Protecting your company’s network against ransomware attacks is a huge and growing concern among IT professionals today. I even devoted a whole issue of WServerNews, our weekly IT pro newsletter, to the challenges businesses and individuals face when dealing with and trying to prevent ransomware. By the way, while you’re at it visit this page and make sure you’re subscribed to both our TechGenix Weekly IT Update emails and our popular WServerNews newsletter — you won’t regret it!
Anyway, the question I always get from business leaders is how can I protect my company from a ransomware attack? Unfortunately, there’s no simple answer to this problem, just as there’s no sure-fire way of safeguarding yourself against con men like in the movies “Oceans 11” and “The Sting.” It takes shrewdness and brains and even a paranoid personality to ensure you don’t get conned by someone, somewhere, sometime. Fortunately, there are some technical tools and solutions that can help if you use them correctly, and my colleague Andrew Perchaluk is going to walk us through the use of one of them: File Server Resource Manager. FRSM is a role service in Windows Server that lets you manage and classify data stored on file servers. It includes such capabilities as file screening, quote management, storage reporting, and various file classification and management capabilities. Andrew is going to explain for us how FSRM can be leveraged by Windows Server admins to help safeguard their environments against ransomware attacks. Andrew is a senior systems administrator at the University of Manitoba in Winnipeg, Canada, and has been working in the information technology industry for almost 20 years. He is a husband, father, and dog lover, and he enjoys sharing his experiences with others in the IT pro community. For more information about Andrew see his LinkedIn profile and you can also follow him on Twitter. Let’s now listen what Andrew has to say about this subject.
The problem of ransomware
Ransomware has been running rampant the last couple of months by taking advantage of an SMB vulnerability in Microsoft Windows. If you’re lucky, you’ve only heard the news about NotPetya, Petya, and WannaCry. If you are unlucky, your business has been held hostage by this ransomware or a variant and you understand firsthand how much damage was caused. Microsoft did release a patch for this vulnerability, even to end-of-life operating systems like Windows XP and Windows Server 2003, but many businesses still have not yet applied the patch.
How can you prevent ransomware and keep your business safe? Patch your systems, educate your employees, and block the SMB protocol on your edge firewalls. One other way to prevent ransomware is by using the file screening component of the Microsoft File System Resource Manager on Windows file servers. You may be familiar with FSRM and even used it for quota management, but it also has a powerful feature for file screening that can be set to actively monitor network shares and send alerts when ransomware tries to save itself to these shares.
What do you need for effective file screening?
First, if you do not have the FSRM role running on your Windows file servers, install it. As we know, doing things manually can lead to falling behind or user error. Because of this we wanted to automate this process as much as possible as well as have some safeguards in place. My goal was to implement the following on our file servers:
- Download known ransomware extensions daily and block automatically.
- We decided to use this list with currently over 1,200 known ransomware extensions and files. (Use this URL for the formatted list as it is updated regularly and a good comprehensive source of ransomware extensions.)
- We needed to have a whitelist for extensions we did not want to be blocked so we prepopulated a skiplist.txt file starting with 45 of our common file extensions.
- We wanted to be alerted if someone tried to save a ransomware file to the network, and we also wanted to alert the user and our help desk with an email.
- We wanted to get a daily email alert on “new” ransomware extensions that have been automatically added to the list.
- We also eventually wanted the option to automatically remove users share permissions via a deny rule once they saved a ransomware file to a network share.
Implementing effective file screening
These scripts will utilize the features of FSRM called file screening, which includes:
- File screens.
- File screen templates.
- File groups.
You will end up with a file screen created per network share, and a file screen template that looks like this:
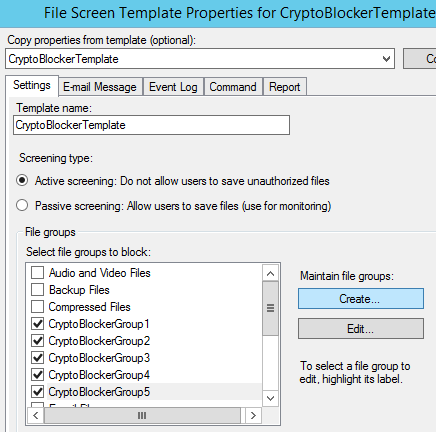
And a number of file groups, which are the files and extensions that will be blocked:
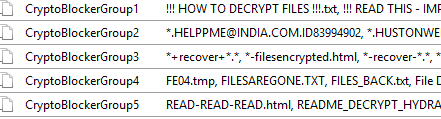
NOTE: The original PowerShell code that we adapted our code from is available on Github courtesy of nexxai.
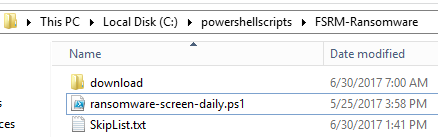
Step 1: Set up a folder on each file server C:\powershellscripts\FSRM-Ransomware\.
Step 2: Place the .ps1 script inside this folder. This contains the PowerShell code we have working. The script splits the ransomware extensions into five files to get around the 4KB file size limitation of FSRM file groups. You can download this script here as a .txt file and just rename it as a .ps1 file.
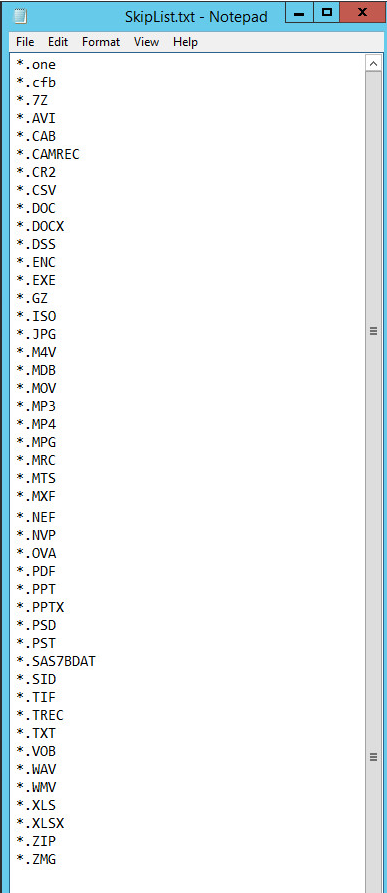
Step 3: Create a file called skiplist.txt and populate it with the extensions/file names you would like to exclude (one item per line). Here is a screen shot of what we put in ours, which contains 45 items:
Step 4: Create a subfolder called “download.” This will contain your daily (provided you choose to run the script daily) files with new ransomware extensions.
Step 5: To automate this, setup a scheduled task to run daily or as often you like.
Step 6: To get the daily email alert on new ransomware extensions that have been automatically added to the list, use this PowerShell script and place in the C:\powershellscripts\FSRM-Ransomware\ on one file server only. (If you add it to all file servers, you will end up with multiple email notifications.)
Step 7: Set up a scheduled task to run daily after the original file screening setup scheduled task.
Prevent ransomware: The more tools the better
We have this automated and running for a few months now, and my recommendation is to leave it in place for a number of months before attempting to automatically remove user access to shares (accomplished using a deny rule script attached to your file screen template). By doing this you can address any false positives that might arise. I hope that this gives you one more tool for your Swiss army knife to prevent ransomware!
Photo credit: Wikimedia




Tried to set this up on my file server but it would never enumerate any of my shares. I wound up cutting that part out of your script and just using the part that downloads the file and parses it into File Groups which did save me a lot of time. I then manually created the File Screens and selected the appropriate File Groups.
Glad you found a way to make use of part of Andrew’s script!
Micth, I’m running your script in Win 2012 R2 server and get the following errors. Do you have an updated script using the FSRM cmdlets?
—-
####
Adding/replacing File Screens..
File Screen for [D:\data] with Source Template [CryptoBlockerTemplate]..
This tool is deprecated and may be removed in future releases of Windows. Please use the Windows PowerShell cmdlets in t
he FileServerResourceManager module to administer File Server Resource Manager functionality.
The requested object was not found.
This tool is deprecated and may be removed in future releases of Windows. Please use the Windows PowerShell cmdlets in t
he FileServerResourceManager module to administer File Server Resource Manager functionality.
File screen successfully created for “D:\data”.
File Screen for [D:\data\pb] with Source Template [CryptoBlockerTemplate]..
This tool is deprecated and may be removed in future releases of Windows. Please use the Windows PowerShell cmdlets in t
he FileServerResourceManager module to administer File Server Resource Manager functionality.
The requested object was not found.
This tool is deprecated and may be removed in future releases of Windows. Please use the Windows PowerShell cmdlets in t
he FileServerResourceManager module to administer File Server Resource Manager functionality.
File screen successfully created for “D:\data\pb”.
File Screen for [D:\data\shared\quickbooks] with Source Template [CryptoBlockerTemplate]..
This tool is deprecated and may be removed in future releases of Windows. Please use the Windows PowerShell cmdlets in t
he FileServerResourceManager module to administer File Server Resource Manager functionality.
The requested object was not found.
This tool is deprecated and may be removed in future releases of Windows. Please use the Windows PowerShell cmdlets in t
he FileServerResourceManager module to administer File Server Resource Manager functionality.
File screen successfully created for “D:\data\shared\quickbooks”.
####
Cleaning up temporary stuff..
####
Done.
####
—-
Unfortunately Andrew crafted the script and he’s since moved on to other things so can’t help. You might try asking over here: https://social.technet.microsoft.com/Forums/en-US/home?forum=winserverfiles&filter=alltypes&sort=lastpostdesc
The Email part of the script is not working for me. The Yesterday.TXT file is empty. Not sure what to do, below is the error.
PS C:\Windows\system32> C:\DATA\Scripts\FSRM-RansomWare\ransomware-new-extensions-email-alert.ps1
Compare-Object : Cannot bind argument to parameter ‘ReferenceObject’ because it is null.
At C:\DATA\Scripts\FSRM-RansomWare\ransomware-new-extensions-email-alert.ps1:4 char:50
+ $newExtensions = Compare-Object -ReferenceObject $yesterday -Differen …
+ ~~~~~~~~~~
+ CategoryInfo : InvalidData: (:) [Compare-Object], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationErrorNullNotAllowed,Microsoft.PowerShell.Commands.CompareObjectCommand
Try asking over here: https://social.technet.microsoft.com/Forums/en-US/home?forum=winserverfiles&filter=alltypes&sort=lastpostdesc