Microsoft Security Intelligence is warning about a scam that is infecting victims with malware by using emails to get recipients to call a phony call center. It is a multipronged attack that has been dubbed “BazarCall” for the BazarLoader (sometimes known as BazaLoader) malware that gets distributed. Microsoft Security Intelligence brought it to the public’s attention through a series of tweets that detail the attack method.
We’re tracking an active BazaCall malware campaign leading to human-operated attacks and ransomware deployment. BazaCall campaigns use emails that lure recipients to call a number to cancel their supposed subscription to a certain service. pic.twitter.com/RS5wGSndhv
— Microsoft Security Intelligence (@MsftSecIntel) June 22, 2021
The basic attack goes as follows:
- Target receives email from scammers stating they need to call to cancel a subscription or cancel a payment made to their credit card, or something to that effect.
- Victim calls the scammers who then send a malicious attachment to be opened by the victim.
- Once the target enables macros on the document (usually an Excel file), they are infected with the BazarLoader.
- BazarLoader begins communicating with its command and control server and engaging in post-exploitation activity.
This particular news story was brought to this reporter’s attention because, in a strange twist of fate, TechGenix is one of the many businesses that has seen its name used in this phony call center scam. According to a reader who contacted us, of the many ways that these “call centers” get people’s attention, phony invoices are one of them. The below screenshot of the fake TechGenix invoice proves this.
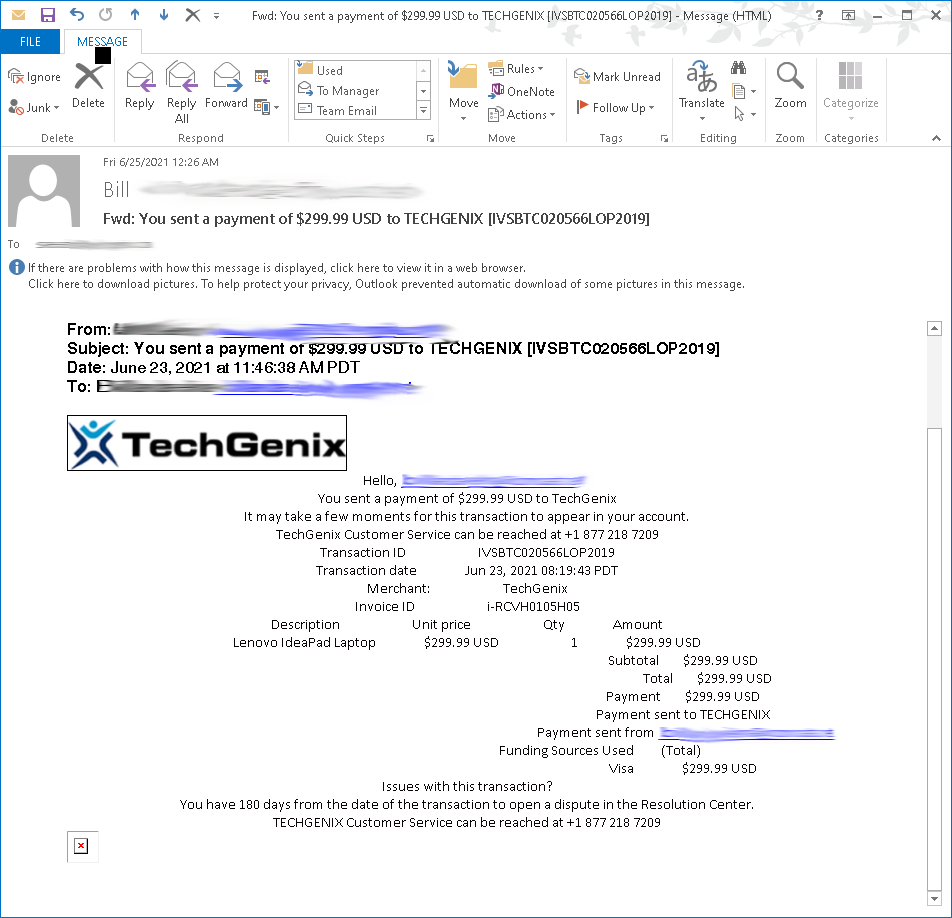
Palo Alto Networks’ Unit 42 released an in-depth research post about this particular campaign. In the analysis, it mentions how the BazarLoader malware functions in its infection and post-exploitation phase:
After macros are enabled on the downloaded Excel file, the BazarLoader DLL is dropped, and it generates a URL containing the string campo. This type of URL is called Campo Loader, which acts as a gateway that redirects traffic to malware.
BazarLoader provides backdoor access to an infected Windows host. In some cases, Cobalt Strike is seen as follow-up malware, leading to other malware like Anchor. At least two cases have been publicly documented where BazarLoader malware led to Cobalt Strike and then to Anchor malware. One case happened in February 2021, and the other case happened in March 2021.
However, BazarLoader is not limited to just Cobalt Strike and Anchor as follow-up malware. 2020 saw reports of BazarLoader leading to ransomware like Ryuk. Backdoor access to an infected Windows host could lead to any family of malware.
One of the problems with preventing this scam is that because there is no malware in the email, it often gets through antivirus and antispam filters. As it is with social engineering campaigns like this, always do research into who is contacting you. If someone is claiming you are subscribed to something you’ve never heard of, chances are it is a scam.
Featured image: Shutterstock



