Active Directory domain controllers must be patched to avoid any security risks. Patching domain controllers is also required for compliance and auditing purposes. Microsoft releases security patches and hot fixes every month. You might have patching software that pushes available patches and can be used for patching domain controllers throughout the Active Directory forest and also help in generating a report, but from time to time you might want to perform a quick recent update check on all domain controllers to ensure your patching software is doing its job efficiently. We have designed a PowerShell script that you can use to gather the last patching status from all domain controllers. The PowerShell script explained in this article uses Get-HotFix PowerShell cmdlet to collect the number of updates applied since last 30 days, last update date and time, and number of updates that have been applied.
Before you execute the below PowerShell script, please make sure to meet certain requirements such as running the script from a computer that has PowerShell modules installed and a domain account that has permissions to access domain controllers. Apart from installing the PowerShell modules on a computer, there are other requirements that you should meet as listed below:
- The script uses the currently logged on user account to access domain controllers. Please make sure the account that you use to run the script has admin access to the target domain controllers.
- Create a folder nameed “C:\Temp” on the computer from where you will run the script. The script will save the report file under C:\Temp folder.
- Get a domain controllers list by running DSQuery Server –O RDN > C:\Temp\DCList.TXT command to ensure domain controller names are collected and saved in C:\Temp\DCList.TXT file. The script checks C:\Temp\DCList.TXT file to connect to each domain controller and then get the patching data.
Once you have met the above requirements, run the below PowerShell script from an elevated PowerShell command prompt.
$TestCSVFile=”C:\Temp\DCPatchingStatus.CSV”
Remove-item $TestCSVFile -ErrorAction
$ThisStr=”Domain Controller,Connection,Command Status, Number of Updates Applied Since last 30 Days, Last Update Date,Final Status”
Add-Content “$TestCSVFile” $ThisStr
$GDCList = “C:\Temp\DCList.TXT”
$TotNo=0
$ItemCount=0
$TestText = “”
$TestStatus=””
$SumVal = “”
$AnyGap = “No”
$ErrorOrNot = “No”
$AnyOneOk = “No”
$TotDCsInError = 0
Foreach ($ItemName in Get-Content “$GDCList”)
{
$DCConError = “Ok”
$DCConStatus = “Ok”
$ProceedOrNot = “Yes”
$Error.Clear()
$AllServices = Get-WMIObject Win32_Service -computer $ItemName
IF ($Error.Count -ne 0)
{
$ProceedOrNot = “No”
$TotDCsInError++
$DCConError = $Error[0].Exception.Message
$FinalSTR = $ItemName+”,Not OK: Error: $DCConError”
Add-Content “$TestCSVFile” $FinalSTR
}
IF ($ProceedOrNot -eq “Yes”)
{
$ComConError=”Ok”
$Error.Clear()
$TotHotFixes = Get-HotFix -ComputerName $ItemName | Where-Object {$_.Installedon -gt ((Get-Date).Adddays(-30))}
$AnyOneOk=”Yes”
$TotHF = $TotHotFixes.Count
$FinalStatusNow = “OK”
IF ($TotHF -eq 0)
{
$IsHFOk = “No”
$AnyGap = “Yes”
$FinalStatusNow = “WARNING: Domain Controller has not been patched since last 30 days.”
}
$TotHotFixes = Get-HotFix -ComputerName $ItemName | ?{ $_.installedon } | sort @{e={[datetime]$_.InstalledOn}} | select -last 1
$LastNowAll = $TotHotFixes.InstalledOn.DateTime
IF ($AnyGap -eq “Yes”)
{
$TotNo++
}
$ThisSTr = $ItemName+”,”+$DCConError+”,”+$ComConError+”,”+$TotHF+”,”+'”‘+$LastNowAll+'”‘+”,”+$FinalStatusNow
Add-Content “$TestCSVFile” $ThisStr
}
else
{
$ComConError = $Error[0].Exception.Message
$FinalSTR = $ItemName+”,$DCConError,”+$ComConError
Add-Content “$TestCSVFile” $FinalSTR
}
}
$OthText = “”
IF ($TotDCsInError -ne 0)
{
$OthText = “Some Domain Controllers have not been checked due to connectivity or command issues.”
}
IF ($AnyGap -eq “Yes”)
{
$TestText = “Some domain controllers have not been patched since last 30 days. $OthText”
$SumVal = $TotNo
$TestStatus=”High”
}
IF ($AnyGap -eq “No”)
{
$TestText = “All Domain Controllers have been patching since last 30 days. Please load and check result to ensure Last Pathing Date is current. $OthText”
$SumVal = “”
$TestStatus=”Passed”
IF ($AnyOneOk -eq “No”)
{
$TestText = “Error Executing Dynamic Pack.”
$SumVal = “”
$TestStatus=”Completed with Errors.”
}
}
$STR = $ADTestName +”,”+$TestStartTime+”,”+$TestStatus+”,”+$SumVal +”,”+$TestText
Once you have finished executing the script, a report will be generated that will contain the domain controller name, command status, number of updates applied in the last 30 days, last update date and time, and a final status indicating the patching status of the domain controller. This is also shown in the screenshot below.
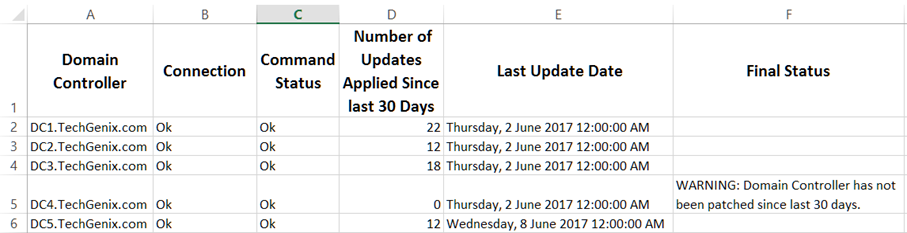
If you look at the report generated by the script, it is clearly visible that the DC4.TechGenix.com has not been patched in the last 30 days. The script checked the number of updates applied since 30 days and it didn’t find any updates installed on the DC4.TechGenix.com domain controller as it is indicated in the “Number Of Updates Applied Since Last 30 Days” column in the above report. Once you have the patching status of domain controllers, you can trigger updates for patching domain controllers that have not been patched.
Tip: The script provided in this article has not been designed specifically to check patching status of domain controllers. You might want to check patching status of application or member servers. In case you wish to check the patching status of any Windows computers, just modify the C:\Temp\DCList.txt and mention list of server names in the file.
This script is part of PowerShell-based Dynamic Packs that ship with the Active Directory Health Profiler, which you can use to perform a complete health check of an Active Directory forest. There are 99 health checks included in the AD Health Profiler.
By using the PowerShell script provided in this article, you can know the patching status of domain controllers. You can include this script in your daily Active Directory health procedure and have it run every month to ensure Active Directory domain controllers are being patched regularly to avoid any security risks.
Photo credit: Pixabay




Hi ,
I am getting error can you please help me.
Remove-Item : Missing an argument for parameter ‘ErrorAction’. Specify a parameter of type ‘System.Management.Automatio
n.ActionPreference’ and try again.
At C:\Temp\Check when Last Time Domain Controller patched.ps1:2 char:38
+ Remove-item $TestCSVFile -ErrorAction <<<<
+ CategoryInfo : InvalidArgument: (:) [Remove-Item], ParameterBindingException
+ FullyQualifiedErrorId : MissingArgument,Microsoft.PowerShell.Commands.RemoveItemCommand
Get-WmiObject : The RPC server is unavailable. (Exception from HRESULT: 0x800706BA)
At C:\Temp\Check when Last Time Domain Controller patched.ps1:21 char:29
+ $AllServices = Get-WMIObject <<<< Win32_Service -computer $ItemName
+ CategoryInfo : InvalidOperation: (:) [Get-WmiObject], COMException
+ FullyQualifiedErrorId : GetWMICOMException,Microsoft.PowerShell.Commands.GetWmiObjectCommand