After Citrix bought French software maker Norskale in September 2016, the product they acquired in the deal was transformed into Citrix Workspace Environment Management. This is an additional software product available for Citrix customers running XenDesktop or XenApp Enterprise or Platinum edition. You must have a Customer Success Services Select (formerly known as Software Maintenance) agreement to use the product. In an earlier article, I did a walk through of the installation of the product. Now it is time to show you the possibilities of the product by setting up the user environment, profile management, and the administrator possibilities.
Configuring user environment with Citrix WEM
With the last component installation and initial setup, we can start configuring the environment. All configuration is done out of the Management Console. If you did not have experience with the Norskale product, you need to become familiar with the way you configure the product, especially for the user environment component.
For the user environment manager part, this is the way to go:
- Define the UEM resources.
- Define configured users (groups or users to which a UEM resource should be assigned).
- Create conditions.
- Combine conditions in rules.
- All parts come together in assignment. Within assignment based on configured users, one or more UEM resources are assigned combined with the rules created.
To get you familiar with the way of working and possibilities, first let’s take a look at creating UEM resources. Within Citrix UEM, you can pre-configure the whole user environment in advance. With UEM resource you are really defining the part that would be done via (logon)scripts before Citrix WEM (or another user environment management product). Within Citrix WEM, you can define the following part:
- Applications: Within applications, you will set up application shortcuts (in Start Menu, Desktop, Taskbar, and so on).
- Printers: Mapping printers into the session.
- Network drives: Mapping of network shares. You would expect here that you can assign a drive letter, but that is done within assignments.
- Registry entries: Managing user registry setting (adding/changing).
- Environment variables: Configuring user environment variables.
- Ports: Configuring ports mappings. Personally, I don’t think this one is used much in this environment.
- INI files: Allows the creation of INI files or modifying existing INI files.
- External tasks: Makes it possible to run scripts (like CMD, VBS) in the user context to do all kind of tasks.
- File system operations: The possibility to copy folders and files into the user environment.
- User DNS: Creation of user-based ODBS connections.
- File associations: Assigning file types to specific applications.

If you are completely new to Citrix WEM, there are a few examples included for applications. But mostly, you need to set it up on your own. The configuration, however, is not that difficult. There are also some other community guys you can turn to who deliver some examples on their websites.
After configuring the UEM resources in the actions part, the next step is to add the user and machines to the Citrix WEM configuration. You need to import all the user/groups you want to use. Creating a new AD group won’t be automatically available; you need to add that one into Citrix WEM afterward. Don’t forget to add the OUs (the easiest way) where the agent resides, otherwise the agents won’t be synchronizing correctly.
Next are the filters. You start with setting up conditions. A condition is a specific trigger determined on a large set of available checks. Some examples are queries on Active Directory, registry, computername, IP ranges, and so on. The full list can be found at Citrix Docs.

To use the conditions, you need to add one or more conditions to a rule. It’s a good thing to keep the default always true for creating generic assignments. I also advise to make the rules as general as possible. Only create separate rules if they are really required. Rules are pretty powerful, but can also cause your configuration to become complex.
After defining the filters, the parts come together at assignments. At assignments, you will start selecting the user/groups as a starting point. Per AD object, you will start assigning the resources (actions) created earlier, by moving them from available to assigned. When moving them to assigned, you are prompted to assign a filter — that’s why the always true filter is important to have, as this is mandatory step. When assigned, you have the possibility to configure additional settings. A nice feature is the modeling wizard, where you can see the end-result of a user of all configured settings based on all groups.

Another part of the user environment management is configuring the desktop environment and taking care of retaining the user settings. The configuration of the desktop environment would normally be done via Group Policies and is often called lockdown of the system. Retaining the user settings is actually profile management.
Let’s start with the configuration of the desktop. Included in the installation resources is a template for lockdown. The template is a good starting point for your own configuration, but it may be a bit too restrictive. Walkthrough all tabs and enable/disable the settings for your own infrastructure. Import the template via the option Import Settings available in the Home ribbon.
WEM does not have profile management included, but it is integrating with other profile management products. For historical reasons, probably, the solutions of Microsoft (UE-V), Citrix Profile Management, and the old VMware Persona Settings are included. I guess Citrix will only focus on Citrix Profile Management for the upcoming versions.
System optimization with Citrix WEM
Besides the whole user environment set up, Citrix WEM is also known for the performance tuning of VDIs and XenApp servers. This part is available within System Optimization and is based on five main topics. I will walk through briefly on all five.
Fast logoff
On fast logoff you can enable this feature. This feature will arrange that the Citrix session will be disconnected directly and the logoff tasks will be executed in the disconnected session. From a user perspective, it looks like the logoff process is really quick.
CPU management
With CPU management, several settings are available for managing the usage of CPU resources. It starts with Enable CPU Spike Protection. Within this setting, a percentage can be defined. If this percentage is reached, the CPU priority will be lowered (which in normal condition will cause lower CPU usage). By enabling Intelligent CPU Optimization, the product will learn which processes are often touched by the CPU Spike Protection and will automatically start those processes with lower CPU priority (the same is also available for I/O optimization). You can also define the CPU Priority for processes manually on the CPU Priority tab. If needed/required, you can also do the same for each process for CPU Affinity (assigning a specific CPU to a process).
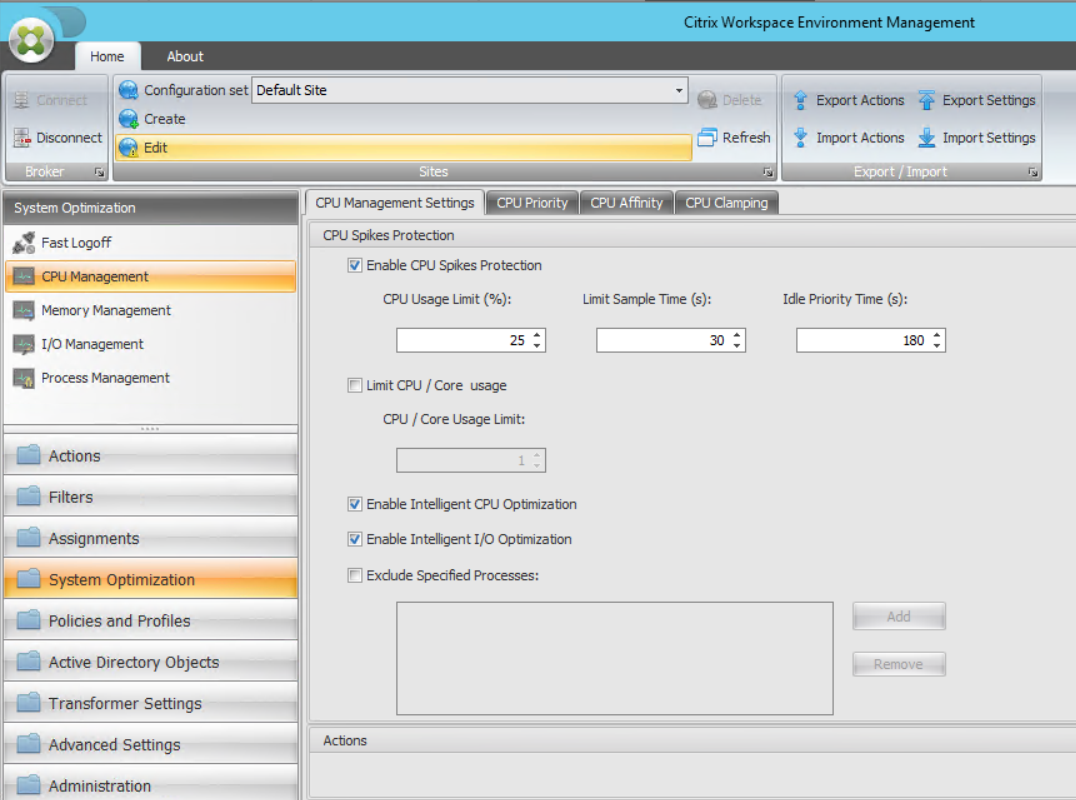
With the last option, CPU clamping, you can set up a maximum of CPU usage for (a group of) specific processes. So if you have bad-behaving applications, you can keep them under control via this option. This is a really powerful feature! Logically, on all parts you can exclude processes if they cannot handle being managed by Citrix WEM
Memory management
The third available option is memory management. When this option is enabled, excess memory will be released from applications that are idle (more memory will become available for other users).
I/O management
Within I/O management, you can configure a list of process that you would like to have I/O priority.
Process management
With this last optimization, you can control which processes are allowed to start or are not allowed to start. You first need to enable the functionality and decide if you would like to use whitelist (configuring which processes are only allowed to start) or blacklist (all processes will start except those in the blacklist).
Administrating Citrix WEM
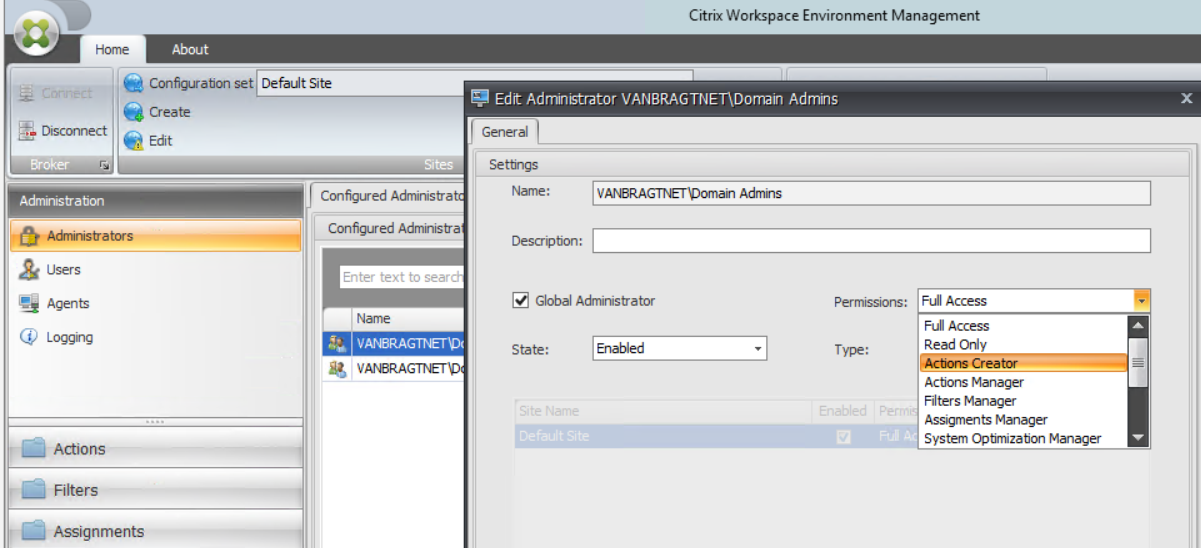
With configuring this part, we have actually touched setting up the end-user environment. The product also offers some functionality from a system administrator perspective. These are available within administration. Administration is divided into four components. On the first part, you can configure the administrators including delegation of control. Several types of permissions are available as shown in the below screenshot.
Administration also shows the users who have been working on a machine that has the Citrix WEM agent installed. Those agents are shown (including their status and connection) under agents. Logging is now available for more detailed information about Citrix WEM.
The last part I will touch on in this article is the monitoring component. There are three types of monitoring available:
- Daily reports: A daily summary of login times across all users connected and boot times across all devices.
- User trends: Reports available within this part are overall login trends, overall boot trends, and daily count of the number of devices.
- User and device reports: Login trends of a single user or boot trends for a single device in a selected period of time.

We are the end of this walk through. I was excited when the Norskale acquisition was announced, and I’m still happy that Citrix customers can use this product to optimize their Citrix infrastructures. When you use the product, be aware that especially in the actions part, configurations can become complex pretty quickly if you use many different rules and several assignments to several groups. Nevertheless, the product is really added value, so I would definitely recommend that you try it yourself and see if it has benefits for your infrastructure.



