In the Fall Creators update for Windows 10, Microsoft has included some very interesting security tools. Before I explain these tools, let’s draw a line between what most people will have, the Pro edition, from what Microsoft promotes, the Enterprise edition with the Advanced Threat Management (ATM) subscription. As an SMB MSP company, none of my clients currently have the Enterprise edition of Windows 10 and none are yet subscribing to ATM. Therefore, I pose the question: what new features do my clients have? And how should I implement those?
Four big areas of concern
The big four areas of concern are Edge, Windows Defender, Controlled Folder Access, and the elimination of the Enhanced Mitigation Experience Toolkit (EMET).
Edge: I should convince my clients to use Edge as much as possible for protection against malicious websites. Sure, there are going to be applications and web pages that aren’t yet compatible, but those are fewer and fewer as designers build for the latest browser technology. Currently, Edge is the most secure browser. Historically, the newest browser is always the fastest and the most secure and nothing has changed here (except its new contender, Firefox Quantum). Edge is currently the best in these areas.
In the Pro edition of Windows 10, we don’t get the benefit of Application Guard which virtualizes Edge to isolate it from the memory space of the operating system and other open applications, but we do get Code Integrity Guard (CIG) and Arbitrary Code Guard (ACG) to perform these tasks for us. These require DLLs to be Microsoft, Windows Store, or WHQL-signed, and if a violation occurs, the kernel will fail attempts to load the DLL. It further prevents the browser from spawning applications and the making of code stored in memory writable. This is great protection against malicious websites. In addition, Windows Defender is able to extend its protections into Edge too.
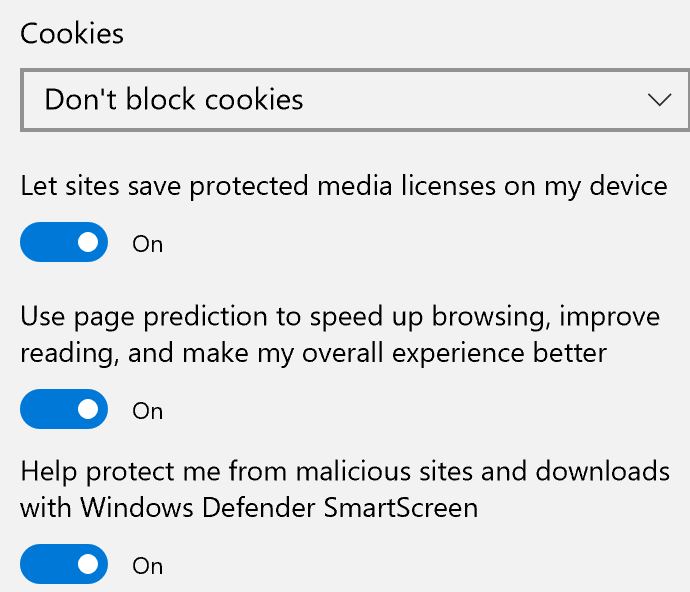
The good news is that these settings are configured by default so there’s nothing to do. To verify that Windows Defender protections are enabled, click the ellipse (the three dots) in the Edge toolbar, go to Advanced settings, scroll down to the bottom, and make sure the “Help protect me from malicious sites and downloads with Windows Defender SmartScreen” is turned on.
Finally, if your users are still quite attached to Internet Explorer, start an education plan to get them comfortable with Edge. IE is on life-support and really only exists for backward-compatibility purposes. Microsoft even has a tab in IE that opens Edge. If that isn’t writing on the wall, I don’t know what is.
Controlled Folder Access: I should enable Controlled Folder Access to help prevent Ransomware, but I really have to plan the configuration of it carefully. Controlled Folder Access protects the Documents, Pictures, Videos, Music, Favorites, and Desktop from being written to by untrusted applications. I can add other folders that my users need protecting too. This is great for Ransomware prevention, but it is very intrusive for the users and results in a lot of pop-up messages until you get it configured properly. Do it wrong and your users will revolt and you’ll never be able to get this protection in production again. I’m looking a bit sideways at Controlled Folder Access and you will too because it’s kind of like Account Control settings a few years ago when it first rolled out. Remember how painful that was?
The protection of Account Control is fantastic, but users hated it because they were getting pop-ups too frequently. These days, it’s enabled by default and your users don’t even know it’s there protecting them. I expect that Controlled Folder access will be like this eventually too, but for now, we’re going to have to configure it. While Microsoft says that they have an algorithm in place that decides whether or not an application should be trusted, ironically, even its own Office applications aren’t trusted by default. My self-experimentation with this feature annoyed me out of the gate by not allowing me to save Word documents into the Documents folder. After some whitelisting, I have now built a list that I can take to my clients and by policy get Controlled Folder Access properly configured for them. I feel so strongly about the importance of this feature that I’m going to be added it to my Ransomware Prevention Kit as a primary tool for protecting Windows 10.
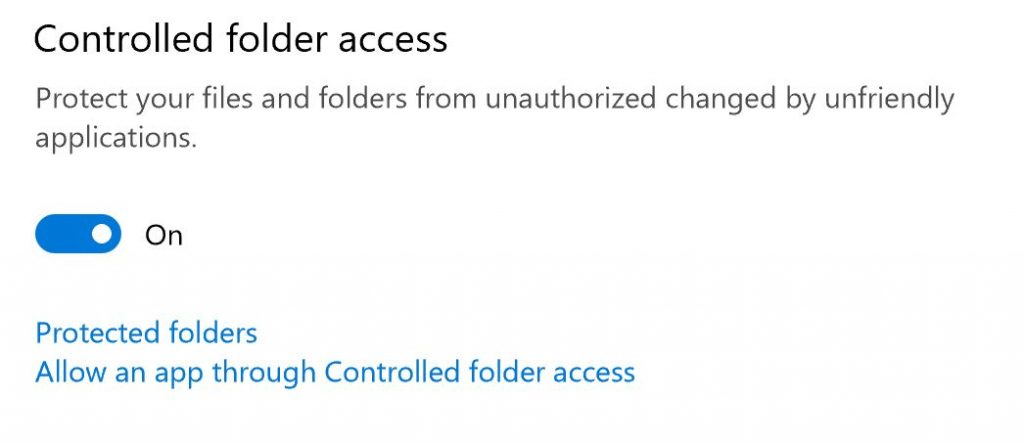
How to configure Controlled Folder Access
Controlled Folder Access is a bit buried. You’ll find it in Windows Defender > Virus & Threat Protection > Virus & Threat Protection settings. Click that and scroll down to the bottom of the page. You should now see what’s in the figure above. It is Off by default. To enable this setting, flip it to the On position.
To begin configuring, click on the Protected Folders link. Here you see a list of the folders that are protected. This protection only allows authorized applications to write to the folder. With this restriction in place, ransomware and other malicious files won’t be able to save their changes to your data. Click the + sign to add a new data location. They don’t even have to be local!
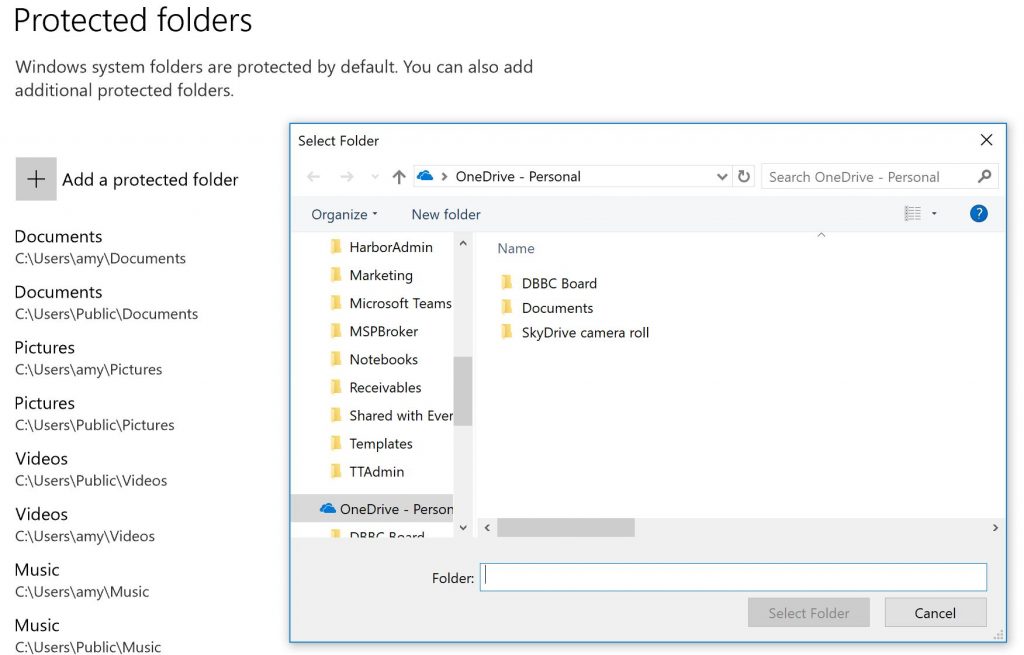
If you later want to remove a folder from protection, just click it and then the Remove button will appear for you to select.
Once you’ve chosen to protect a folder, you are immediately going to find that you can’t save any files, nor can you applications save any personal configurations. Two things will happen: The application will pop up with a “file not found” message, which is its way of saying “I can’t save this file,” and Defender will show a notification telling you about the unauthorized change to your protected folder.

In the case above, I added OneDrive to my protected folders. Sure, OneDrive keeps previous versions of your files, but they are a pain to revert to should the whole lot of them get encrypted. Once I’ve protected that folder, I decided to save a new image from my snipping tool to it and got the above notification. This is my cue to whitelist SnippingTool.exe. To do this, click the “Allow an App” through the Controlled Folder Access link. It is located just under the link you used to protect the folder (see above). This is a whitelist for Controlled Folder Access and now you can see why you are going to have to do this for your users and plan this rollout carefully.
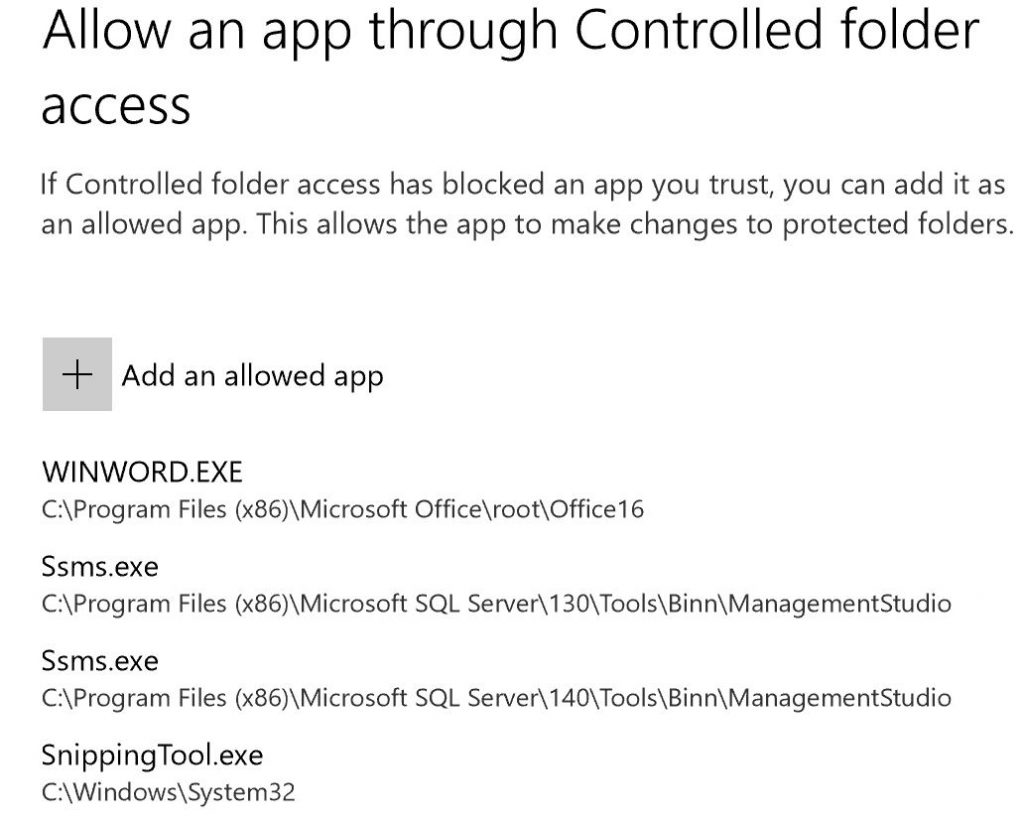
Click the + to add an application. I recommend using the notification to determine the location of the .exe. Once you’ve built your allowed list, you’ll be ready to build such a list for Group Policy or Powershell to configure your users’ computers and save them the pain that you just went through. My plan is to gather a standard set, push it out to a few people who will test it, and use their results to build department level whitelists. Each department in a business probably has apps that are specific to them that will need to be added to the whitelist.
Windows Defender: I need to make Windows Defender the primary anti-virus on the machine to prevent non-exe infections, like some new ransomware variants, from running. Defender uses Attack Surface Reduction to prevent scripts, email, and Office applications from running malicious code and it does it by comparing behaviors to Microsoft’s worldwide graph of such information gathered from other users of these applications. Windows Defender also enables anti-phishing inbound network connection preventions, but again, it has to be the primary anti-virus on the machine to do it.
That brings me to a suggestion that will fly in the face of everything that we as IT have done to this point. I’m going to stop recommending third-party anti-virus. Windows Defender is set up to sit in the background and only do minimal protections should you have another product installed, so in order to get these great protections, Defender has to be the primary AV tool on your machine. Microsoft is finally taking the driver’s seat and I’ve decided to recommend to my clients that we let them.
EMET: Finally, there’s one more thing important to note. EMET is gone. In my practice, we used EMET to protect the computers that used accounting software and made payments. It was mostly to enhance Internet Explorer. However, Microsoft has now built those protections into Windows 10 and it calls those “Windows Defender Exploit Guard.” You can read all about what this means on TechNet. The settings are lengthy and complex, but the important thing to note is that if you were already running EMET, when you update Windows 10, it’s going to be removed. This is so there’s no conflict between the new Exploit Guard and EMET. There is a process to follow to convert your EMET settings into Device Guard that you will have to follow. However, if you’ve been successful at moving your users over to Edge, then you’re already going to be a long way there. In fact, if you can eliminate IE, then you will most likely not have any need to migrate your current settings.
Unknown to most people is that Microsoft is the largest security company in the world, but for too long they have kept this a secret for the enterprises to hold. With Windows 10, we are finally seeing excellent security tools and postures coming down to the “normal” Windows 10 user. This is very good news for small businesses that generally do not participate in Enterprise agreements. Microsoft is trying to change this with the new Microsoft 365 subscriptions, but it will take a lot of time for them to migrate their customers over to that model. Meanwhile, they’ve done an excellent job at bringing us a more secure platform to start with.



