Product homepage and free trial offer: click here

Encryption solutions such as BitLocker can go a long way toward making a user’s device more secure. At the same time though, a user who loses their BitLocker key may be locked out of their device. Specops is attempting to solve this problem with Specops Key Recovery. Specops Key Recovery can provide users with self-service key recovery services for both BitLocker and Symantec Endpoint Encryption. For this review, however, I will be focusing solely on BitLocker key recovery.
Installation process
Before I could install Specops Key Recovery, I had to create a customer account. The account creation process was relatively easy, and mostly just involved providing information such as the organization’s name and domain name, as well as the primary contact person’s name and email address. This process also required me to enter a mobile phone number. Upon doing so, Specops sent me a code via text message. This code is then used to complete the account creation process.
The next step is to download the Gatekeeper. As you complete this process, you must also make note of an activation code that you will use later on to activate the Gatekeeper. The actual installation process simply involves installing the administration tools and installing the Gatekeeper. This is an intuitive process that ends with activating the Gatekeeper using the code that you were given when you downloaded the Gatekeeper software. It is worth noting that this code expires 24 hours after it is issued, so you need to download the Gatekeeper at the time when you plan on installing it.
End-user experience
Before I show the administrative side of the Specops Key Recovery interface, I want to take just a moment and tell you about the end-user experience.
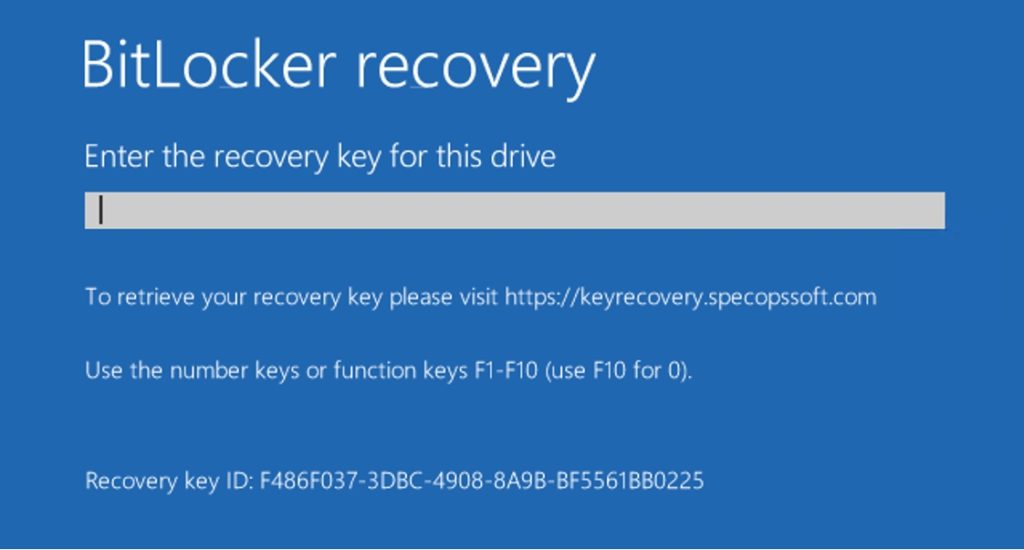
When a user has problems with accessing a BitLocker encrypted drive, they are taken to a screen like the one shown in the screenshot below. This interface is provided by Microsoft and allows the user to enter their BitLocker recovery key. Notice, however, that the screen now contains a message telling the user to visit keyrecovery.specopssoft.com to retrieve their recovery key.
When the user visits the URL listed above, they are prompted to log in using their username. Next, the user is taken to a multifactor authentication screen, similar to the one shown below. There is a lot more going on here than might initially meet the eye. I will talk about this screen in more depth a bit later on.

Once the user has been authenticated, they are prompted to enter the first eight characters of their recovery key ID. The recovery key ID is displayed on the Windows screen that prompts the user to enter their recovery key (it was the very first screen capture shown in this review). Upon entering this information, the Specops Key Recovery software retrieves the user’s recovery key, which you can see below. The user can then enter the recovery key into the Windows key recovery prompt, and regain access to their BitLocker encrypted drive.


Required authentication process
So now that I have shown you what the end-user experience looks like, I want to take a step back and talk about the administrative side of things. For Specops Key Recovery to work, a group policy setting has to be configured to store BitLocker recovery keys in the Active Directory. When a user enters their recovery key ID, Specops Key Recovery uses that recovery key ID to retrieve the recovery key from the Active Directory. Note that recovery keys are heavily locked down as such admins and helpdesk technicians would not have access to the keys in AD.
This raises the question of why anyone would want to invest in a third-party product simply to perform what amounts to an Active Directory query? However, there are two things that Specops Key Recovery has going for it. First, it gives the user the ability to perform self-service key retrieval. The administrator and helpdesk don’t have to get involved in the process. Second, Specops Key Recovery goes to great lengths to keep the recovery keys secure.
BitLocker is used to protect disk’s containing sensitive data, so if someone requests a BitLocker recovery key then you need to make absolutely sure that the person is who they claim to be. This is where Specops Key Recovery really excels.
As I briefly mentioned earlier, Specops Key Recovery makes extensive use of multifactor authentication. The entire process is based around a system of weighted authentication. The idea behind weighted authentication is that some authentication providers are more trustworthy or more secure than others. Requiring a user to enter a code that has been sent to their mobile phone, for example, might be considered to be a more reliable test of the user’s identity than simply requiring the user to enter their Windows password.
Before a user can use Specops Key Recovery, they have to be enrolled in the system. Or users can be pre-enrolled in the system depending on which authentication factors are enabled and if they rely on information stored in the users’ profile. An administrator can select a combination of authentication factors, assign weights to each, while setting a required weight for enrollment, and a required weight for authentication. These weights are expressed through a series of stars, as shown in the figure below.

As you look at the figure above, you will notice that there are a series of identity providers listed, and each one has a weight associated with it (usually either one or two stars) however administrators can configure the star value of authentication weight of each identity service. Based on the enrollment/authentication policy set by the admin, for a user to enroll in Specops Key Recovery, they must provide authentication information for several different identity services. The cumulative total number of stars for the identity services that the user selects must meet or exceed the number of stars that the administrator sets as the required weight for enrollment. As previously mentioned, an administrator can change the required weight for enrollment or authentication, and can also change the weight of any of the identity services.
One more thing that you will probably notice about the screenshot above is that there is a higher weight required for enrollment than for authentication. The reason for this is that it makes it possible for a user to be authenticated, even if there is a problem with one of the identity services that the user used when they enrolled. If a user forgets their secret question or accidentally leaves their mobile device at home, for example, they can still be authenticated by using a combination of other identity services. Specops Key Recovery doesn’t care which identity services a user uses during the authentication process, so long as those identity services collectively meet the required weight for authentication.
The verdict
Whenever I review a product on this site, I like to conclude the review by giving the product a star rating ranging from zero to five stars, with five stars being the highest possible score. With that said, I decided to give Specops Key Recovery a score of 4.5 stars, which is a gold award.
Overall, I think that Specops Key Recovery is a really great product that will go a long way toward helping organizations prevent BitLocker-related data loss. At the same time, though, I ran into a couple of minor issues during the initial deployment process (such as an expired authentication code and a Gatekeeper that at first did not want to connect to the cloud). In the grand scheme of things, however, these issues were very minor and I would not hesitate to recommend Specops Key Recovery for use in any organization that uses BitLocker encryption.
Rating 4.5/5


