Microsoft provided a lot of policy settings for Windows 2000, and the list just grew longer with Windows XP/2003. Of course you could add more policies, for example, to configure Office.
IT professionals, wishing to implement a sophisticated system of group policies, soon found that proper and updated documentation was essential because a single wrong setting could bring much havoc unto an unsuspecting users’ workday.
This is especially true where multiple policies were implemented on the same user or computer. Even with documentation, finding out which setting came from which policy is not a simple task in complex scenarios where some settings might conflict.
At first, Microsoft trickled a few separate utilities, mostly command prompt based that you could use to, for example, make a printout of all policies or find out which policies were actually implemented for a single user on a specified computer.
Now, Microsoft has delivered GPMC as an add-on for Windows 2003 Server. It also works on Windows XP machines that have at least SP1 and the .NET framework installed.
The good news is that it can also be used to manage Windows 2000 based domain controllers (though not installed on one). The bad news is that there is some learning curve for using it.
The old way of managing Group Policies was maybe lacking in features but was easy to implement without special experience. You just right click an OU, Create the policy and set the settings. It was only when you had problems or conflicts where group policy became a nightmare.
Setting Group Policies
With GMPC when you right click an OU all you see is this:

You can also run GPMC from its shortcut, available under Administrative Tools.
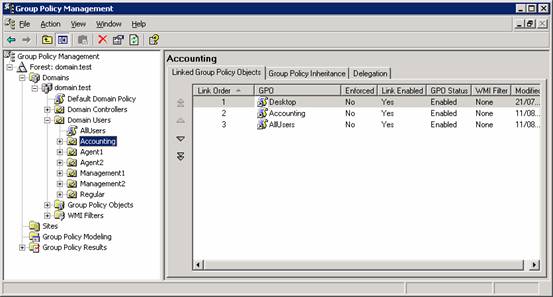
As one can see, GPMC looks a lot like an improved Active Directory Users and Computers interface. Since group policies can be applied to domain, OUs and sites, they all are represented. When you open an object, you can see which Group Policy policies are linked to it.
Does “linked” means applied? Usually, it does. But you can also disable a linked policy when necessary without needing to delete the policy or unlink it. This is useful for diagnosing problems.

You can also control the new Windows 2003 group policy features for filtering the policy by using groups or WMI filters so you could really control which policies are applied where.
The Settings tab shows the settings selected in the policy in a nice HTML look which you can save and open in a word processor or Internet Explorer.
It might be frustrating at first but unfortunately you cannot alter settings from here.

To change settings for a policy you right click it and choose “Edit”. You will then get the familiar group policy editor.
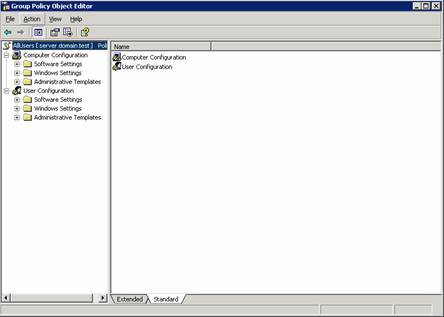
You can also see a list of Group Policy Objects and WMI filters at the bottom of each domain which you can backup, import, restore and save to a report.
Group Policy Modeling
Modeling allows you to plan Group Policies before you implement them by simulating changes. Each simulation checks what a user gets on a specified computer.
To create such a simulation you run the Group Policy Modeling Wizard by right clicking “Group Policy modeling”.


As can be seen, you can provide as much information as you like and skip to the end by clicking “Skip to the final page”.

Each of the next screen shots shows a way that the user is changed so that new policies might be applied.
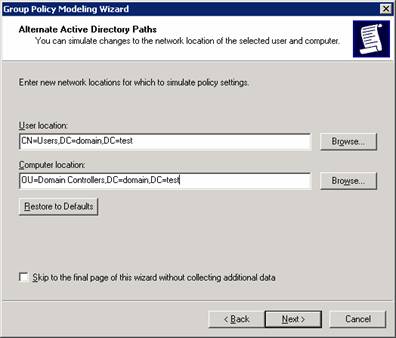

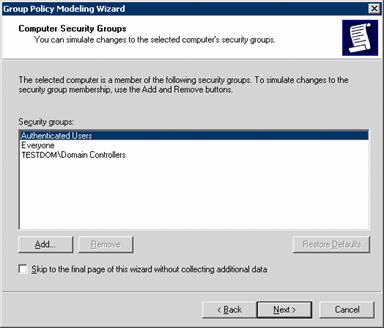


Once the Wizard finishes you can view which settings could apply to the user based on the information entered.
Group Policy Results
The Group Results Wizard is like a stripped down version of the Modeling Wizard with less dialog boxes. It allows you to connect to a remote computer and calculate the group policy that is actually applied to a user which logins to that computer.
Know that this wizard can fail if you don’t have administrative permissions on the target computer, or if there’s no RPC connectivity to that machine which can be caused by an installation of a personal Firewall such as the on Windows XP SP2 installed.
Conclusion
GPMC is more than an interface, it’s a new way of looking at group policies, but after some practice and study of this interfaces it’s an invaluable tool for designing and troubleshooting group policies.



