While this quick hint can be used with any web service, I will concentrate on cloud — and more specifically — Azure. When troubleshooting Azure Web Apps, Application Gateways, it is essential to understand which certificate is currently in use, especially when testing rotation and renewing certs.
For macOS users, we can use either Microsoft Edge or nmap utility. In this blog post, we will cover the process of using nmap through the command line in your favorite coffee shop (assuming you are a fan of that coffee company based in Seattle). If so, you are probably using macOS — and this blog is for you or anyone that wants to use nmap utility.
The first step is to install HomeBrew, an installer that helps install tools in a macOS or Linux system (actually, the system has built-in tools to do that). The process to install is simple. Just run the following line of code on your terminal:
ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)" 2> /dev/null
Having HomeBrew installed on your macOS makes the installation process for additional tools quite easy. Here is the command to perform nmap installation:
brew install nmap
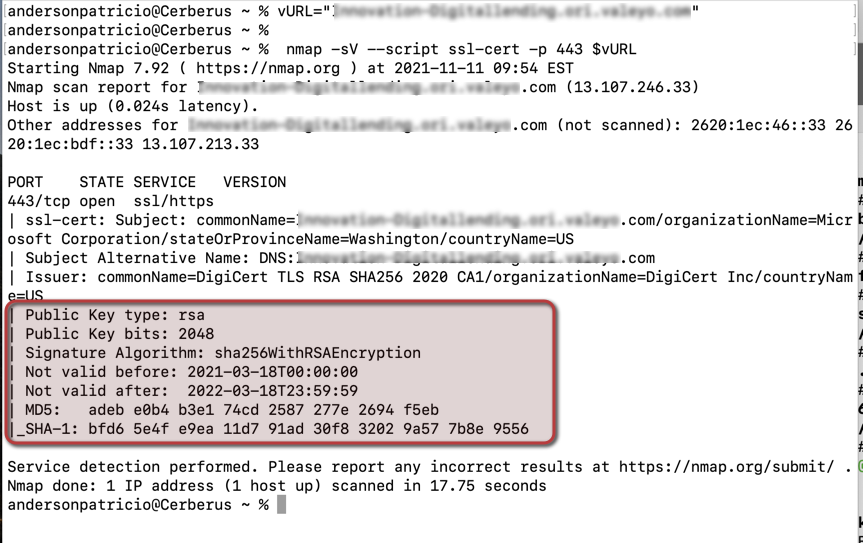
Now that we have all the pieces installed, we need to run these two (2) commands to query the URL and see which certificate is being used. The first line needs to be updated with the domain/URL that you want to check.
vURL=”app.domain.ca” nmap -sV --script ssl-cert -p 443 $vURL
As part of the output of the nmap utility, we can check the key size and the validity of the certificate, which is crucial when testing certificate rotation.