In the article series “Configuring Granular Password Settings” (part 1 & part 2) we demonstrated how to configure Granular Password Settings for individual users or global security groups in a Windows Server 2008 Active Directory environment, using built-in methods. This article will demonstrate “The Easy Way” of how to handle these additional password policies in your Windows Server 2008 domain environment.
Different approaches
Like with many other areas of Windows administration you have several different options when it comes to handling the new password policies, their settings and who is affected by them. The built-in possibility, utilizing tools like ADSIEdit, may not be the best option for inexperienced helpdesk personnel, overtired administrators or clumsy consultants like myself – we need better tools, preferably with a neat graphical user interface (GUI) to do the job, nice and safely! Others may claim that we need scriptable solutions to do the job – everybody is talking about PowerShell these days, right? Luckily some cool & free tools have arrived already – before Windows Server 2008 is even released – all of these tools provide us with both PowerShell command-lets (CmdLets) and a nice GUI on the top!
In this article the main focus will be a free utility from Special Operations Software called Specops Password Policy Basic – this tool is a feature limited version of Specops Password Policy. There are of course other possible solutions and some of them will be mentioned in the end of this article.
Specops Password Policy Basic
First thing you need to do is to go and grab the download from the Specops website – you will have to register yourself on the webpage to get hold of the product (a fair deal if you ask me). The tool requires Microsoft .NET Framework 2.0 and Microsoft Management Console (MMC) version 3.0 to be present on the machine on which the product is installed. In my case I have used Microsoft Windows Server 2008 (the RC1 beta version).
During installation you can choose to install the Specops Password Policy Basic MMC snap-in and/or the Windows PowerShell CmdLets – default is to install both components (which will be fine for most scenarios). After installation you will have a new MMC Snap-in available shown in Figure 1.
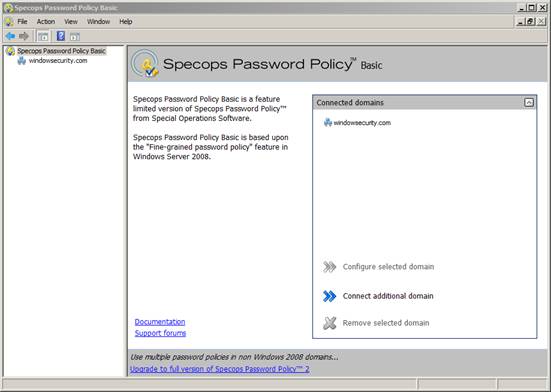
Figure 1: The MMC Snap-in overview
As you can see the snap-in is capable of connecting to multiple domains, in my case I’m connected to the windowsecurity.com domain.
When clicking the domain node in the left margin we get to a great overview of the password policies currently present in the domain. This includes the precedence order, the password policy name(s), top 5 settings (minimum length, complexity requirements, minimum age, maximum age and history settings) and a quick view of policy members (users or global security groups).
Besides from that we have the option to create a “New password policy”, “Edit selected password policy”, “Delete selected password policy”, “Lookup password policy for user” and “Lookup users affected by selected policy” – please see in Figure 2.

Figure 2: The password policies present in the domain and our options
In my case I have selected a password policy for “Helpdesk Employees,” in the “Members of the selected password policy” table I can see the relevant users and/or security groups. By using the Up/Down arrows you can set the precedence order of the password policies very easily. Please note that you can also get a quick glimpse of the Default Domain password policy (normally defined within the Default Domain Policy GPO) – as previously recommended this should be a very tight password policy to make sure all users are in the correct security group(s) and if not they will “suffer” from a very strict default policy (and so be forced to call Helpdesk).
When selecting “New password policy” or “Edit selected password policy” you get a very intuitive dialog (see Figure 3) – much better than the ADSIEdit wizard I showed you in my previous articles on the subject.
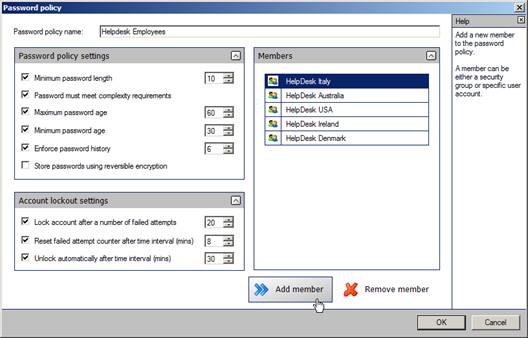
Figure 3: The password policy dialog
This is where we set the password policy settings, including account lockout settings. We can easily add and/or remove members (users or security groups) from this particular dialog too. This is a very nice way of displaying the password policy settings – quick and easy with almost no room for mistakes or annoying typos. Using an interface like this will definitely save you time and effort compared to the ‘nerdy’ ADSIEdit utility – you actually don’t even have to think, just follow the design and implement the agreed password settings!
Who is getting what?
One of the things that are particularly hard with Windows Server 2008 password policies is determining what user gets what policy settings – and the other way around. Specops thought about this and included the two neat options: “Lookup password policy for user” (Figure 4) and “Lookup users affected by selected policy” (Figure 5).
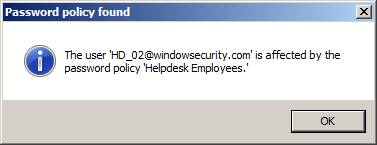
Figure 4: Quick lookup by user
It’s very easy for me to perform a query to see what password policy a particular user is “hit” by. In the opposite case, where I want to see what user are affected by a particular password policy I just choose the “Lookup users affected by selected policy” option – my result is shown below.

Figure 5: Quick lookup by policy
We have now seen the GUI functionality of Specops Password Policy Basic – all pretty cool compared to the built-in tools (or lack of the same). However, the Specops tool includes more goodies – all for free!
PowerShell CmdLets
Specops Password Basic contains a small bunch of PowerShell CmdLets. Table 1 is a quick introduction to the included free CmdLets:
Table 1: PowerShell quick reference
|
What is the CmdLet name? |
What does the CmdLets do? |
|
Get-BasicAffectedUsersForPasswordPolicy |
Used to find all users affected by a fine-grained password policy |
|
Get-BasicAffectingPasswordPolicy |
Used to find the fine-grained password policy that affect a specific user |
|
Get-BasicDomainPasswordPolicy |
Retrieves the single non-fine-grained password policy set by Group Policy |
|
Get-BasicPasswordPolicy |
Finds one or more fine-grained password polices |
|
New-BasicPasswordPolicy |
Creates a new fine-grained password policy in the domain |
|
Remove-BasicPasswordPolicy |
Removes a fine-grained password policy from the domain |
Table 1
Before using the PowerShell goodies the following command must be executed (within the PowerShell shell):
Add-PSSnapin SpecopsSoft.PasswordPolicyBasic
To get a list of the CmdLets type the following command: Get-Command -Noun Basic*
More PowerShell samples are available here.

Figure 6: PowerShell
PowerShell is great for performing the same tasks over and over again, documenting what you did and how you did it, etc. But, if neither the provided GUI nor the PowerShell CmdLets is good enough for you, Specops actually included an additional goodie too: an Application Programming Interface (API). Both the Specops administration tool and CmdLets utilizes this API and it can be used by third party developers to automate or integrate the administrative tasks of Specops Password Policy Basic.
One idea could be to create a script, or an application, to catch all users that are not “hit” by any password policy except from the Default Domain account policy – this will be good for security, especially if the default policy is not the most secure in the environment (as I normally recommend it to be).
Additional options
As previously mentioned, Specops Password Policy Basic is not the only (free) way to go beyond the built-in tools. Others have come up with additional solutions and I’m just going to mention a two of them very shortly. They both have the same basic functionality: create, edit, delete and link fine-grained password policies in the domain.
The first free tool is from Christoffer Andersson (TrueSec), a Microsoft MVP in Directory Services. The tool can be downloaded here in a beta version and provides basic functionality as shown in Figure 7.
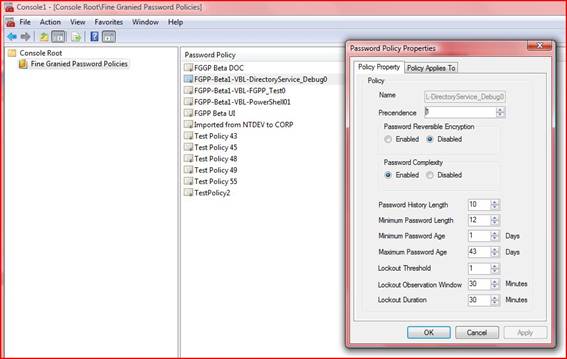
Figure 7: Christoffer Andersson’s MMC
The second free tool is from Dmitry Sotnikov and is built using PowerGUI – on top of some other free AD CmdLets from Quest – it can be downloaded here. Figure 8 shows the nice GUI.
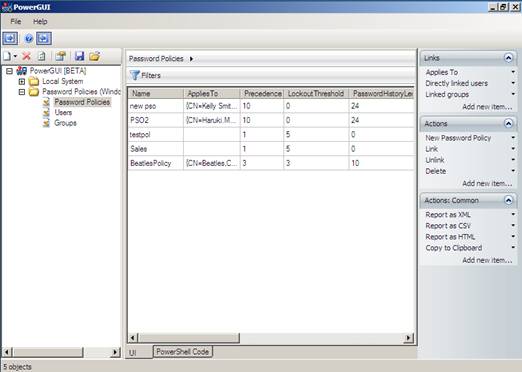
Figure 8: PowerGUI tool for handling Fine-Grained password policies
So, basically it’s up to you what you like – I’m sure we will see more feature complete versions of the utilities as we get closer to the release date of Microsoft Windows Server 2008: February 27, 2008!
Conclusion
Understanding how Granular Password Settings work – and how, when and why to use them – is very important. Hopefully the previous two articles about ‘Configuring Granular Password Setting in Windows Server 2008’ have enlightened you on the subject. The ‘password policy design’ itself is probably the hardest and most crucial part of setting up multiple password policies within a single Active Directory domain – but the implementation process, using ADSIEdit, may not be the best “out of the box” management solution from Microsoft – so Specops comes to the rescue with the free product: Password Policy Basic. I think the tool gives us everything we need to manage multiple password policies within the Windows Server 2008 domain – Thumbs up!
External links



