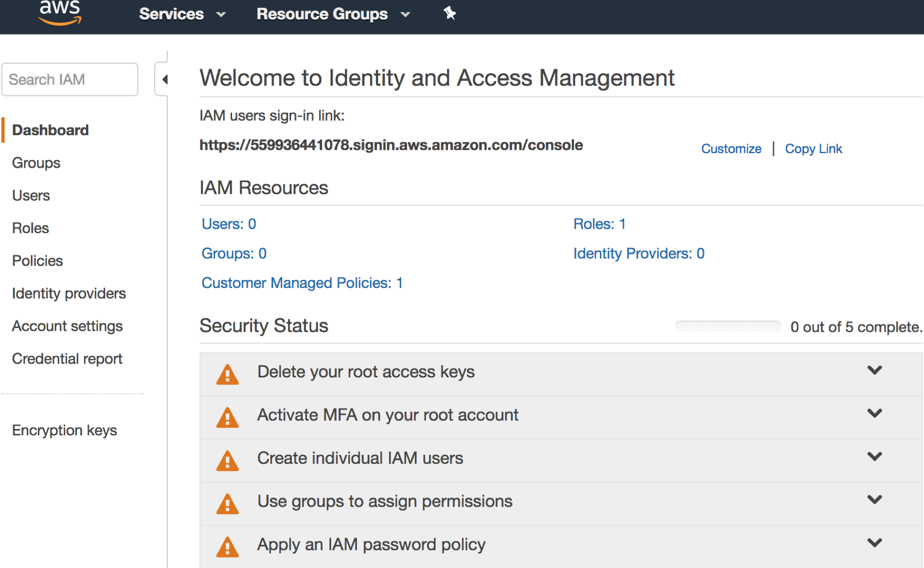
We are starting by checking the Security Status section of the Identity and Access Management console. As we can see there are five items that have a warning state. We will work on fixing those alerts throughout this article. As a result, we will have a more secure environment.
Removing the root access keys
The root account is the most powerful account in AWS and it cannot be restricted in any way. We should use the root account only to create new users and delegate permissions accordingly but never on a daily basis.
If your root account has access keys, those should be removed. The root account most likely will be used just for console access and not AWS CLI or SDK access.
To remove root access key, expand Delete your root access keys item on the Security Status and click on Manage Security Credentials.
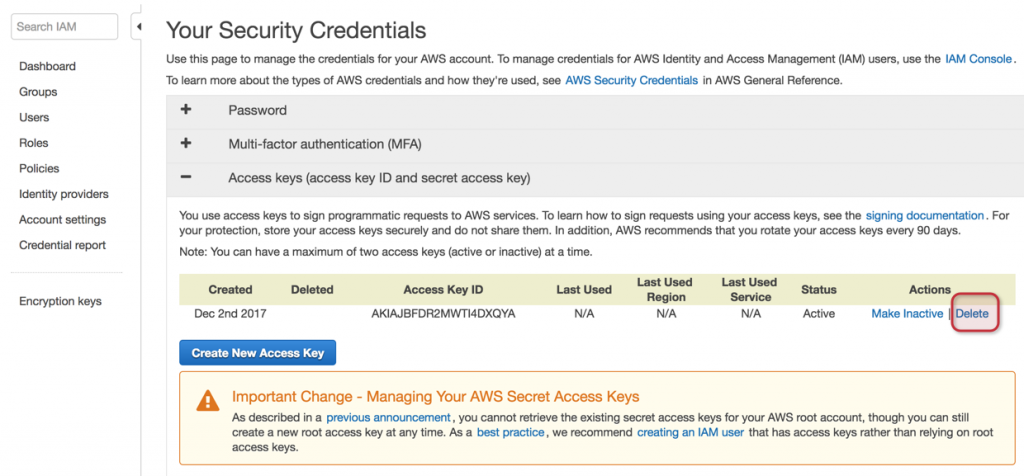
A new page entitled Your Security Credentials will be displayed. Expand Access Keys (access key ID and secret access key) section. A list of your access key will be listed. Delete all of them using Delete link located on the right side, and confirm any dialogue box that may show up.
Using users and groups
Due to the importance of the root account, it is highly recommended to create a user (even if you are a single administrator) to manage AWS. If you have more than one user and need to delegate permissions to different team members, then the use of groups becomes critical to make delegation consistent and easy to manage.
Defining a password policy
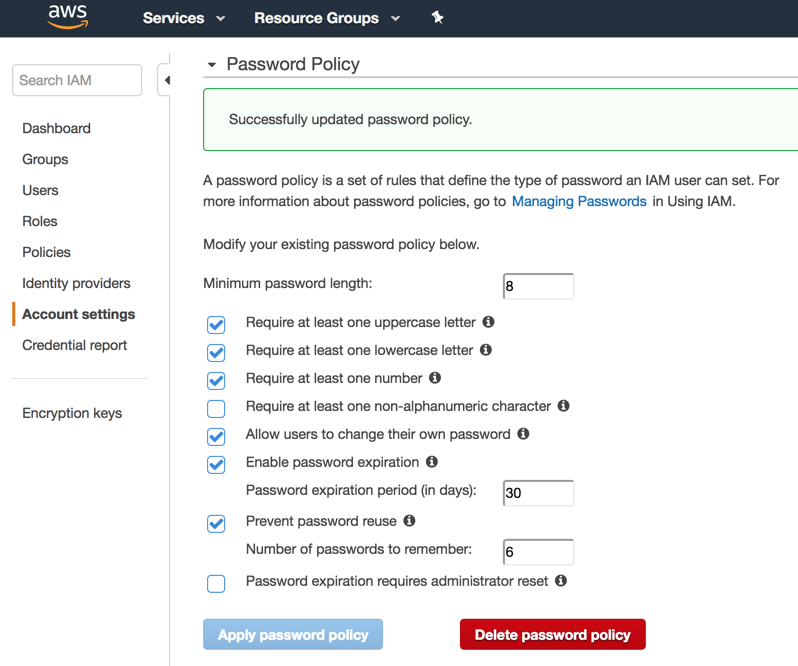
To define a password policy, click on Account Settings item located on the left side, and define the parameters and values that you want to enforce. After that click on Apply password policy.
Note: There is a single Password Policy and it applies globally.
Managing multifactor authentication
The AWS Console or access key is not for all users in your company. Just a handful of users may need access to it. Multifactor authentication (MFA) is a key security feature that should be implemented for all users, and it must be implemented in the root account.
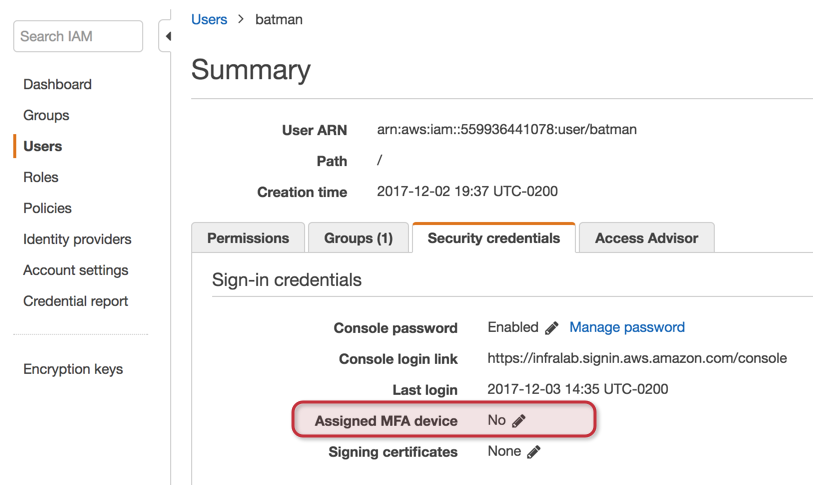
To enable MFA in the root account, expand Activate MFA on your root account, and click on Manage MFA. For a regular IAM user, click on the desired user and click on Security Credentials tab, and then click on edit icon located on the Assign MFA device.
The process to enable MFA is through a series of questions. The first one is the choice between a virtual or a hardware MFA device (the virtual does not have a cost and we can use an app such as Google Authenticator). In this article, we will use virtual and then click on Next Step.

A new dialogue box informs you that the app must be installed. It is time to go to your device and install Google Authenticator on it and be ready to add an account. Click on Next Step.
The next step will entail using a QR code. On your mobile device click on the Add button and point the device to the QR code, which will create an entry on Google Authenticator. The next step is to enter two consecutive codes on the AWS console. The AWS console with the QR code and the Google Authenticator are depicted in the images below.
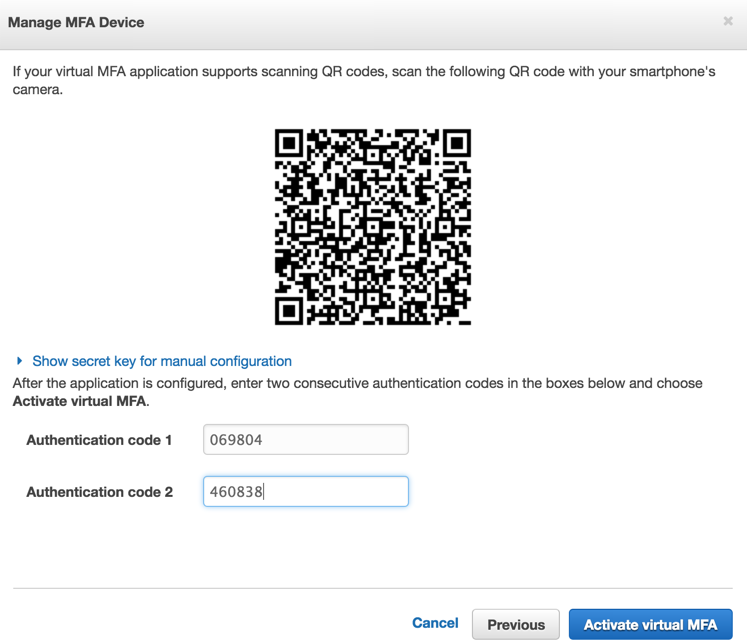

If everything goes well, a final dialogue box informing that the MFA device was successfully associated with the account will be displayed. Click on Finish.
Enabling MFA means that for every new logon on the AWS Console, a code displayed on Google Authenticator will be required to allow access.
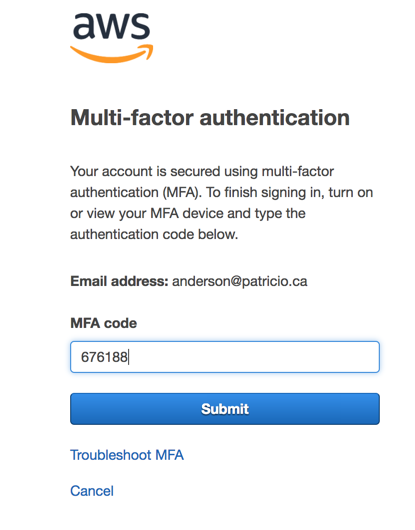
Checking IAM user utilization
After enabling the recommended security best practices, we can use a built-in feature to keep track of our IAM users utilization, including the status of their credentials, MFA information, and last time their account had activity. A good practice is to purge accounts that are no longer in use.
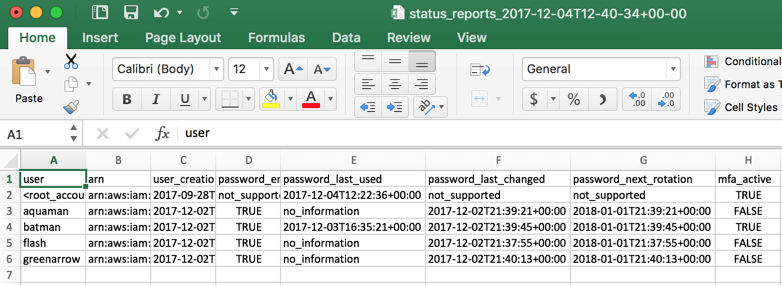
Click on Credential Report. On the right side there is a single button: Download Report, which will be a CSV file.
The image below shows some of the fields listed on the CSV file. Using them the administrator can check the current utilization and features enabled for its IAM users.
Final check
After spending a few minutes improving our security, we can refresh the Dashboard page of the IAM Console. At this time, the results should be 5 out of 5 for the Security Status.

By following the few easy steps outlined here, your IAM security will be enhanced and your AWS cloud will be more secure.



