Keeping an organization’s IT resources secure is an ongoing challenge, and recent high-profile hacks and ransomware outbreaks have upped the stakes. Administrators are under more pressure than ever to make sure that network endpoints adhere to the organization’s established security protocols. One way in which you can make sure that your Windows desktops are properly configured is to leverage security templates. The idea behind a security template is really simple. An administrator builds a security template that defines all of the security settings that are required to be used throughout the organization. Then, whenever a PC’s security settings need to be validated, they can be compared against the security template. Doing so makes it really easy to find and remediate deficiencies. Best of all, everything that you need is natively built into Windows 10 (as well as several earlier versions of Windows).
Creating security templates
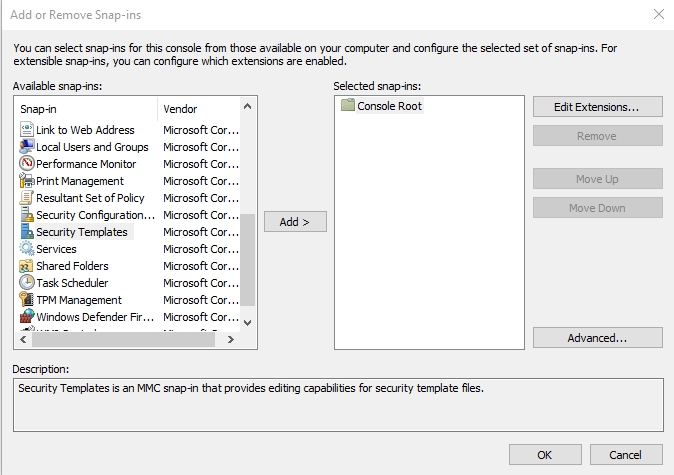
Before you will be able to use templates to enforce security, you will need to create a baseline security template. To do so, open the Microsoft Management Console by entering the MMC command at the Run prompt. When the console opens, choose the Add / Remove Snap-In command from the File menu. Now, select the Security Templates snap-in, which you can see in the figure below, and click Add, followed by OK.
Once the Security Templates snap-in has been loaded, it is time to create a template. Navigate through the console tree to the template path, right click on the path, and then choose the New Template command from the shortcut menu. When prompted, enter a name for the template that you are creating. You can see what the newly created template looks like in the figure below.
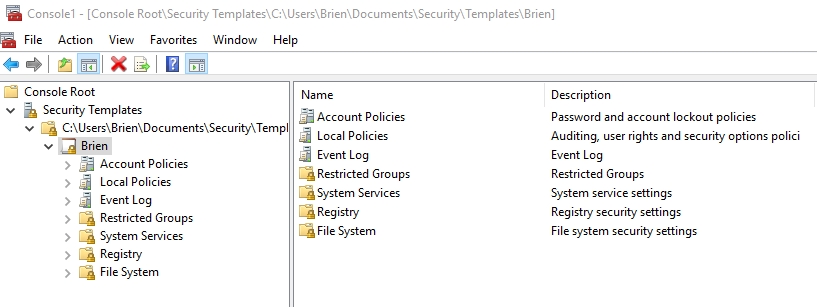
As you look at the figure above, you will notice that the console looks a lot like the Group Policy console. This is not a coincidence. Most of the settings that are available within the local security policy also exist here. Remember, the local security policy is used to lock down the OS, but the security templates are there to make sure that the OS stays locked down. Therefore, you should configure the account policies and local policies so that they mimic the settings that you apply through the local security policy.
In addition to the basic account policy and local policy settings, there are five other types of policy settings that you can implement. These include:
- Event log — Event log settings are used to retain and/or restrict access to security logs, as well as defining the maximum log size.
- Restricted groups — Restricted group settings are used to define which security groups should be restricted.
- Registry – Registry settings are used to define specific registry keys that should exist within the Windows operating system.
- File System — The file system settings are used to define the Access Control List (ACL) entries that should apply to specific files and folders.
When you finish defining security settings, right-click on the template that you have created and select the Save command from the shortcut menu to save your changes.
Auditing a PC’s security configuration
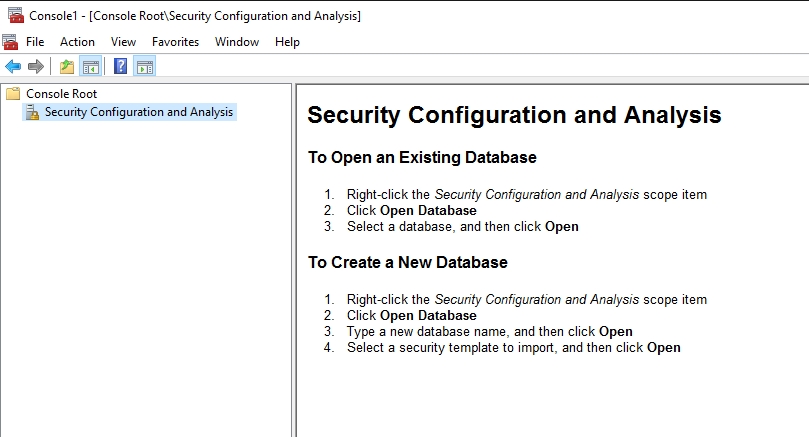
Once you have created a security template, you can use that template to audit a PC’s security configuration. To do so, open the Microsoft Management Console and select the Add / Remove Snap-in command from the File menu. When Windows displays the list of available snap-ins, select the Security Configuration and Analysis snap-in, shown below, and then click the Add button, followed by the OK button.

The first thing that you will need to do after loading the snap-in for the first time is to create a database. As you can see in the figure below, you can create a database by right-clicking on the Security Configuration and Analysis container, choosing the Open Database command from the shortcut menu, and then typing a name for a new database. When you use this tool in the future, you can reuse the database that you are creating now.
At this point, you will be prompted to load a security template for analysis. Select the security template that you had previously created, and click Open. Once you have imported the template, the tool is ready to use.
You can use the Security Configuration and Analysis tool to either configure a computer or to analyze a computer. For established Windows PCs, you will probably want to perform an analysis. To do so, right-click on the Security Configuration and Analysis container, and select the Analyze Computer Now command from the shortcut menu. When prompted, enter the desired log file path, and click OK.
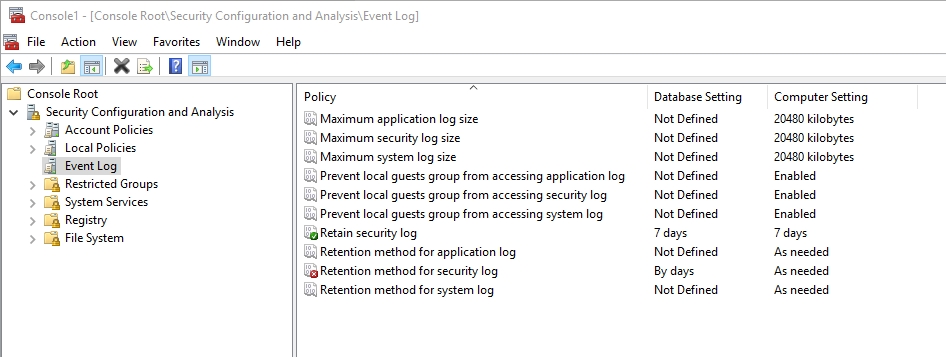
When the analysis finishes, you can review the log file or you can browse the console. As you can see in the figure below, the console allows you to compare the template settings against the computer’s settings. As you look at the figure, pay attention to the icons associated with the policy setting. A green icon indicates that the setting is defined within the template, and the PC is compliant with that setting. A gray icon indicates that the setting is undefined in the template, and a red icon indicates that the setting is defined within the template, but the PC is not compliant with that setting.
A powerful tool
As you can see, security templates are a powerful tool for finding and resolving security configuration drift. If you want to automatically fix any discrepancies that may exist between the policy and the PC’s settings, then you can right-click on the Security Configuration and Analysis container, and choose the Configure Computer Now command from the shortcut menu.
Photo credit: Shutterstock




Can the DB be easily moved/exported to an external drive?
Is this something that can realistically be used on Win 10 Home? It would be nice to setup a DB then be able to distribute/share it with Home users to automate configuring their machines.
I am specifically concerned about the policy portion, since Home users can’t manage policies. Is this a back door to policies, bypassing GPEdit?
Does anyone know why the “System Services” that populate in the template do not come across in the Analyze phase? They work properly in Server 2012 but not in Windows 10.