If you would like to read the next part of this article series please go to Collecting Threat Intelligence (Part 2).
Introduction
Those defending the network are at a significant disadvantage when attempting to secure a network against potential attackers. Attackers have days, weeks, months, or even years to perform research on their target. They can perform web-based reconnaissance, participate in social engineering efforts, and even dumpster dive to find out critical information about your network. All of this research may lead up to a single event that leaves your network compromised in a matter of minutes.
As a defender, we are often blind against the reconnaissance that attackers perform whilst preparing for an attack. If the potential intruder is on top of his game then he will leave no traces of his activities in any of the log files on your systems. However, attackers are human (sometimes), and even the best can slip up and spew out a few accidental packets or forget to proxy their traffic through a third-party system.
When this occurs it means that the attacker leaves an artifact somewhere on your network. This artifact is typically an IP address or domain name, and it can be the key to preventing an attack before it occurs, stopping an attack in progress, or finding a culprit post-exploitation.
Defining Threat Intelligence
When discussing threat intelligence as it pertains to a computer network it is important that we define some terms in order to better understand the factors that come in to play.
A threat is defined as the potential danger to a network resource. Whenever you find an anomalous IP address in a log file or IDS alert, that IP address represents a potential threat. Our goal is to determine if a threat can be tied to a particular threat agent. A threat agent is an individual or group that can manifest a threat. Putting the two terms in perspective, consider a scenario where a system is unpatched. There is a threat that this system will be compromised (the probability that this system will be compromised is defined as risk). In order for this threat to be manifested, a person or group (the threat agent) must exploit a vulnerability in the system. There are entire books devoted to defining these terms and the differences between them, and I’m sure someone would slightly disagree with my definitions, but they should suffice for our purposes here.
The magic formula for determining a threat agent is Threat Agent = Capabilities + Intentions + Past Activities. When looking at an artifact in a log file your goal is to build intelligence on this potential threat so that you can fill in the pieces of this equation.
A Word of Caution
Before I begin discussing different methods for collecting intelligence on IP addresses and DNS names it’s important to write a word of caution. I’ve heard it stated many different ways, but nobody says it better than Mike Poor, one of the Founders of the Inguardians security firm and a SANS Instructor; “In all cases, it’s never a good idea to invite an attacker to dance.” When you are dealing with a potentially hostile entity, the last thing you want to do is make them aware that you are aware of their presence. If an attacker is performing recon on your network and then they notice your IP address touching one of their DNS servers or border firewall then that attacker is likely to know that you are aware of their presence. At the very least they may change their tactics or their IP address, invalidating any research you have already done. In a worse scenario, this may cause an attacker to become more aggressive and increase their efforts, or even deploy some form of denial of service attack.
The simple fact of the matter is that most of the time you have no idea who you are going up against and it’s generally a good idea to not let them know you are watching them until you have to. That being said, the techniques discussed in this article are mostly passive, but for those that aren’t I recommend using some form of anonymity whether it be an SSH tunnel to a third-party host or something like Tor. I’m only going to cover each of these techniques briefly so before you use them against a hostile IP address from your network make sure you know the details of how they work by taking some packet captures of the traffic each one generates.
WHOIS
When a potentially hostile host is encountered the first question that is typically asked is in regards to the physical location of its source. With the distributed nature of the Internet it’s nearly impossible to geo-locate an IP address if attacker takes the proper precautions. However, in the case of careless or less sophisticated attackers you can often get the information you need by doing a simple whois query.
A whois query can be performed on either a domain name or an IP address. These can both be done via the command line but I prefer to do them through third party websites for the sake of anonymity. One such website is whois which provides a variety of domain and IP address research tools.
Domain WHOIS
Doing a whois query for a domain from the main page of whois.net will yield the registrar used to register the name, the name servers associated with the domain, the date the domain was registered, and in some cases the contact information of the person who registered the domain. Although whois.net provides some information, if you want to find the bulk of the information associated with a domain registration you are best doing a search from whois.net, finding who the registrar is, and then performing a search using that registrar’s whois database. For instance, if the domain is shown to be registered through GoDaddy, you will find additional information for the domain listed when you perform a whois from GoDaddy.
Also keep in mind that some registrars offer services designed to mask the information of the true owner by replacing it with that of the registrar. This may prevent your domain whois from turning up useful results.

Figure 1: This domain whois for Google provides basic registration information
IP WHOIS
Querying an IP address is done by performing a whois query to one of the five regional Internet registries (RIRs). These registries are designated by the Internet Assigned Numbers Authority (IANA) to manage all of the IP address assignments for their specific geographic location. You can perform a query by going to the website of each individual regional registry, as shown in the table below. If you don’t know which region the IP address is from you can start with the registry for the region you are in, and if the IP address doesn’t belong to that region then you will be pointed to the correct registry.
|
Regional Internet Registry (RIR) |
Locations Served |
Whois URL |
|
AfriNIC |
Africa |
|
|
APNIC |
Asia and Pacific |
|
|
ARIN |
United States, Canada, North Atlantic Islands |
|
|
LACNIC |
Latin America |
|
|
RIPE NCC |
Europe, Central Asia, and the Middle East |
The information garnered from an IP whois includes the company that the IP is registered to, the block of IP addresses allocated to the company, and contact information for the address. If the IP address belongs to an individual or a smaller company then it is likely that the whois will return information for the ISP that owns the IP block, and any abuse or malicious activity would require the ISPs cooperation to locate the at-fault individual or organization.
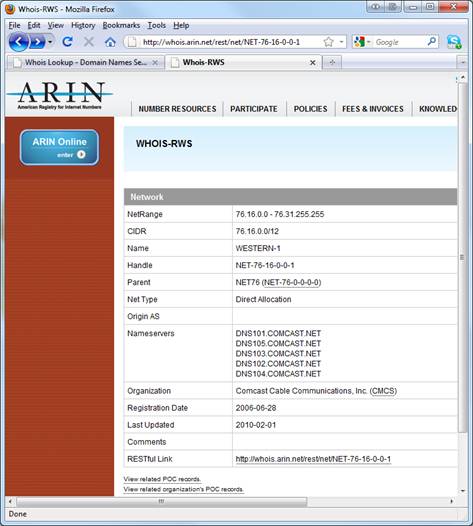
Figure 2: The IP address whois shows that this IP address belongs to an ISP
Domains by IP
One of the most useful pieces of information you can collect from an IP address are the domains names that are hosted on it. A great passive method of doing this is by using this site. You simply enter the IP address and the website will provide you a list of the domains hosted on the IP. This list can be exceedingly useful when researching known malicious domains.
Known Malicious Domains
The best thing you can hope to do is stumble upon an artifact that has already been identified as malicious by another party. A great way to do this is to use a couple of my favorite websites that compile such information. The first is the Malware Domain List, located here. MDL contains a list of IP addresses and domains that have been reported for malicious activity, and namely, hosting malware.
Another favorite intelligence site of mine is ThreatExpert. ThreatExpert allows users to submit malware for analysis. This analysis provides details of the malware along with the associated domains and IP addresses the malware uses for distribution and communication. Using this site you can plug in any anomalous IP addresses or domain names you may have to see if any of the indexed malware is related.
These two sites are primarily useful if the anomalous IP or domain is the result of some type of automated malware or botnet activity, but none the less I almost always plug data into both sites immediately once it’s been deemed anomalous. If you have a done a Domain By IP search as discussed in the previous section it’s also a good idea to feed those additional domain names into the search to see what you can find.

Figure 3: A simple ThreatExpert report on a FakeAV Variant
Conclusion
In the first part of this article we’ve discussed a few basic searches you can perform to build intelligence on a potential threat agent. In the second half of this article I will discuss a few more resources for threat intelligence. I’ll also provide some tips for getting the most out of Google and ensuring that you are doing it safely.
If you would like to read the first part of this article series please go to Collecting Threat Intelligence (Part 1).



