A VPN is one of the most popular tools for allowing users to work remotely. While there are numerous third-party VPNs available, you can also configure Windows Server to act as a VPN. In this article, I will show you how to configure Windows Server 2019 to act as a VPN server.
Before I begin
Before I get started, there are two things that I need to quickly mention. First, the procedure that I am about to show you is not the only way to set up a Windows Server VPN. I intend to make the process as simple as I possibly can for the benefit of those who have never done this before.
The second thing that you need to know before getting started is that the VPN server will need to be equipped with two network interfaces. One of these interfaces will handle inbound traffic and must be connected to the Internet. The other interface will be connected to your internal network.
Windows Server 2019 VPN configuration process
The first step in this process is to use Server Manager (or PowerShell) to install the Remote Access role, shown below. You don’t have to worry about installing any additional roles of features, but when you arrive at the Role Services screen, you will need to select the DirectAccess and VPN (RAS) service and the Routing service, along with the supporting features that are recommended by Windows.


When the role and feature installation process completes, go ahead and close the wizard. Next, click on Server Manager’s Notifications icon. When you do, you will see a message indicating that post-deployment configuration is required. Click on the Open the Getting Started Wizard link.
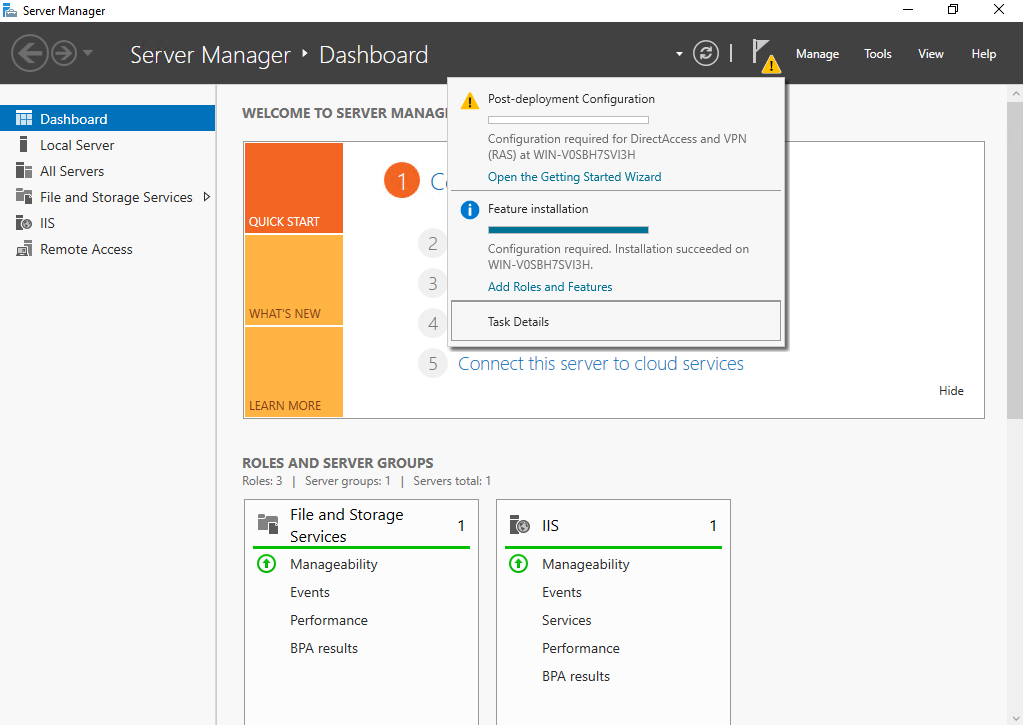
At this point, you will see a screen asking you how you wish to configure the server. In the interest of keeping things simple, go ahead and choose the Deploy VPN Only option. When you do, Windows will open the Routing and Remote Access console. At this point, you will need to right-click on the listing for your server within the console tree, and then choose the Configure and Enable Routing and Remote Access option from the shortcut menu, as shown below.

Windows will now launch the Routing and Remote Access Server Setup Wizard. Click Next to bypass the wizard’s Welcome screen, and you will be taken to a screen asking which service you wish to configure. The appropriate selection will vary based on your use case. However, if your goal is to enable basic VPN capabilities, then you should choose the Virtual Private Network (VPN) Access and NAT option.
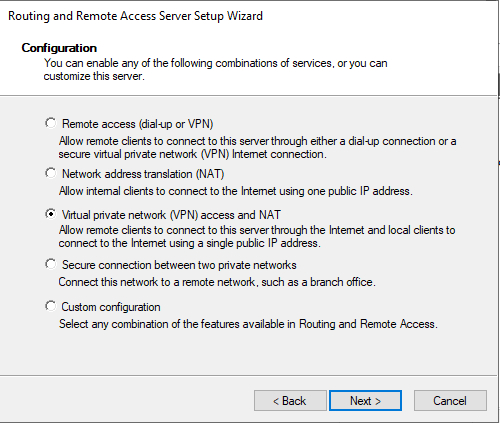
The following screen asks you to choose which interface connects to the Internet. This is the interface through which clients will connect to the VPN server.

Now, choose whether you want to provision clients with IP addresses automatically (from a DHCP server, or from a dedicated address pool). Make your selection and click Next.
Click Next, and you will be asked whether you want to use a Radius server to authenticate remote access requests. Choose No to allow the VPN server to authenticate authentication requests on its own. Click Next, followed by Finish. When you do, you may see a message telling you that you need to manually open the necessary firewall ports. Be sure to do this if necessary.
Testing your VPN
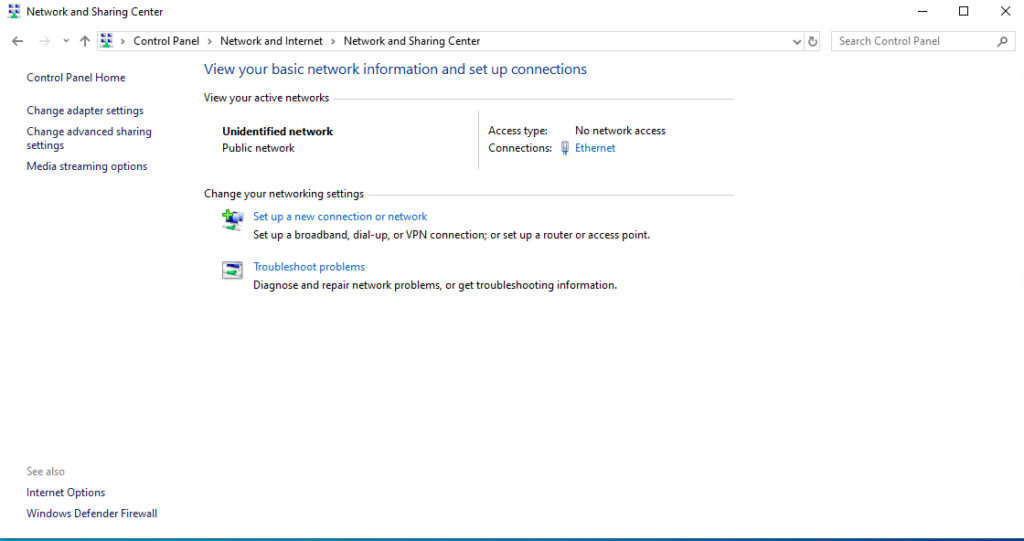
Before you will be able to test your VPN server, you will need to grant one or more users permission to access the server remotely. Once you have done that, you should be able to connect to the VPN server from a Windows 10 client. To establish VPN connectivity, open the Windows Control Panel and then click on the Network and Internet option, followed by Network and Sharing Center. When the Network and Sharing Center opens, click on the Set Up a New Connection or Network link. On the following screen, choose the option to connect to a workplace.
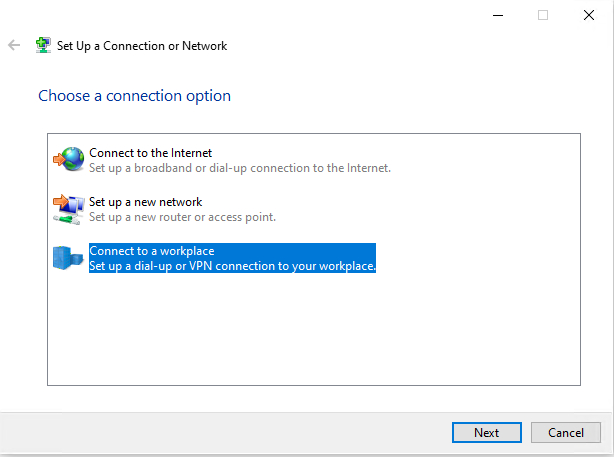
The following screen will ask you if you want to use your Internet connection, or if you prefer to dial directly into the VPN server. Choose the Internet option.
At this point, you should be taken to a screen that asks for your VPN server’s Internet address. You can populate this field using either a DNS name or an IPv4 or IPv6 address. You will also need to provide a name for the connection that you are creating. Click the Create button to create the VPN connection.

Now, go back to the Network and Internet screen within the Control Panel. Click on the Network and Internet link, followed by the Network and Sharing Center link. Click on Change Adapter Settings, and you should see an icon representing your VPN connection. Right-click on this icon and then choose the Connect / Disconnect option from the shortcut menu. When prompted, click on the connection within the pop-up, and then provide your authentication credentials. The client should be able to connect to the VPN that you have created.

Don’t forget about security
As you can see, it is relatively easy to configure Windows Server 2019 to act as a VPN. Even so, it is important to keep in mind that there is a lot more than you can do concerning security. For this article, I wanted to keep the configuration process as simple as I could for the benefit of those who have never configured the Windows Server Routing and Remote Access Services before.




Nice article.
I’m actually already running RRAS in a Windows 2019 environment and the remote users are using the built-in Microsoft VPN for Windows 10 clients (SSTP) and L2TP for Mac clients.
I’m wondering if you have any advise in implementing 2FA for RRAS, preferably with TOTP like Google Authenticator with those built-in VPN clients.
My research has come across Radius-based solutions (e.g OpenOTP, Duo, Okta, miniOrange), but they all seem to require some sort of workaround for how the user have to enter the OTP token due to the fact that the built-in VPN clients don’t support second-phase challenge. Unable to prompt for the 6-digit token, in other words. The workaround seems to require the user to enter a concatenated AD Password + the OTP token.
Knowing my users, this workaround is probably not ideal.
Can you confirm that this is the case, and would you know of an alternative (perhaps more elegant) solution if we want to keep using the built-in VPN clients? I realize that the limitation rests with the VPN clients, but I can hope.
Regards, Immanuel
Any tips on how to speed up the VPN connection? We had a Comcast line with 200Mbps down and 35Mbps UP and it pretty much maxed out at 5Mbps. Now we a ATT Fiber 1Gig up/ down connection and it didn’t change the speed.
Thanks!