Most of what cybersecurity researchers deal with, at least in terms of vulnerabilities, involve identifying flaws that can be exploited and crafting patches for these flaws. There are instances, however, where core designs of devices are discovered to allow for hacking by criminals. In such situations, a simple patch cannot always be created in the same manner that other vulnerabilities are dealt with.
Such a case is affecting Android mobile devices according to a paper presented by researchers from the Georgia Institute of Technology and the University of California, Santa Barbara for the IEEE Security and Privacy Symposium in San Jose, CA. Entitled Cloak and Dagger: From Two Permissions to Complete Control of the UI Feedback Loop, the paper details how System Alert Window and Bind Accessibility Service, when employed together, can create a scenario that allows clickjacking.
The first step of the attack involves a potential victim installing an application that utilizes Android’s overlay feature. Since Android does not ask for user permission when installing an app that uses the System Alert Window (such as Facebook and Twitter) from the Play Store, a malicious app coder can include the overlays without knowledge of the user. The overlays are, in this case, used to trick the user into enabling the Bind Accessibility Service.
As the paper states:
“The (overlay) allows an app to draw overlays on top of other apps, while the (accessibility feature) grants an app the ability to discover UI widgets displayed on the screen, query the content of these widgets, and interact with them programmatically.”
The reason why all of this is dangerous is that an attacker can create a situation in which a user can be prompted to enter sensitive data that will then be stolen. All of this will occur without user knowledge because the System Alert Window allows hackers to alter what the app shows in GUI form (like widgets, photos, or videos), and when employed with the Bind Accessibility Service, can generate false inputs for users to enter sensitive data or accidentally install malicious apps.
This video shows just what happens if a variation of this attack is occurring:
[tg_youtube video_id=”RYQ1i03OVpI”]
What occurs is a user being coaxed by their supposedly safe application into doing whatever a hacker wishes as they are totally oblivious to the changes being made. On their own, the System Alert Window attack would not know instantaneously how a user is reacting to the altered visuals and would likely allow a user to see something is off.
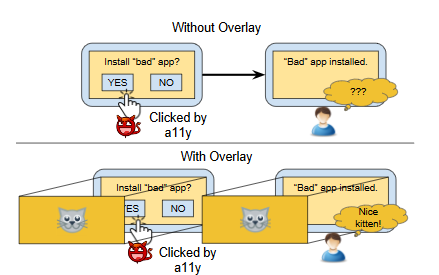
If the Bind Accessibility Service is employed on its own, the fake inputs would be generated, but a user would also see how these inputs are reacting in real time (showing quickly that the app is hacked).
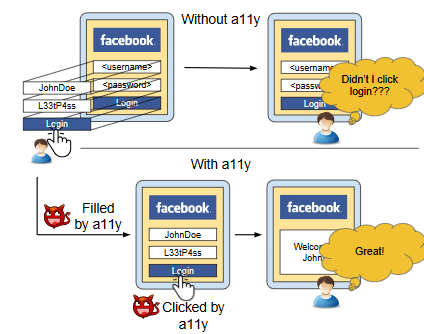
As the researchers state in their abstract, when put together the System Alert Window and Bind Accessibility Service allow hackers to “completely control the UI feedback loop and create devastating attacks… ranging from stealing user’s login credentials and security PIN, to the silent installation of a God-mode app with all permissions enabled.”
Google was convinced that this scenario was not possible, but now that they have been definitively been shown that this is not the case. According to Threatpost, Google is planning to modify how Android “handles overlays” in their “upcoming release of Android O, expected later this year.”
Photo credit: Pixabay



