If you have been in the IT industry for some time or have been following our site, SSH protocol and SSH keys are words you’re sure to have come across often. So, what are these SSH keys, why do you need them, and how can you set them up? Let’s get answers to all these questions in this article.

SSH protocol
Before we jump into what SSH keys are, let’s understand the SSH protocol.
Secure Shell (SSH) protocol is a set of rules or methods for secure remote login from one computer to another. It lays the foundation for strong authentication and security while remotely logging into a computer.
This protocol was born out of the need for a secure way to remotely log in, as the existing ones such as telnet and rlogin were not secure.
SSH protocol works in a client-server model and uses public-key cryptography for authentication. Essentially, the SSH client initiates the connection to the SSH server. Once the connection is set up, encryption and hashing algorithms are used to exchange data between the client and the server.
Broadly speaking, the SSH protocol uses three kinds of authentication at different points of authentication and data transfer to ensure security, and these are:
- Symmetric keys
- Asymmetric keys (public-private keys)
- Hashing algorithms
Out of these, the most common and popular one is the public-private key encryption. In this form of encryption, there is a private and public key pair, and the public key is configured on the server to grant access to the user who is logging in from a client computer. The server sends the public key and if it matches with the private key pair present in the client, that user is granted remote access.
Obviously, the main use of this authentication is to ensure security. It can also be used for automation and to enable a single sign-on by administrative users.
What are SSH keys?
Now that you have an idea of the SSH protocol, it is relatively easy to understand where the SSH keys fit in.
In its simplest form, SSH keys are the private-public key pair that provides the access credentials for the SSH protocol. Its function is similar to usernames and passwords, except that it is mainly used for automated and single-sign-on.
These SSH keys always come in pairs and consist of a public and private key. When both the keys remain with the user, they are called user keys. Similarly, when these keys are on a remote system, they are called host keys.
There is another kind of SSH key called the session key that applies to just one session. This session key is highly useful to transmit large amounts of data securely.
How do SSH keys work?
The private key of this pair remains on the user system that is used to access the remote system. It is also used to decrypt the information sent by the remote system. Needless to say, this is the more important and secure of the two keys, and must never be shared. Most times, it is stored in an SSH key management software, though it can also be saved in a file.
The public key, on the other hand, is used by the remote server. It is used to encrypt information and can be shared with anyone because knowing the public key does not help without the private key. For the same reasons, these keys are stored in a file and no specialized tools are necessary to mask them.
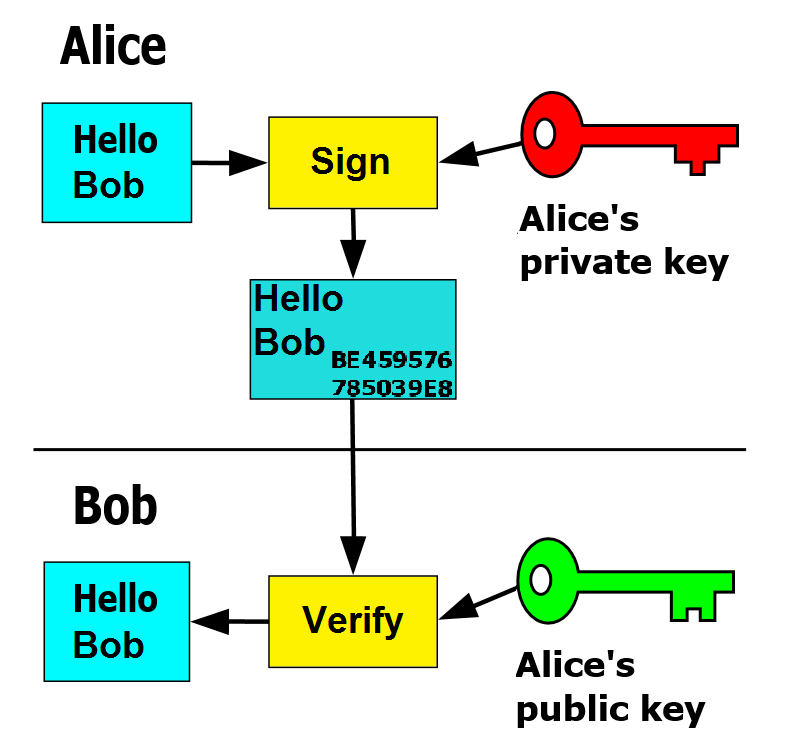
Now, let’s move on to understand how these keys work and how to set them up.
How to set up SSH keys?
Here is a step-by-step guide on how to set up these SSH keys on your computer.
Generate your pair of SSH keys
The first step is to generate your own SSH keys. Let’s briefly see how you can do it.
- Open the Terminal and type ssh-keygen -t rsa. This command starts the key generation process, and next, it prompts you to choose the location for storing these keys.
- If you’d like to go with the default location, press Enter.
- Next, you’ll be prompted to enter a passphrase.
- You can enter a phrase or simply accept the default one by pressing Enter.
- Once you confirm, the system automatically generates the key pair.
When you accept the default values, your private key will be stored in the id_rsa file in the .ssh directory while the public key will be stored in the id_rsa.pub file.
Here is another way to create private and public keys separately.
Type this command:
openssl genrsa -out private.pem 2048
This will generate a 2048-bit private key.
Create the corresponding public key with this command:
openssl req -new -x509 -key private.pem -out cert.pem
To check if the keys have been created successfully, type ls and see if the files are present in the directory.
A word of caution here. Never share your private key with anyone.

Import your SSH public key
After you generate the SSH keys, import the public key to the server. To do this,
- Copy the SSH public key.
- Go to the account page of your service provider and navigate to the “Import Public Key.”
- Paste your key in the public key field of your service provider’s account<./li>
- Give a name for the key in the “Key Name” field.
- Though it is not necessary to give the key a name, it’s a good practice.
- Finally, click the “Add” button, and the keys will get added to the SSH table.
With this, you’re all set.
Do a final check
Finally, check if everything works.
- Open your terminal and enter your SSH username along with the IP address of the remote system in the format ssh [email protected].
- This will initiate a connection with the remote system through the SSH protocol.
- The server will look up the public key in the SSH table. It will pick the public key associated with your username, will encrypt a random message using this key, and will send it back to the client.
- The client computer decrypts this message using the private key and combines it with the session ID. This concatenated message is encrypted and sent to the server.
- The server decrypts with the public key, and if the message matches, access is given to the user.
This establishes the remote connection and you can securely send messages to the remote client.
An ending note on SSH keys
These SSH keys can become unwieldy quickly, especially in the case of large organizations that may have to use millions of keys to grant access to different digital resources.
Research shows that the chances for security vulnerability increases when these keys are not well-managed, so consider using an SSH key management tool that can help IT admins to stay on top of SSH keys and their use.
So, have you implemented SSH keys? Please tell us about your experience in the comments section.
Featured image: Pixabay



