Quick Fix: Block Installation of Bogus Toolbar from Fake Google Spam
By Thomas W Shinder MD, MVP
Got questions? Discuss this article over at
http://forums.isaserver.org/ultimatebb.cgi?ubb=get_topic;f=33;t=000031
On Tuesday of this week (August 23, 2004) I received a spam that for some reason wasn’t caught by any of the spam whackers in my four tier inbound SMTP server relay. This spam was different enough from the usual spam that it made me give it a second look before deleting. It was an HTML message (yes, I still accept HTML mail!) and at the top of the message was the Google logo, complete with the trademark symbol. The body of the message goes like this:
“Are you tired of pop ups and spy ware [sic]?
It can be one of the most frustrating experiences you encounter while surfing the web. Constantly having to close the pop up windows that appear non stop. Well with our free toolbar you can instantly get rid of
- All Pop Ups
- Spy ware [sic] that tracks your every move while you surf
- Cookies which also track where you go on the net
Plus, our toolbar does so much more. You will love surfing without worrying about who is watching you do what. And the best part is that it doesn’t cost you one penny. That’s right……its 100% FREE to you. So, go ahead and CLICK HERE to download your free copy today.
Thank you for searching with Google”
You can see the original messages here:
Html email: http://footon.jheslop.com/block%20all%20popups.html
txt email: http://footon.jheslop.com/block%20all%20popups.txt
The message implies that when you click the CLICK HERE link that you’ll download the Google toolbar. Of course, no where in the message did they actually say that you would download the Google toolbar, all they mention is “our toolbar”, whoever they are.
The funny thing about this message was that the FROM: address was from some user account at an East Indian ISP. Why would Google delegate sending toolbar offers to such a user account? No reason that I can think of so I deleted the message figuring it was some kind of scam, NOS (not otherwise specified).
Today Jim Harrison brought to my attention that this e-mail message is more than a generous offer to distribute the Google toolbar. In fact, the CLICK HERE link points to an executable named valuebar_setup.exe.
After being alerted to this by Jim, I fired up a couple of machines on my VMware network to see what happens when you install this thing. If you click the link in the fake Google spam, you’ll see in the ISA management console’s real time log viewer the get request for the scumware.
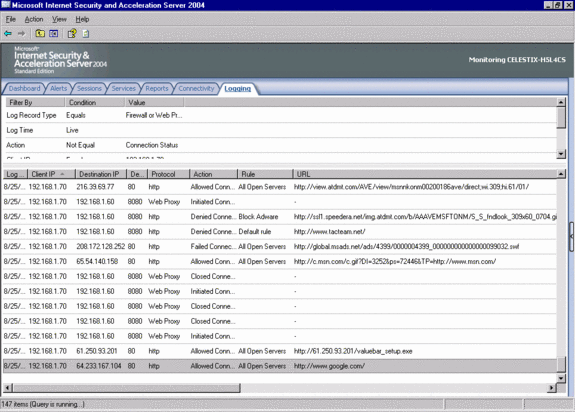
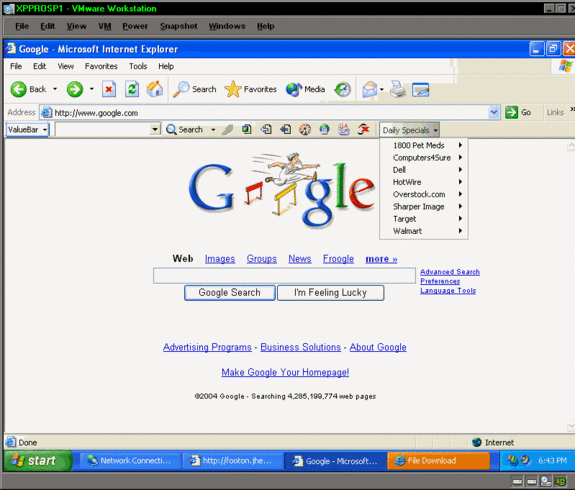
You’ll be taken to the Google home page after the scumware installs. Hey, wait a minute! That isn’t the Google toolbar. It says ValueBar on the left side. There is also a drop down list of Daily Specials and lists some well known commercial Web sites. I sure hope that these large vendors aren’t knowingly supporting the surreptitious installation of browser hijacking scumware.
I browsed a few Web sites and nothing unusual seemed to happen. Then I went to www.drudgereport.com and look at what I saw. Seems that I’ve won something, and even some money. Unfortunately the morons who work with the scumware developer forgot that the dollar sign goes before the number 😉 Maybe they meant to put the ¢ sign instead.

Of course I clicked Cancel and the scumware was kind enough to take me to a scumsite, as seen in the figure below.

Because the Google logo engenders a lot of trust in the Internet community, there’s a high likelihood that your users are going to click the link and get infected with application. Better to stop this criminal enterprise in its tracks and take advantage of the ISA firewall’s strong stateful application layer inspection mechanisms.
You can manually configure all your HTTP Security Filters for all your rules allowing HTTP, or you can do it the easy way. Just head on over http://isatools.org/block_fake_google.vbs can grab Jim’s script. Copy it to your ISA firewall (you’re going to copy it because you NEVER run the browser on your ISA firewall) and run it. Of course, you need a 2004 ISA firewall for this to work because the ISA Server 2000 firewall doesn’t have an HTTP Security Filter.
Jim’s script adds two signatures that block access to the scumware. There is a signature that applies to the Request URL and another applying to the Response body, as seen in the figures below.

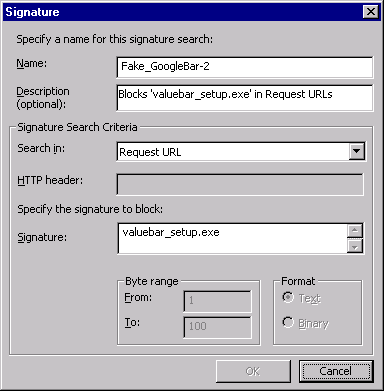
Hat’s off to Jim Harrison for the heads-up and script!
I hope you enjoyed this article and found something in it that you can apply to your own network. If you have any questions on anything I discussed in this article, head on over to http://forums.isaserver.org/ultimatebb.cgi?ubb=get_topic;f=33;t=000031 and post a message. I’ll be informed of your post and will answer your questions ASAP. Thanks! –Tom
If you would like us to email you when Tom Shinder releases another article on ISAserver.org, subscribe to our ‘Real-Time Article Update’ by clicking here. Please note that we do NOT sell or rent the email addresses belonging to our subscribers; we respect your privacy.




