If you missed the other parts in this article series please read:
- Deploying IPsec Server and Domain Isolation using Windows Server 2008 Group Policy (Part 1)
- Deploying IPsec Server and Domain Isolation using Windows Server 2008 Group Policy (Part 2)
- Deploying IPsec Server and Domain Isolation using Windows Server 2008 Group Policy (Part 3)
In part 3 of our four part series on configuring NAP with IPsec policy enforcement, we configured a NAP IPsec policy and then configured the clients for testing. In this final installment of the series, we’ll test the clients and see how the security certificates are assigned and removed automatically and how clients are connected and disconnected from the network.
We’ll focus on two primary tasks in this article:
- Test the Health Certificate and Auto-remediation configuration
- Verify NAP Policy enforcement on VISTASP1
Test the Health Certificate and Auto-remediation Configuration
In this section we will perform the following tasks:
- Confirm that both VISTASP1 and VISTASP1-2 have Health Certificates
- Join VISTASP1-2 to the Domain
- Verify Auto-remediation on VISTASP1
Confirm that both VISTASP1 and VISTASP1-2 have Health Certificates
Use the following procedure to verify health certificate enrollment of VISTASP1 in a domain-authenticated environment and VISTASP1-2 in a workgroup environment.
Perform the following steps on both VISTASP1 and VISTASP1-2:
-
Open the Run dialog box and enter mmc, then press ENTER.
-
On the File menu, click Add/Remove Snap-in.
-
Click Certificates, click Add, select Computer account, and then click Next.
-
Verify that Local computer: (the computer this console is running on) is selected, click Finish, and then click OK.
-
In the left pane of the console, double-click Certificates (Local Computer), double-click Personal, and then click Certificates.
-
In the details pane, under Issued By, verify the subordinate CA, msfirewall-WIN2008SRV1-CA, is displayed. Verify that Intended Purposes shows System Health Authentication. Because VISTASP1-2 has not yet authenticated to the msfirewall.org domain, the client name is not displayed under Issued To, and the certificate purpose of Client Authentication does not appear. Verify that the certificate on VISTASP1-2 has Intended Purposes of System Health Authentication. This is a valid NAP health certificate for client computers in a workgroup environment. A domain-authenticated health certificate similar to the certificate obtained on VISTASP1.
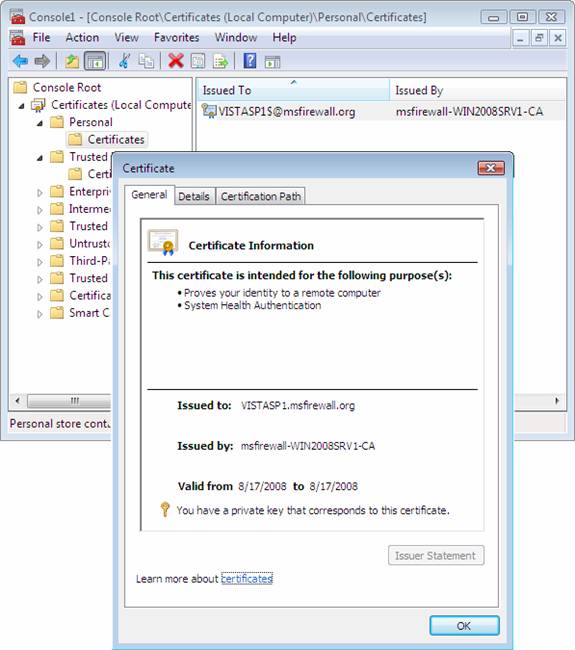
Figure 1
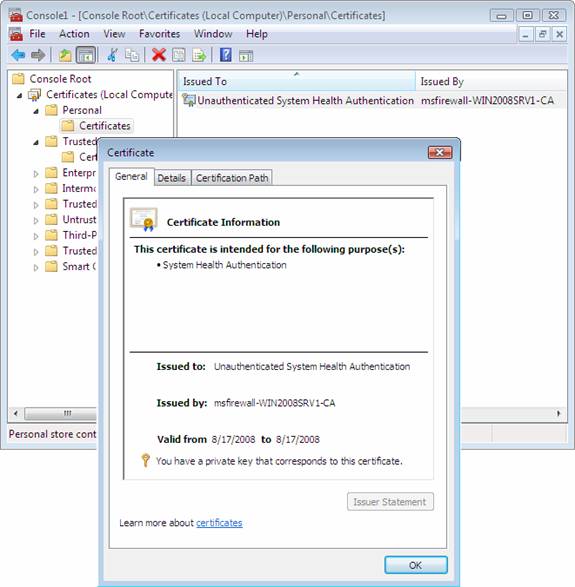
Figure 2
-
Close the Certificates console.
Join VISTASP1-2 to the Domain
Use the same procedure you used earlier to join VISTASP1 to the msfirewall.org domain to join VISTASP1-2 to the msfirewall.org domain. Log on as the domain administrator after the machine restarts.
Verify of Auto-remediation on VISTASP1
The NAP IPsec with HRA Noncompliant network policy specifies that noncompliant computers should be automatically remediated. The following procedure will verify that VISTASP1 is automatically remediated when Windows Firewall is turned off.
-
On VISTASP1, open the Run dialog box, and enter firewall.cpl, then press ENTER.
-
In Windows Firewall control panel, click Change settings, click Off (not recommended), and then click OK.
-
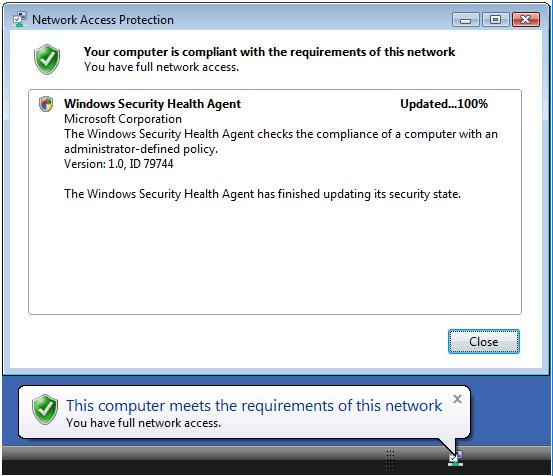
You might see a message in the notification area that indicates the computer does not meet health requirements. This message is displayed because Windows Firewall has been turned off. Click this message for more detailed information about the health status of VISTASP1. See the following example.
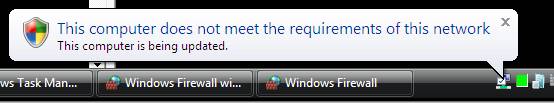
Figure 3
-
The NAP client will automatically turn Windows Firewall on to become compliant with network health requirements. The following message will appear in the notification area: This computer meets the requirements of this network.
Figure 4
-
Because auto-remediation occurs rapidly, you might not see these messages. To renew the NAP notification icon, type napstat at the command prompt, and then press ENTER.
Verify NAP policy enforcement on VISTASP1
Now let’s see how we can verify that NAP policy enforcement is being applied on the client systems. We’ll begin by testing with VISTASP1. To test this, we’ll perform the following procedures:
-
Configure the Windows SHV to be more restrictive by requiring that machines have anti-virus applications installed. Since we don’t have any AV software installed on any of the clients, the clients won’t be able to meet the requirements set forth in the SHV.
-
Refresh the SoH on VISTAP1. This will cause the client to send a new Statement of Health to the Health Registration Authority and will report that the client is fall out of compliance
-
Confirm that the client health certificate is removed. The Health Certificate is removed because the client has fallen out of compliance.
-
Restore health policy to a less restrictive state so that the client can be compliant. We will remove the AV requirement so that the client can become compliant again.
-
Refresh the SoH on VISTASP1 show that the machine is now compliant with the new policy.
-
Confirm that the client health certificate is restored.
Configure WSHV to require an antivirus application
First, configure NAP policy to require an antivirus application, causing CLIENT1 to be noncompliant.
Perform the following steps on WIN2008SRV1:
-
On WIN2008SRV1, click Start, click Run, type nps.msc, and then press ENTER.
-
In the left pane of the console, open Network Access Protection, and then click System Health Validators.
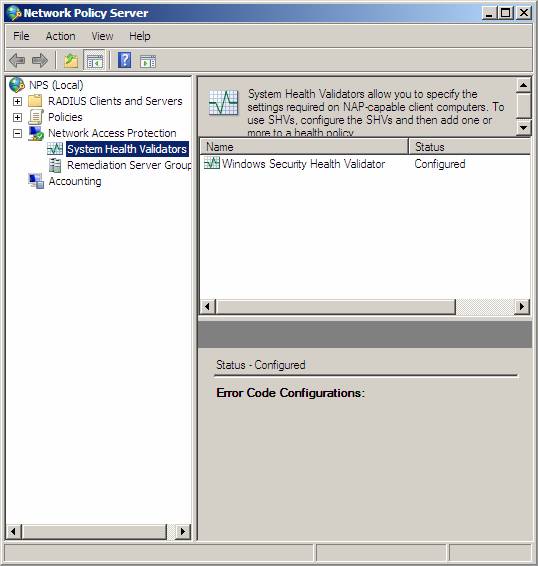
Figure 5
-
In the details pane, double-click Windows Security Health Validator, and then click Configure.
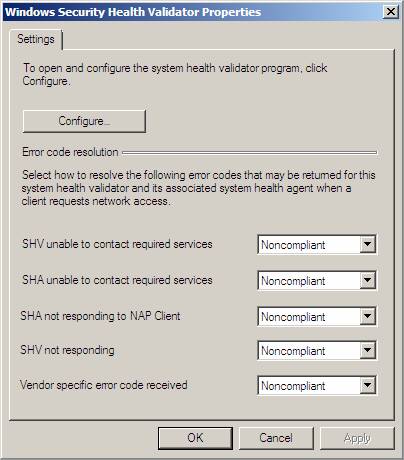
Figure 6
-
In the Windows Security Health Validator dialog box, under Virus Protection, select the check box next to An antivirus application is on.
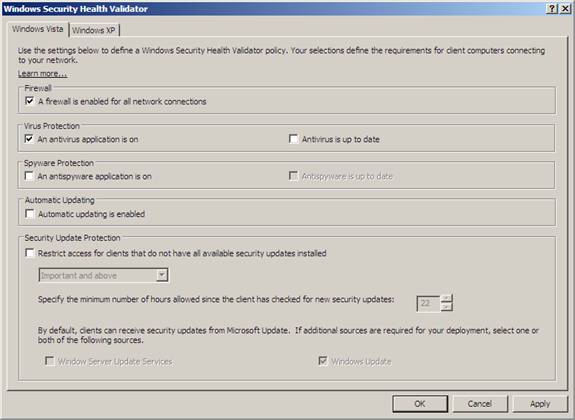
Figure 7
-
Click OK, and then click OK again to close the Windows Security Health Validator Properties window.
-
Leave the NPS console open for the following procedures.
Refresh the SoH on VISTASP1
Because health policies were changed after VISTASP1 received a health certificate, we need to trigger the sending of a new State of Health from VISTASP1 that will be evaluated against the more restrictive health policies. This will occur when the health certificate on VISTASP1 expires, or when a change in client health status is detected. We can produce a change in health status by turning off the Windows Firewall.
Perform the following steps on VISTASP1:
-
On VISTASP1, click Start, and then click Control Panel.
-
Click Security, click Windows Firewall, and then click Change settings.
-
In the Windows Firewall Settings dialog box, click Off (not recommended), and then click OK.
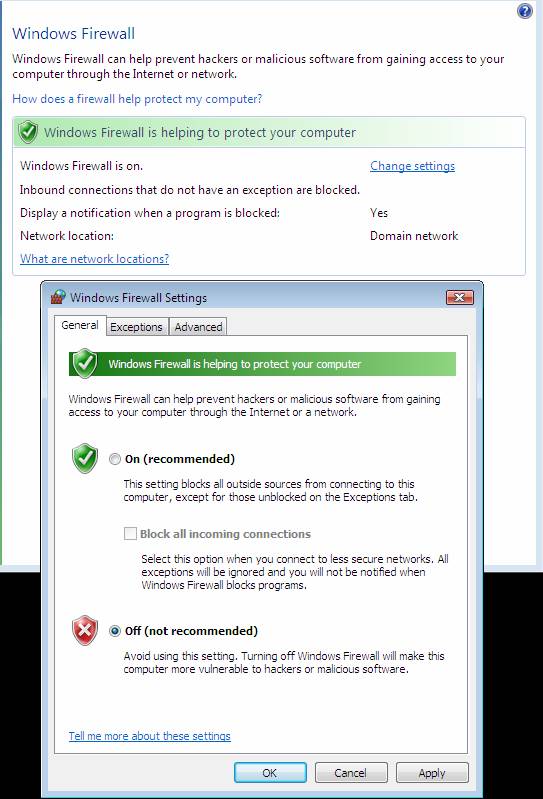
Figure 8
-
Windows Firewall is turned back on automatically because auto-remediation is enabled. However, because NAP policies now require an antivirus application, VISTASP1 will remain in a noncompliant state and will be unable to obtain a health certificate.
Confirm health certificate removal
Next, view computer certificates on CLIENT1 to verify that the health certificate has been removed.
-
On VISTASP1, open the Run dialog box and type mmc, and then press ENTER.
-
On the File menu, click Add/Remote Snap-in.
-
Click Certificates, click Add, select Computer account, and then click Next.
-
Verify that Local computer: (the computer this console is running on) is selected, click Finish, and then click OK.
-
In the console tree, open Certificates (Local Computer)\Personal.
-
Verify that no health certificate is present.
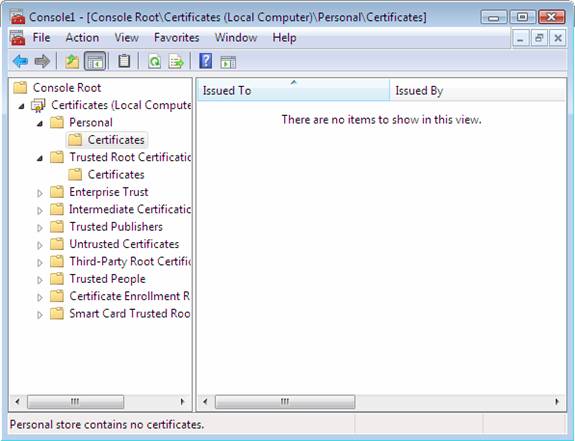
Figure 9
-
Leave the Certificates console open for the following procedures.
Remove the antivirus health requirement so that VISTASP1 can become compliant
Change NAP policies so that VISTASP1 can become compliant.
-
On WIN2008SRV1, in the left pane of the NPS console, open Network Access Protection, and then click System Health Validators.
-
Double-click Windows Security Health Validator, and then click Configure.
-
In the Windows Security Health Validator dialog box, under Virus Protection, clear the check box next to An antivirus application is on.
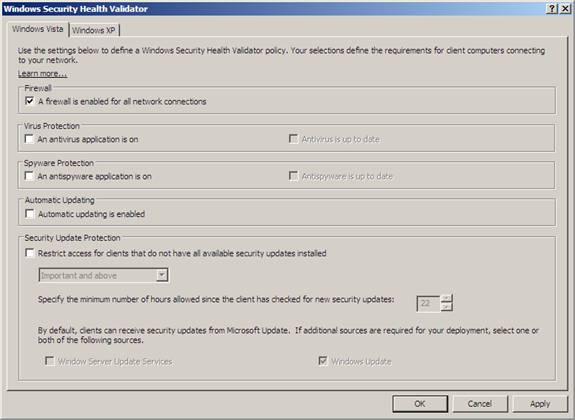
Figure 10
-
Click OK, and then click OK again to close the Windows Security Health Validator Properties window.
-
Close the NPS console.
Refresh the SoH on VISTASP1
Perform the preceding procedure to refresh the SoH on VISTASP1 by turning Windows Firewall off. A new SoH will be triggered, and Windows Firewall will be turned on. Because VISTASP1 is now compliant with NAP policies, it will be provisioned with a health certificate.
View computer certificates on VISTASP1 to verify that the health certificate has been restored.
-
On VISTASP1, in the Certificates console, in the console tree, click Personal.
-
Right-click inside the details pane, and then click Refresh. Verify that a health certificate is present.
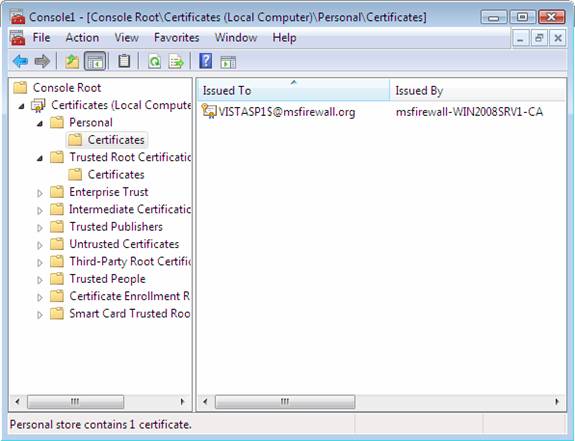
Figure 11
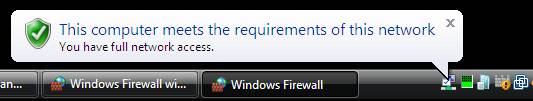
Figure 12
Summary
In this series on NAP IPsec enforcement I aimed at providing you a visual review of the many movement parts involved with a NAP IPsec enforcement solution. As you saw, there are many components to the solution and that each component must be configured correctly in order to reach a working solution. Many Windows admins have voiced concern over the complexity of NAP with IPsec policy enforcement and due to this concern, have not availed themselves of this exceptionally powerful and effective security technology. Make sure you replicate this demonstration in your own lab before deploying it on your production network, and also be sure to visit the NAP blog on a regular basis to get more information. Check out the NAP blog! Thanks! -Tom.
If you missed the other parts in this article series please read: