If you would like to read the first part in this article series please go to Optimizing Performance on the Forefront Threat Management Gateway (Part 2).
Introduction
The Forefront Threat Management Gateway (TMG) 2010 firewall is an integrated edge security gateway that provides advanced network and application layer protection services. It performs low-level protocol inspection, deep application layer traffic inspection, authenticates users, provides reputation-based access control, and inspects HTTPS communication. These advanced features consume a lot of resources that can potentially impede throughput and introduce delay if the system is configured incorrectly or sized improperly. In this article we’ll discuss some common issues that can lead to poor performance and talk about ways to improve and optimize the solution.
Hardware Configuration
Before we begin any discussion about the TMG firewall and performance, it is important that the underlying hardware is up to the task of supporting TMG in the role in which it will be deployed. It is recommended that high-quality server-class hardware or a dedicated security appliance be used. For best results it is essential that this hardware be sized correctly for its environment and expected load. TMG’s advanced network and application layer inspection capabilities impose significant resource demands on the system, so having adequate processing power, memory, disk and network capacity is fundamentally important to the overall stability and performance of the solution.
Determining how much hardware capacity is required for a particular implementation is a challenge, because each deployment is unique and has many dependent factors. To assist in determining hardware requirements, Microsoft has made available the Forefront TMG Capacity Planning Tool. This tool allows you to input specific details about your environment and it will offer advice on hardware specifications based on the expected number of users and bandwidth you have as well as protection features that will be enabled. Plan to be generous with CPU and memory resources to ensure the best performance, accommodate unforeseen spikes in usage, and to allow room for future growth.
Infrastructure Services
The TMG firewall relies heavily on supporting infrastructure services to perform many of its tasks. The overall performance of the solution is dependent upon how well services such as Active Directory and DNS are performing. If there are issues with AD or DNS, no amount of tuning on the TMG firewall is going to overcome them. There are many things that can go wrong with AD or DNS. Providing a comprehensive list of those would be outside the scope of this article, but here are some common issues that consistently result in poor TMG performance:
Network connectivity – Performance will be negatively impacted if the TMG firewall does not have reliable network connectivity to AD or DNS. TMG should be well-connected to these services; ideally they will be located in the same physical location and have gigabit connectivity. Be sure that any intermediary devices (routers, switches, etc.) are performing well and do not show signs of errors.
Active Directory site configuration – On several occasions I have noticed that poorly performing TMG firewalls were authenticating against domain controllers located in different geographic locations (on one occasion in another continent!) when there were domain controllers located in the same data center as TMG. This is caused by improperly configured Active Directory sites. Make certain that Active Directory IP subnets are properly defined and that an Active Directory site is configured that includes domain controllers which are local to the TMG firewall.
Networking
At the lowest levels, the TMG firewall is a routing firewall that delivers packets from one interface to another if policy allows it. It stands to reason that networking configuration plays an important role in overall system performance. Here are several key configuration settings and recommendations to optimize network throughput and performance:
Port speed and duplex – A port speed or duplex settings mismatch will result in extremely poor network performance. For proper operation, these settings must be identical at each connection. That means if you elect to manually configure the settings on the network interface of the TMG firewall, you must also make those identical settings on the switch to which it is connected. If the switch it is connected to is an unmanaged switch, you must leave the TMG firewall’s network interface set to auto-negotiate. You cannot configure one side manually and leave the other side set to auto-negotiate. Never under any circumstances should you use a hub in a production environment! Hubs are relics from the 80’s when NetBEUI was still prevalent. Even an unmanaged switch will be far better than a hub.
DNS Configuration/Network Interface Binding Order – This is one of the most common configuration errors and can result in unreliable authentication and poor name resolution performance. In all but the rarest cases, DNS servers should be configured on the Internal network interface only. In addition, it is essential that the Internal network interface on multi-homed firewalls be configured first in the ordered list of network interfaces. For more information see my article DNS Configuration Review.
Isolated Network Segments – It is an excellent idea to have the TMG firewall’s network interfaces located in isolated network segments whenever possible. Doing this improves both security and performance. It reduces the risk of layer two attacks (e.g. ARP cache poisoning) and makes network discoverability more difficult. If Network Load Balancing (NLB) is enabled this becomes even more important. By default, NLB broadcasts heartbeat information which will be seen by all hosts on the segment. Having the TMG firewalls configured in an isolated segment limits those broadcasts to only the hosts that require it.
Back Firewall Configuration – Although the TMG firewall is edge-ready and edge-capable, this is not always an optimal configuration in terms of security and performance. Hosts that are exposed directly to the Internet are constantly barraged with probes and scans of all types. Configuring the TMG firewall as a back firewall to another firewall can reduce the amount of noise it has to process. For example, having a Cisco ASA at the network edge configured to allow only the protocols that TMG will process frees up valuable resources for it to perform advanced application layer traffic inspection and authentication. It has the added benefit of reducing log pollution, making the logged data much more meaningful and easier to identify anomalous traffic.
Web Proxy Clients – Configuring clients as Web Proxy clients has significant performance benefits, although many administrators prefer SecureNAT client configuration because it requires no changes to client software. SecureNAT clients consume substantially more resources on the TMG firewall than Web Proxy clients because the Web Proxy client establishes far fewer TCP connections to the TMG firewall’s web proxy listener in order to retrieve web content. For example, when connecting to a popular web site (in this example espn.com) the SecureNAT client established 31 TCP connections to display the main web page.
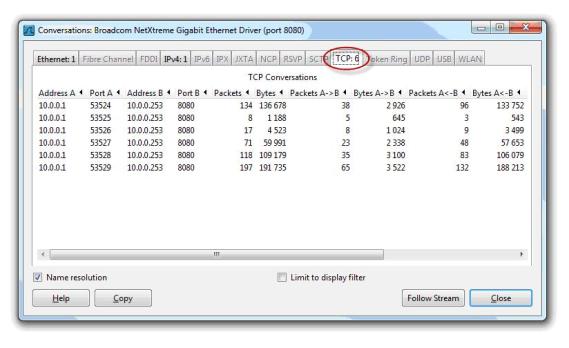
By contrast, when configured as a Web Proxy client only 6 TCP connections were required to display the same web page.
If you have thousands or tens of thousands of users, this exponential increase in TCP connections and commensurate increase connection rate can easily consume twice as much CPU than Web Proxy clients.
Summary
There are myriad factors that affect the overall stability and performance of the TMG firewall. In this article we’ve focused on the importance of having healthy infrastructure services such as Active Directory and DNS. We established that the TMG firewall should be well-connected to these services, and that proper Active Directory IP subnet and site configuration is essential. We looked closely at networking configuration and talked about configuration best practices to improve network throughput. Properly configured network settings such as port speed and duplex, DNS server configuration, and network interface binding order are vital for optimum network throughput. Firewall placement and client configuration also have dramatic effects on overall system resource utilization and performance. In my next article we’ll discuss some additional ways in which to optimize performance on the TMG firewall.
If you would like to read the first part in this article series please go to Optimizing Performance on the Forefront Threat Management Gateway (Part 2).