Microsoft announced back in 2021 that they would be turning off basic authentication for all Exchange Online tenants in Microsoft 365. With COVID changing everything, the deadline was postponed. But Microsoft has now set a definite date, announcing that “effective October 1, 2022, we will begin to permanently disable Basic Auth in all tenants, regardless of usage, with the exception of SMTP Auth.” What does this mean for you? For those new to Microsoft 365, basic authentication allows users to connect to a mailbox using only a username and a password. The reason behind stopping this is that it will prevent accounts from being brute-forced or falling victim to password spray attacks. The policy does not affect Exchange Server on-premises.
Every day Basic Auth remains enabled in your tenant, your data is at risk, and so your role is to get your clients and apps off Basic Auth, move them to stronger and better options, and then secure your tenant, before we do.
–Microsoft Exchange team
Modern authentication will supplant basic authentication
Modern authentication is what you and your organization need to be using going forward. If you are running Exchange 2016 and higher and you have hybrid running, you can enable modern authentication in Exchange and Microsoft 365, but this discussion is out of scope for this article. To turn off basic authentication, your clients need to support the new authentication method. On docs.microsoft.com, they provide a list of clients that are supported, and you should check it from time to time to ensure that you meet the requirements. Here is the link to the article.
The clients they have listed are as follows:
- Outlook 2016 for Mac or higher
- Outlook 2013 and higher
- Outlook on iOS and Android
- Mail app for iOS 11.3.1 or higher
If you head over to the admin portal, you should notice the announcements regarding basic authentication. You may find that Microsoft has disabled it already on your tenant, or they will turn off basic authentication. If you are not prepared, you may end up with a pretty busy day or week fixing the issues. Take note that basic authentication is being turned off for multiple protocols, which include:
- POP3
- IMAP4
- Remote PowerShell
- Exchange Web Services
- Office Address Book
- MAPI
- RPC
- ActiveSync
- SMTP Auth
You can reenable basic authentication — but only temporarily
As you can see, the list is long and if Microsoft did turn off basic authentication in your tenant, you can enable it again. But when the time comes next year that it hits end-of-life, it will be turned off permanently. Here is an example of the message in the admin center:

For those concerned about the security of Basic Auth, the question is, “How do I disable basic authentication?” You have a few options. Here are some of them:
- Authentication policies
- Enabling security defaults (this is automatically turned on for new Microsoft 365 tenants)
- Client access rules
With authentication policies, you can create a new policy with PowerShell and then apply the policy to all users that block the legacy authentication methods.
Enabling security defaults
Enabling security defaults can be done from Azure Active Directory. From the Microsoft 365 admin center, you can expand admin centers on the left and then click on Azure Active Directory, which will open a new page and ask you to sign in with an account that is a global admin. Once you have signed in, you will be greeted with the main Azure AD page. Click on Azure Active Directory shown below:
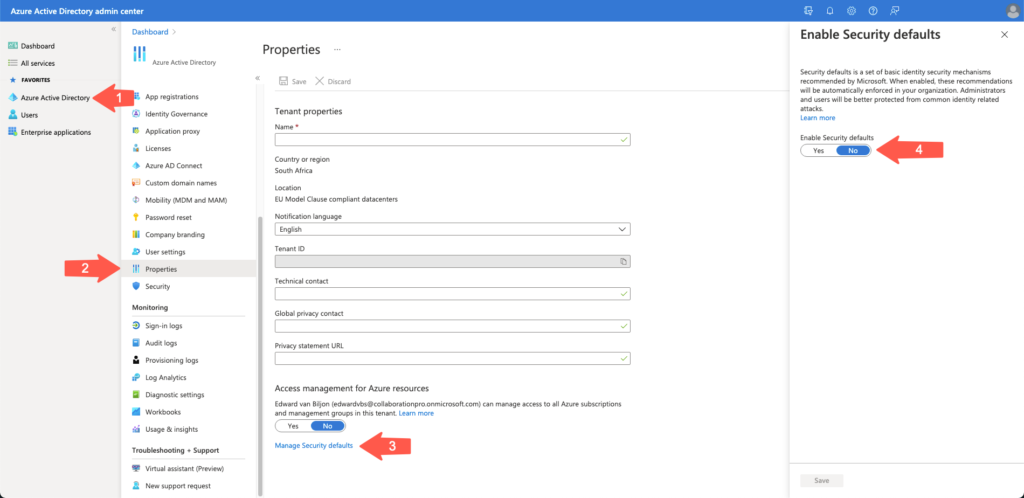
Once you have clicked on Azure Active Directory (Arrow 1), the middle section will change and present you with the list of options. Select Properties (Arrow 2) and at the bottom of the page where it says “Access management for Azure resources,” and click on Manage Security defaults (Arrow 3). This will bring up a menu on the right-hand side (Arrow 4). As you can see, my tenant is set to No. Once you select the Yes button, the Save button that is grayed out will enable, and you can click it.
This will kick off a task in Azure AD, and you can see in the notification section on the top that there is one listed. Now that I enabled it on my tenant and tried to sign into one of the admin centers, I was asked to set up Azure AD multifactor authentication and conditional access, which asked to send a text message to my phone.
Now that we have enabled security defaults, basic authentication is disabled. To read more about what security defaults are, you can refer to this Microsoft docs page.
If you head over to the admin center for Microsoft 365 and you click on Settings and then Org Settings and scroll down the list till you see Modern Authentication, you will see the message on the right-hand side if you have security defaults enabled:
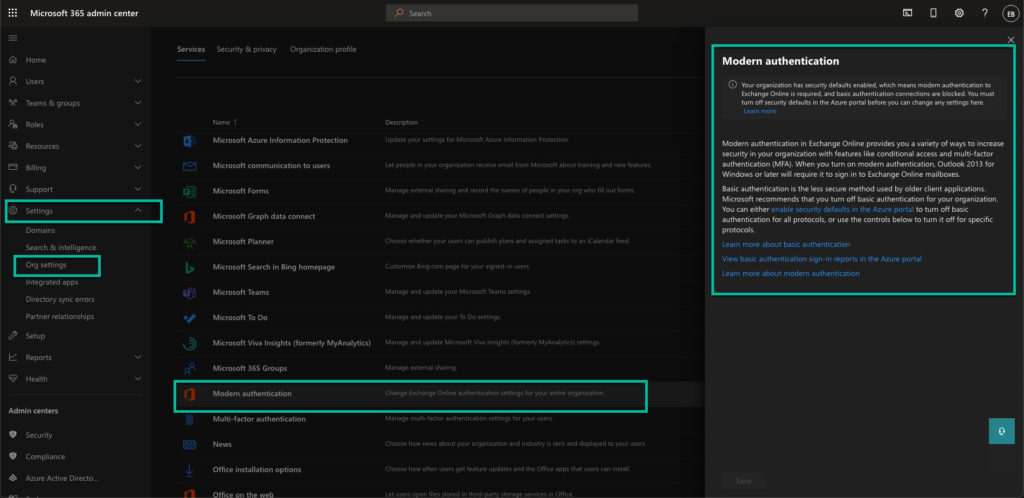
If you want to view the basic authentication sign-in via a report, click the next-to-last link in the right-hand block called View basic authentication sign-in reports in the Azure Portal. This will bring up a sign-in page again for Azure Active Directory, and you are able to view the reports. This will give you an indication of how many users or applications are still using basic authentication so that you can plan your switch.
If Microsoft has switched basic authentication off and it affects your organization, you can reenable it while you move to modern authentication. Do not leave the move to modern authentication for the last minute, because you might run out of time. But the main reason you should change to modern authentication sooner rather than later is that your data is at risk with basic authentication.
Featured image: Shutterstock



