One of the keys to keeping your Microsoft 365 environment safe is understanding the factors that pose a significant security risk. After all, it is difficult to mitigate risks if you don’t even know what those risks are. Fortunately, there are a series of reports built into Azure Active Directory that you can use to assess your organization’s risks as they relate to user accounts and attempted logins. In this article, I will discuss these three reports and show you some actions to take if you identify risks within your organization.
Azure Active Directory risks reports
Risky sign-ins
The first of these reports is the Risky Sign-ins report. You can access this report by opening the Azure Active Directory admin center, going to the list of all services, and then locating the Security section. From there, just click on the Azure AD Risky Sign-Ins report, which you can see in the image below. Incidentally, all of the reports that I am going to be discussing are located in the Security section.
You can see the Risky Sign-ins page in the following image. In this case, the list of risky sign-ins is empty because there have not been any risky sign-ins. Even so, you can at least get a feel for what the console looks like and what options are available.
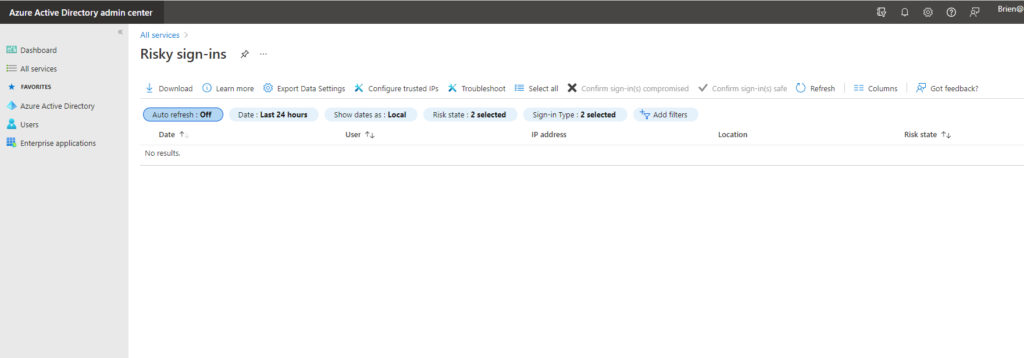
There are any number of things that can cause a login to be deemed to be risky. For example, Microsoft might decide that a login is risky if the user’s credentials have been leaked or if the user is logging in from an unfamiliar location, especially if it would have been impossible for the user to travel to that location in the time that has passed since their last normal login.
So if risky logins are found to be occurring within your organization, what can you do about it? Your options vary depending on what type of subscription you have. The Risky Sign-in console allows you to review the risky sign-ins and flag each one as either safe or compromised, based on the results of your investigation and the information provided by the console.
However, if you have an Azure AD Premium P2 subscription, you can create a sign-in risk policy that allows you to block risky sign-ins or require multifactor authentication. To do so, go to All Services and then click on Azure AD Identity Protection, followed by Sign-in Risk Policy. As you can see in the next screenshot, a sign-in risk policy can be applied to all users or a specific group of users (such as those with elevated permissions). Azure AD allows you to specify the risk level at which you want to take action and choose what happens when that level is reached. For example, you might choose to block a user’s sign-in if a high level of risk is found.

Risky users
The second report is the Azure AD Risky Users report. This report, which you can see in the next screenshot, displays a list of user accounts that are considered to pose a risk. I have blocked out the user name in the screenshot for obvious reasons, but as you can see, the console also lists the user’s risk state and the date and time when the user’s risk was most recently evaluated.

When a user account is identified as risky, it usually means that the user’s credentials may have been compromised. The console allows you to confirm that the account has been compromised, dismiss the risk, force a password reset, or block the user.
If you have an Azure AD Premium P2 subscription, you can also create a User Risk Policy. Just go to the list of Azure AD services and click on Identity Protection, followed by User Risk Policy. As you can see in the next screenshot, creating a user risk policy works the same way as creating a sign-in risk policy. You must simply specify which groups of users the policy applies to (or you can apply the policy to all users), choose a risk level, and then choose the action that will be performed once that risk level has been reached.

Risk detections
The third report that is available is the Risk Detections report. You can access this report by going to the list of Azure AD services and clicking on Azure AD Risk Detections. The Risk Detections report is a lot like the other two reports but provides a bit more detailed information about risks that have been detected. For example, this report provides you with information about the user’s location when they attempted to log in. It can also show you other risks that may have been triggered at the same time. This particular report is informational in nature, and you will need to go to either the User Risk report or to the Sign-in Risk report to take action.
Better yet, keep your Azure Active Directory free from risks
As helpful as the various Azure Active Directory risks reports and the corresponding risk policies may be, it is important to keep in mind that these policies and reports are reactive in nature. In other words, a risk has to exist before it can be identified. While identifying risks is undeniably important, it is equally important to keep those risks from happening in the first place.
One of the most effective things that you can do to help mitigate user and sign-in risks within Microsoft 365 is to enable multifactor authentication. That one feature goes a long way toward protecting your user accounts. It’s also worth taking the time to examine your organization’s Microsoft 365 secure score. The secure score is a numerical score that represents your organization’s Microsoft 365 security health. Not only does this score help you to gauge your security, but Microsoft also includes a list of things that you can do to improve both your score and your organization’s security.
Featured image: Shutterstock



