Email security is a top concern of most IT professionals today. The old way of doing things was to subscribe to a third party to filter your email. But there are new ways to do it too. Some of those new ways use old tools like transport rules, some are anti-phishing rules, some are cloud app security policies, some are conditional access. It’s another case of it takes a village but once you’ve built your village your users are much less likely to be the cause of a network breach — and that is hugely significant because today’s threats typically come from people clicking on something they shouldn’t be. I’m going to share the set of rules and alerts that I use to protect, monitor, and manage my Microsoft 365 cloud email infrastructures under my charge across a variety of clients in various industries. At the end, I’ll show you some of the reports that you should be getting and reviewing.
If you’d like to implement these, just follow along from the screenshots that I’ve provided for each of them but remember that there’s no guarantee that these will solve all of your email security issues — and I haven’t given away all of my secrets. Securing email is always a work in progress because the bad guys never rest from finding ways around our preventions. Keep layering is the best advice you can get. The second best advice is to hire a professional. I see far too many businesses buying online email systems but not configuring them or not purchasing the subscriptions levels necessary to protect them. I run a ransomware and security group and daily someone posts about another preventable sad tale of a business in ruins. It’s a small investment to do this right. Just like you invested in protecting the server when it was in your office, so too do you need to invest in protecting your business when it moves to the cloud.
Transport rules
Transport rules work by intercepting mail and acting upon according to the rules you’ve set up. Here are a few from my standard set.
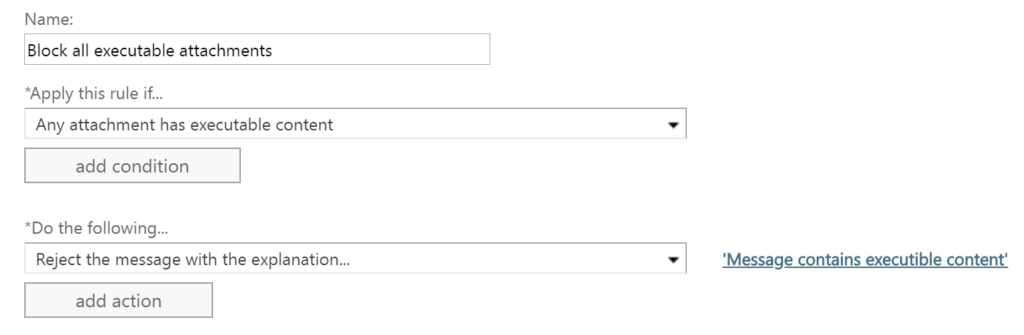
Block all executable attachments: This rule blocks anything that could actively run. Microsoft defines that and maintains the block criteria. All you have to do is select the item from the list and create your rule as below.
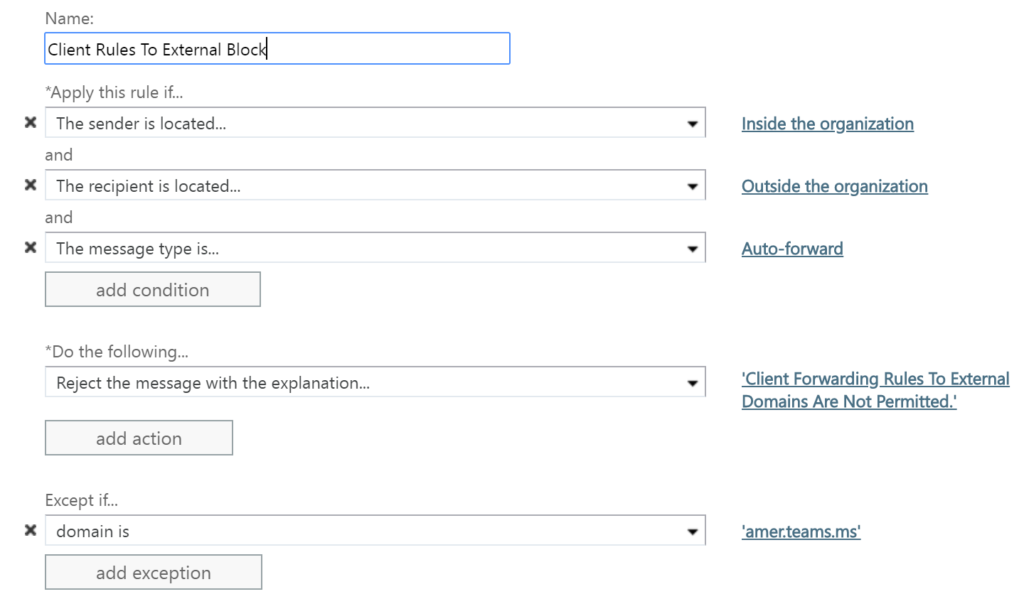
Block auto-forwarding: This rule prevents outlook rules from forwarding email out of your organization. If your employees account credentials have been compromised this is often one of the first things that the bad guys will do. Create your rule as below and add any exclusions that your business might require. In the example, exclusion has been made to allow forwarding into Microsoft Teams.
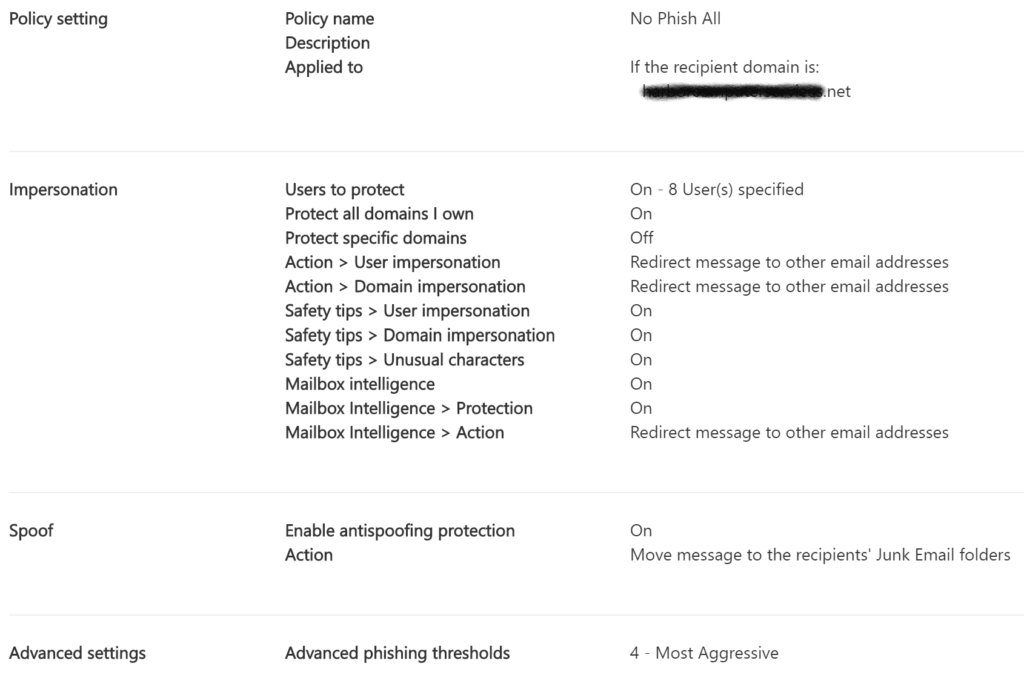
Anti-phishing: Microsoft has made anti-phishing rules available to all 365 subscribers. Don’t be afraid to bring the settings up to full. The only false positives I’ve seen in doing so are some newsletter, and users can always whitelist the ones that they are actually reading.
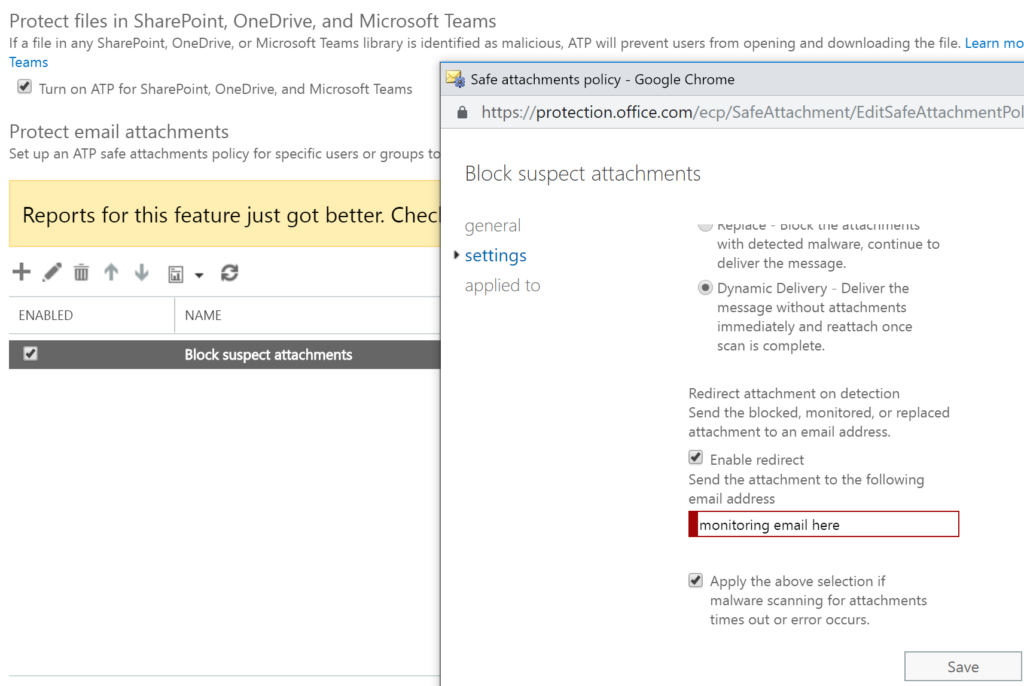
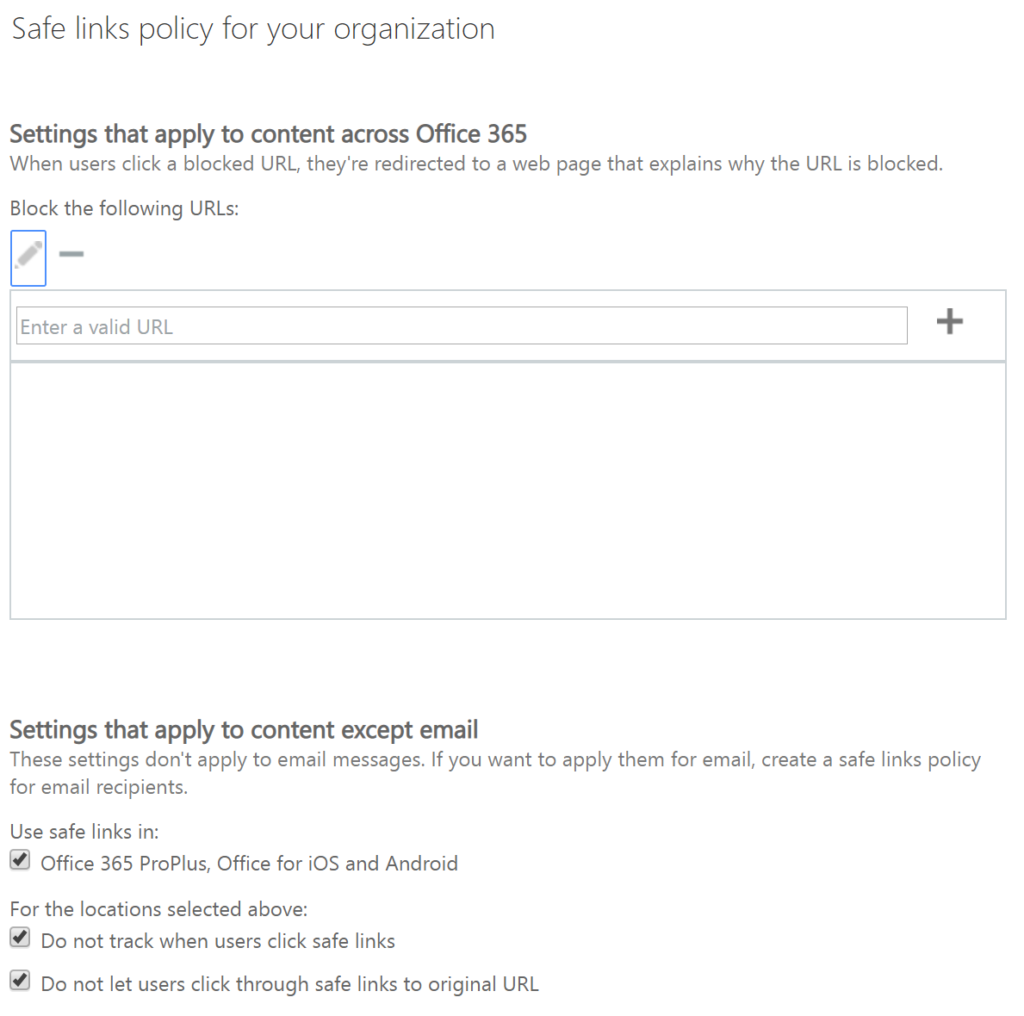
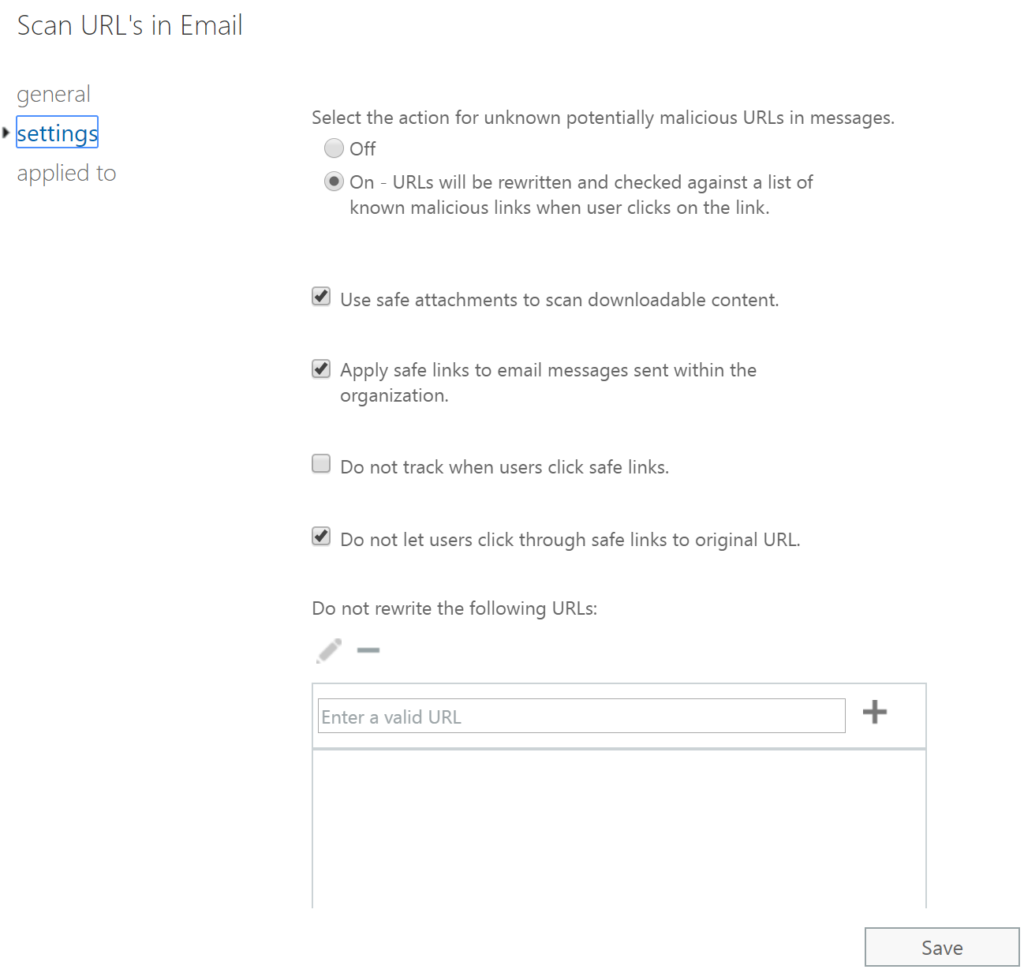
Safe link and safe attachments: These rules may require a certain level of 365 subscription, but even the Microsoft 365 Business plan has these now. Using Microsoft’s leverage as the largest email processor in the world, they will prescan links and attachments for malware. As noted in the setting definitions many of these policies apply to data, whether desktop or mobile too.
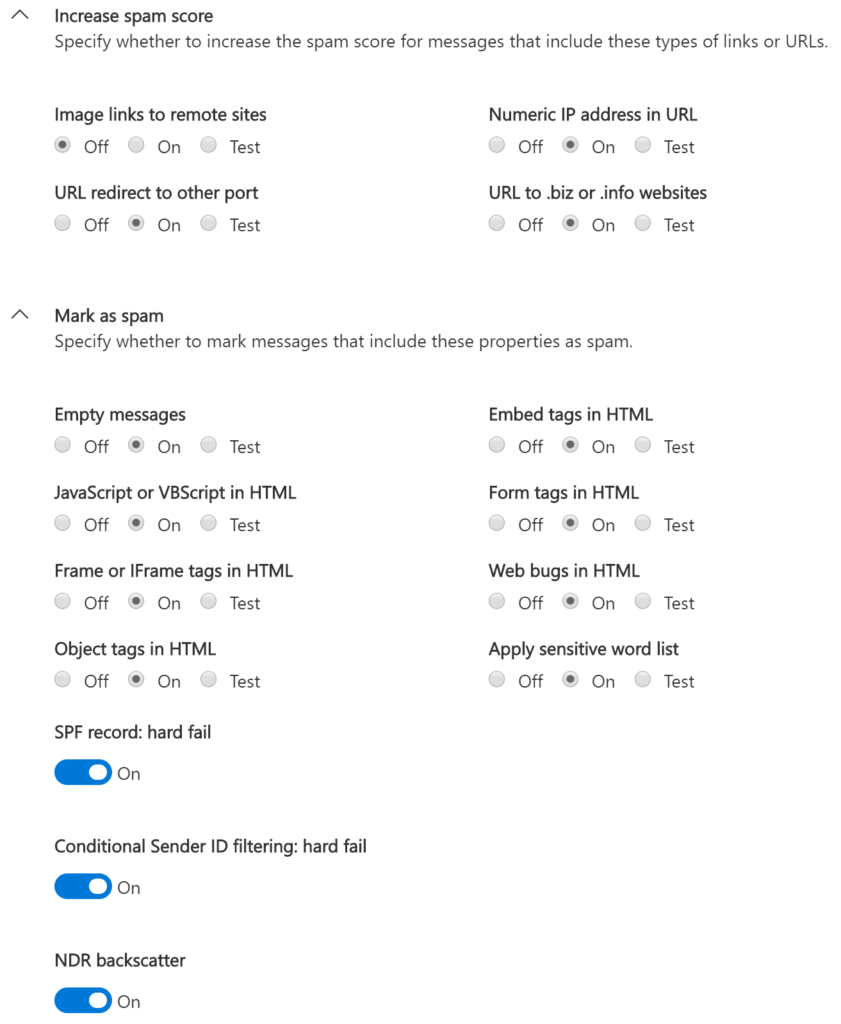
Spam policy: Microsoft provides a default policy, but you should customize your own. In this policy, you’ll define what to do with messages that are caught by your policies, as well as some more advanced features. In particular, blocking messages from countries you don’t do business with is a very powerful filtering technique. Your results may vary with these settings. Microsoft provides the ability to run in test mode where you can monitor what would have been caught. As you can see I prefer settings that are as quite restrictive. As email is the No. 1 way in which people are phished and malware is delivered, I would rather err on the side of caution.
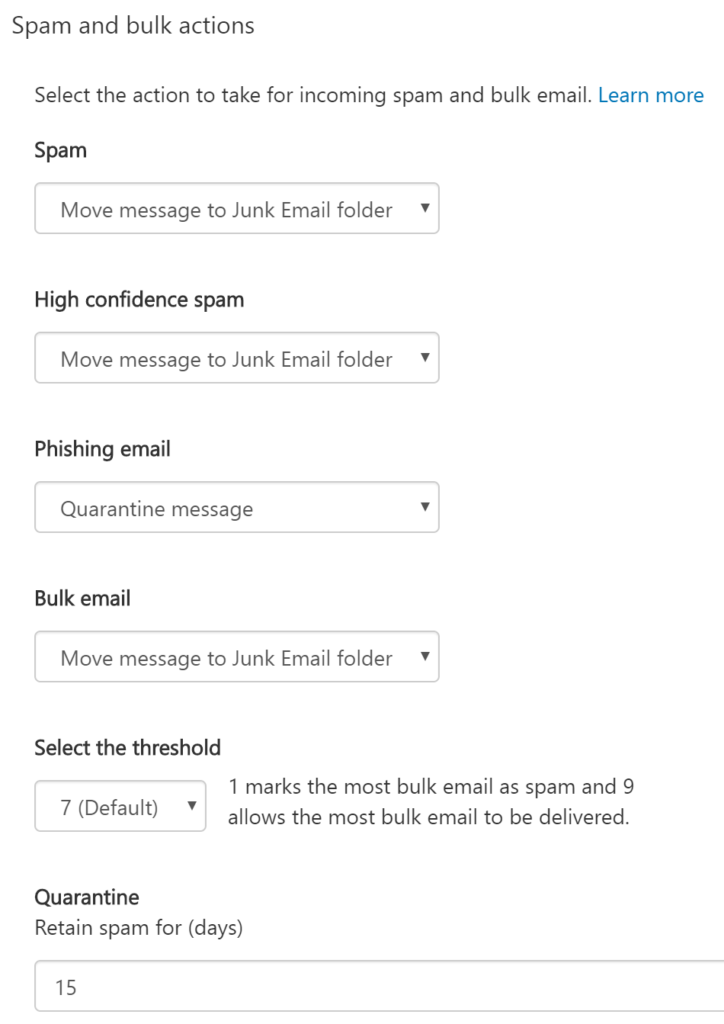
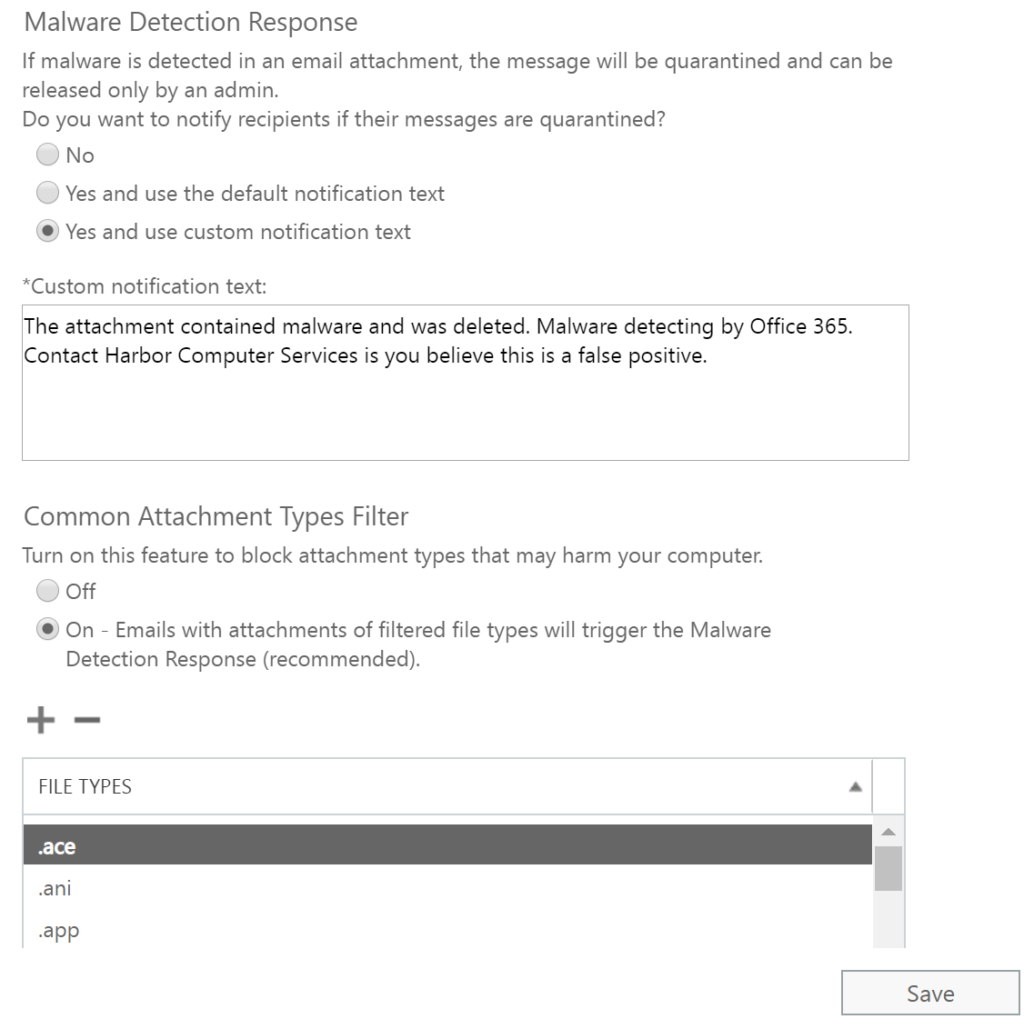
Malware detection: Since I’m putting detection settings up pretty high, I want to make sure that people are notified should an email get quarantined. In addition in order for our previous executable policy to work, I need to make sure that the definitions are turned on here. This list is the same list that Outlook contains natively but we’ve applied it to more than just email through our previous rules.
Let employees help
Everyone needs to be engaged in the fight against breaches introduced via email. Education is a key component. Make sure that everyone has had training on how to identify suspicious email and to understand what today’s threats look like. They also need permission to interrupt you by asking whether or not an email is safe. It’s our better-safe-than-sorry policy. Just ask and we will review the email. It’s a teachable moment, too, so take the time to teach them how you made the determination.
Let’s also give our people a tool to report messages that got through our precautions so detection continually improves.
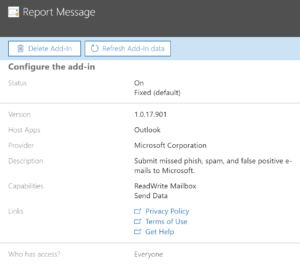
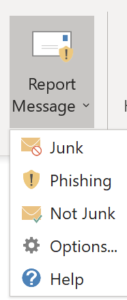 In the admin portal under Settings, choose Services & Add-ins and deploy the Report Message add-in to Outlook.
In the admin portal under Settings, choose Services & Add-ins and deploy the Report Message add-in to Outlook.
More advanced policies
For those of you with licenses for advanced alerting in Microsoft 365, there are some more options. These will require Azure AD P1 or Cloud App Security licensing but are well worth a few extra dollars for the security they deliver. Here we’re going to just look at rules I’ve created for email protection but that licensing brings to much more to our tenant than just these few rules. These rule types take advantage of AI with behavior learning.
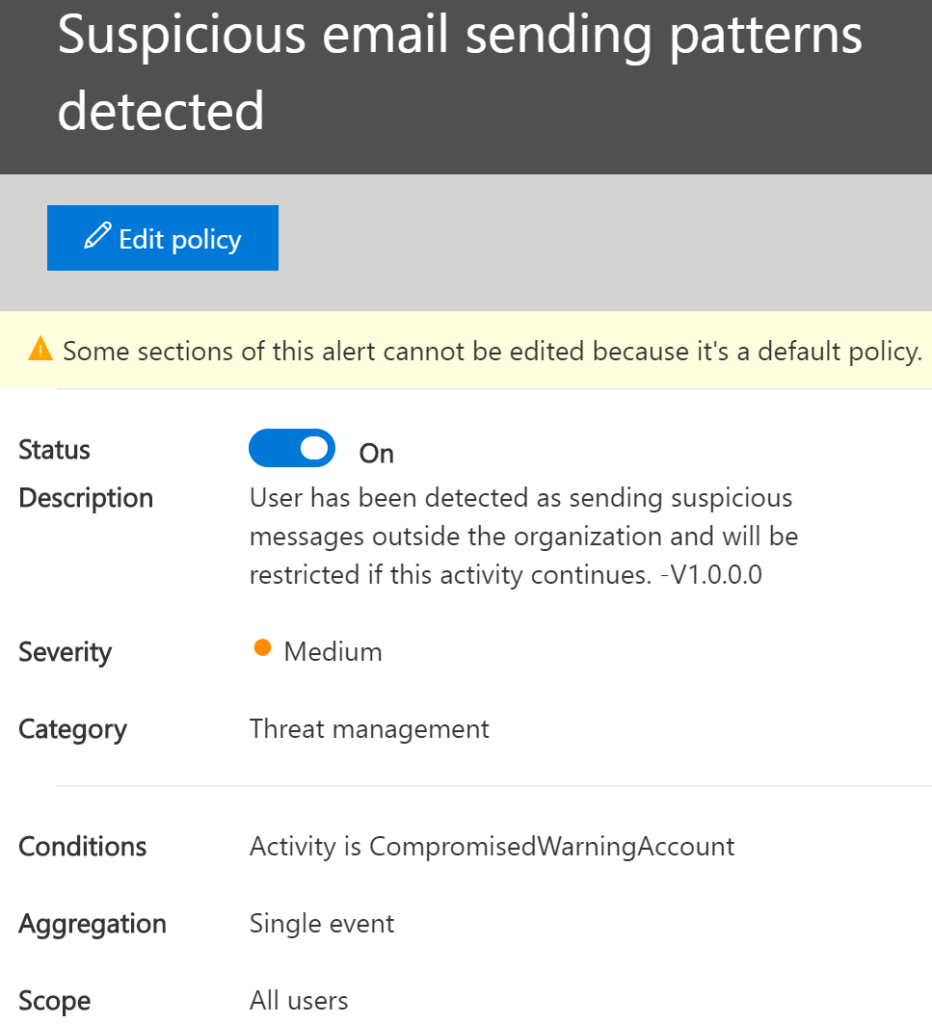
Suspicious email sending patterns: By building an activity profile, we can see if anything suddenly starts acting out of the norm.
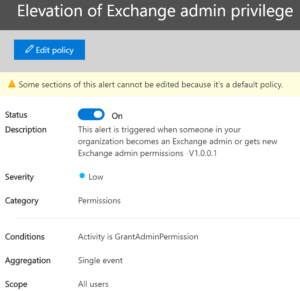
New administrator: How often do you create a new administrator of your exchange online environment? Almost never, so when it happens we want to know if that elevation was intentional or not.
Malware outbreak: When our users start getting a malware storm we want to know about. Depending on what exactly is going on we could use this information to warn our users.
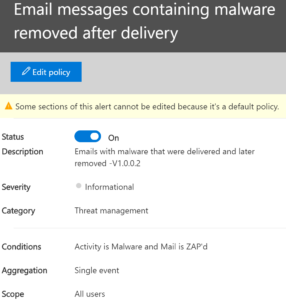
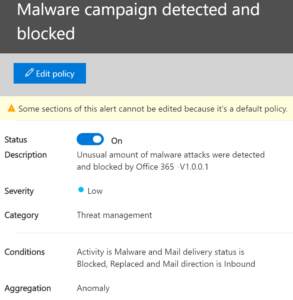
Users report bad email getting through: Above, we set up the ability for our users to report bad email to Microsoft. If they are reporting bad email we might want to adjust our filters. This alert lets us know that our users are getting mail that they shouldn’t be.
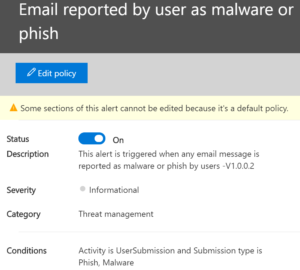
The above is a low-level alert, meaning that priority is set too low. But we have a high-priority alert when a bunch of people in the company are suddenly reporting phishing messages. This gives us the heads up that there’s a new phish method and it’s getting through.
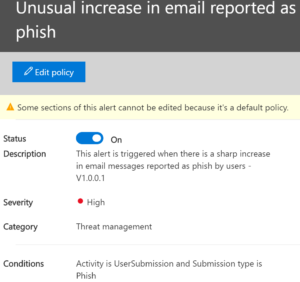
Sometimes email can get through the pre-delivery rules and later get removed. This is called the zap filter and this rule lets us know that it happened.
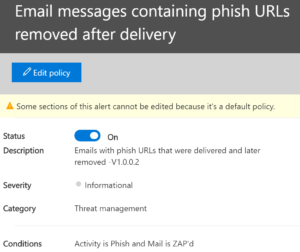
And what if someone clicked a rule that was found to be phishing? Hopefully, Microsoft’s SmartScreen caught it, but we need to know when a malicious URL was clicked. That it was detected and triggered this alert is a good thing but again this is our opportunity to let the rest of our user population know how to avoid it.
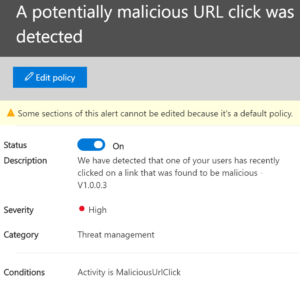
Email redirection has been setup: Above, we set up a policy to prevent mail from being redirected off the domain but what if it was attempted? We might have a breach going on and need to know about it. This alert does that for us.
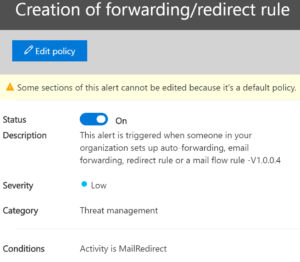
And this one lets us know if Microsoft blocked our user for similar activity.
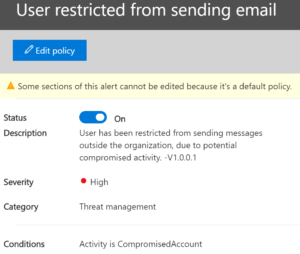
Reporting
Is your Microsoft 365 administrator properly managing your cloud email environment? It’s hard to know if you aren’t the administrator yourself. But you could ask for access to the management portal, which should allow you to review the reports. Here’s what you should be seeing at a minimum. The below results are for a seven person company. Multiply up for your company size.
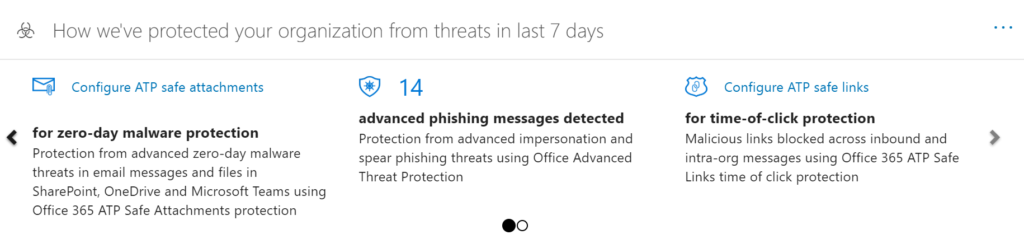
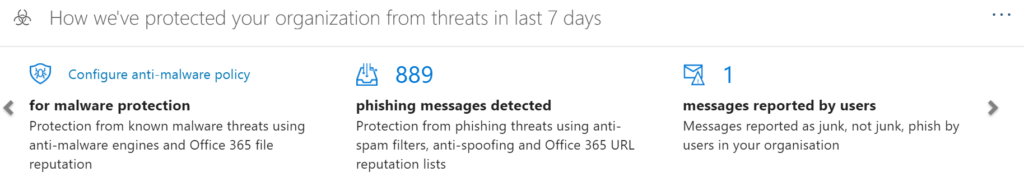
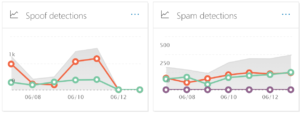
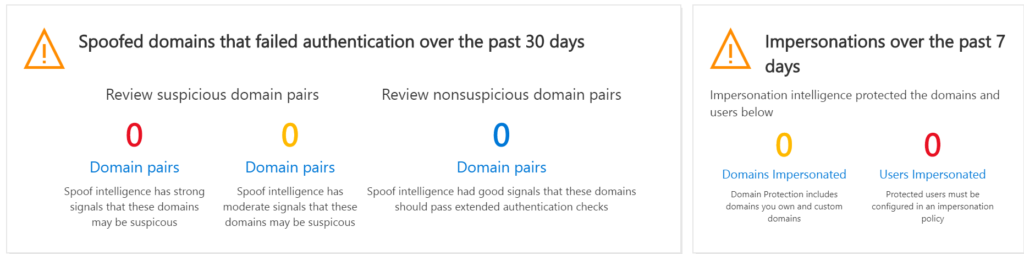
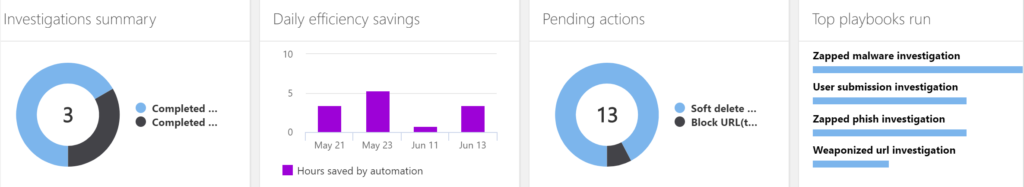
Cloud email security: Definitely not hands-off
There’s a lot that can be done to protect your cloud email environment. Just because your email infrastructure has gone to the cloud doesn’t mean that it’s hands-off now. In fact, it’s all hands on deck — and after reading this tutorial, your cloud email administrator has the toolset that’s needed to do the job right.
Featured image: Shutterstock




Block all executable attachments isn’t an option I even see in ECP when creating a new rule.
You need to click the More options button