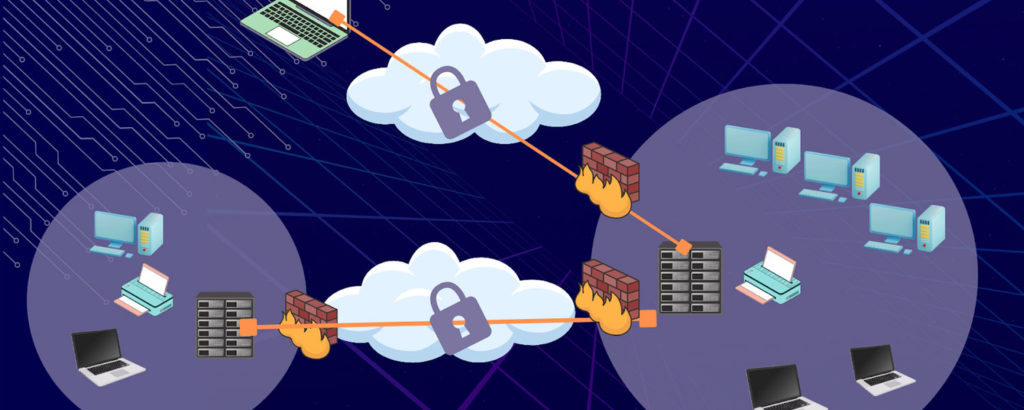
Top 11 Must-Have VPN Features for SMBs
SMBs can find the most value in a VPN if they look for certain key features. In this article, we’ll talk about the top 11 VPN features most suited for SMBs. We’ll cover features such as secure VPN protocols, DNS leak protection, static IP addresses, router support, and more.