People go to coffee shops like Starbucks or Peets for many reasons. For me, personally, it is for an overpriced cappuccino that tells the world I am an important guy and probably work on really lucrative projects.
That’s just me? OK then…
Besides ego boosts, a major reason people go to coffee shops is the free WiFi that students, writers, and countless other individuals use for convenience. For cybersecurity pros, public WiFi is a place we like to avoid. The possibility for malware infection and Man-in-The-Middle attacks are enough to keep us away from such networks.
Let’s imagine for a second, however, that you are an up-and-coming black-hat hacker. You want to do more than vandalize websites with ASCII drawings or hack your buddies on Facebook and change their relationship status to 10 years of being married to a goat. You want to do something that impresses your script-kiddie pals on IRC; something that says you have actual skill.
Packet sniffing undetected on a network may just be that thing do it.
This leads us back to the coffee shop WiFi. Today, you decide on Starbucks since the Pumpkin Spice Latte is now available. With how easy it is to simply gain access to the network, there isn’t a ton of hacking to be done. All you do is, according to the company’s official website, “select ‘Google Starbucks’ WiFi network, open a browser and click ‘Accept & Connect.’ Then you’re… ready to enjoy fast WiFi with your coffee.” Thankfully, the store is full of people just waiting to be cyber casualties via public WiFi. Places like Starbucks do not require a password for their WiFi, but even if they did and were running WPA-2 certifications, passive actions like packet sniffing can still yield results. Any traffic that is unencrypted (which is likely to be a great deal) will be captured by Wireshark.
Once you’re in, let’s say you want to do that thing called packet sniffing. First, you understand it’s illegal and you could go to prison for stealing data, but hey who cares about that? You want to be a 1337 h4x0r like in the movies. So to start your journey of hacking the planet, pull up everybody’s favorite sniffer, Wireshark. Since you have not discovered the beauty of Kali Linux yet, and because this hypothetical situation is made easier with it, you are using the Windows GUI version of Wireshark.
What you want to do is make sure that your version is the most up-to-date, which is 4.1.2, as other versions may be buggy. Running this packet sniffer is a bit of a pain on Windows, as you will find yourself limited to certain modes as others may require additional hardware to work properly. In any case, you can absolutely collect data packets using just the Windows version of Wireshark on a WLAN.
So you sit down with your latte and open Wireshark. The first thing you are going to want to do is go to the tab that says “capture” and select “options.” A window called “capture interfaces” will pop up, and at the bottom you will see the words “capture all packets in promiscuous mode.” Make sure the box next to it is checked as promiscuous mode ensures your interface will receive any packet sent, rather than just those intended for it.
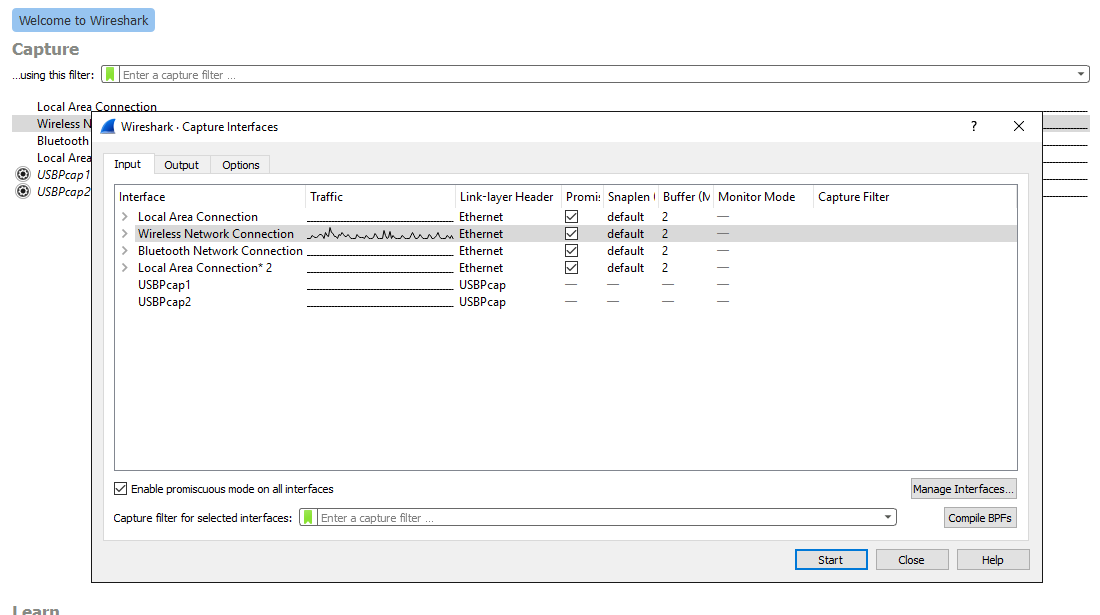
The actual packet capture process is ready to commence. Hit the “start” button with the “wireless network connection” option selected and watch all the data be captured by Wireshark. This is the easy part. The hard part comes later. When you feel that you have been running the packet capture long enough, simply hit the red square at the top of the page to stop the sniffing.

Now here comes the difficult part. You likely have a gold mine of data, possibly even passwords thanks to the unencrypted traffic, from the unknowing Starbucks’ patrons. The problem is, you are going to now have to sift through a ton of data packets to find something interesting. Thankfully, Wireshark makes it simple to isolate the type of data that you are looking for. To view these options, select the “analyze” tab and from the drop-down menu select “display filters.”
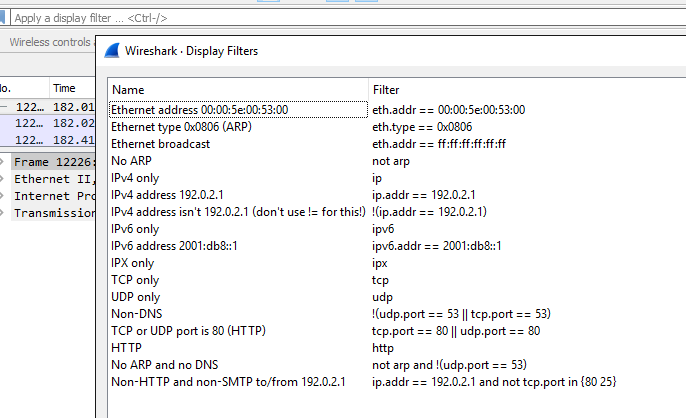
A tab will pop up with your options to enter into the bar that says “apply a display filter.” Start entering different filters into the white text bar that says “apply a display filter” and see what kind of data you captured. If you are lucky enough, there will be some rather juicy data that you can use against an individual in the coffee shop. Things like user names and passwords (even hashed ones that are easily decrypted by free services on the Internet) are obviously the holy grail, but be on the lookout for anything in plain text that can be useful. Not every website uses HTTPS, and if you get someone signing in on an HTTP site, you are likely going to get some great data.
Let’s say you get lucky and get somebody’s username/password combination by searching for POST submissions, or at least something that looks like it. With a simple search of the IP address listed in the “destination” column, you may very well have scored your first hack. After a bit of decryption, which is easily accessible from the Internet, you have a password that is fully ready to use.
Congrats, you will probably get arrested some day, but at least you can brag about this to your buddies in IRC. I look forward as a cybersecurity guy to bringing you down someday when you inevitably join Lizard Squad or some other collective. For now, finish that Pumpkin Spice Latte and walk out of Starbucks with the knowledge that you just hacked someone’s account thanks to Wireshark.
As you finish this article you are probably thinking, “Derek, you are a cybersecurity guy, why the hell are you teaching up-and-coming bad guys how to hurt innocent people?” Two main reasons. The first is to illustrate just how vulnerable any person can be on a public WiFi network and to discourage them from using it. The second reason is to show how major corporations often sacrifice security for convenience, leaving their customers worse for wear. Having WiFi that has no password, no encryption, or any other security measures that truly matter in place is a bad look for any organization.
And for the love of God, stay off of public WiFi!




Great article, for the lulz.
I cannot find other devices listen on arp-scan at local Starbucks.
Maybe we can have logless encrypted chat about how to resolve this.
“Angels: don’t play this ARP. . .”
LOL
Is there a way to do this on mac? if so what equipment do i need?!
If, hypothetically speaking you were to do this on mac, you’d just need the Mac version of Wireshark. It’s that simple. Just download the program for mac. The equipment you’ll need is a Mac. How have you not thought of this?
Kali Linux eh? I just installed it on a machine for dual boot, and I have found that we were made for each other, like we chose each other and I found my system!
Mind I’m so new to this all- but I’m learning at leaps and bounds. Thanks Udemy. Anywho, my question is thus- I learn by udemy, by reading and videos, but I learn a lot by doing, and shit- Mike Myers in his udemy course was talking about wireshark, so I downloaded it on my windows system before I even knew about Kali. I didn’t have a chance to use it. Then fast forward I got Kali, then I randomly discovered it had WS. Well I’m in a coffeeshop now ready to continue my course Python and Ethical Hacking and was thinking about running wireshark. Keep in mind I didn’t even find this article using the search terms Kali or Wireshark. That’s how coincidental it is. I was searching for whether it’s ok to ARP, because I was practicing changing my mac address, but when I do, it says I’m connected but I can’t load webpages, so I want to test the hypothesis I just read that I need to ARP the system and have it update it’s table, and I was wondering is this something I can do, legally or whatever. So I googled this and came to your page.
But now I have bigger broader questions- shit, if I opened wireshark, and ran it here- would I be THAT CLOSE already to gathering data and crossing over the legality lines? I just assumed first of all that I was a long way off from being able to do anything malicious effectively, and second I don’t want to do anything malicious and I definitely don’t want to get in trouble. And yet I love learning by experimenting so I definitely see this as being dangerous, a great way to wreck my career and cost me so I am just now having to consider all this, because the python course assumes we are using a virtual machine and our LAN I think is our host OS and the virtual box. I haven’t gotten that far in, but I am not doing it that way, in part because I only have 4GB ram and I hate those small windows. I want a real OS, I want Kali to live free. But I don’t want to really hack into public routers and switches and other computers on such LANs. This really helps clarify how things work though, which I love but this will have to be something I learn- how vulnerable others are but also how vulnerable I could be to crossing lines unintentionally. So I can’t even open up wireshark here in public and mess around? Sheet man, after a hard day’s work, innocent motives I came that close to trouble?
The older I get the more security minded I become btw. I love security in all its manifestations and freedom too and those are NOT mutually exclusive.
There was an app about 6 moths ago that i was using. It is basically wireshark with a GUI that aims only at facebook. IE, you go to starbucks, launch the app and before you know it, you have a bunch of usernames and passwords for facebook.
Does anyone know what app this is?
thanks
I have identified two people who sit in Starbucks and scan. What can I do about it? There is virtually nothing online about how to turn in people who scan and scam.
Packet sniffing is not illegal whatsoever. There was a significant court case involving the cars Google drives around to capture street view data for Google Maps. While they were driving around they were also collecting network traffic from unprotected wireless networks. This was deemed LEGAL by the courts. Public wifi in a coffee shop is considered PUBLIC domain – there is no expected privacy, just like any other public place. When you begin to steal passwords and use them in a manner that is illegal, like stealing credit card info and then using it or selling data online – then you have crossed the line to black hat hacker engaging in serious cyber crimes. Just thought I needed to clear this up because this post is erroneous.
can one use a roku at starbucks