Today’s data-driven world is closely followed by a need to safeguard it at all costs. This is why the security policies of most organizations today revolve around protecting the data and the resources that can provide access to them. But this hasn’t been as easy as it sounds given that most data and applications are stored in the cloud and are transmitted over the Internet. Also, the exponential growth of personal devices that connect to a company’s network to access data has compounded the problem — a problem made even more complicated by work-from-home employees and others working from remote locations. An organization has to use multiple tools and strategies to secure its network and resources and at the same time, give its employees uninterrupted access to data, regardless of where they are located. One such tool that has been playing an important role in helping an organization to strike a balance between data security and employee flexibility is Microsoft Azure. In particular, its Conditional Access feature has been at the forefront of this need for a balance.

What is Conditional Access?
Conditional Access policies are a key component of Azure Active Directory and are designed to work with the user identity. Based on the activities, roles, devices, and locations of a user, appropriate security policies are enacted to give them access only to the data they need and in a secure way.
At the heart of it all, Conditional Access is a set of if-then statements where a user gets access to data or applications based on the fulfillment of certain conditions like a multifactor authentication or even the requirement for a compliant device.
Risk-based approach
Conditional Access is a risk-based approach where the risk is calculated based on the details collected about a user and an intelligent analysis of the same. In fact, this risk calculation is interesting because it uses not just the data available about a user but also taps into the collective analyses and models that are present in Azure itself.
This way, the suggested policies tap into the consumer identity offerings and patterns that are way more than what an individual organization can have. Such an extensive analysis, undoubtedly, leads to smart and risk-based access decisions.
Finally, you can create organizational policies based on these decisions and implement them across all applications that are a part of the Active Directory including Microsoft 365, third-party apps, SaaS applications, or even apply them to specific lines of businesses that have federated access to AD.
As for the on-premises applications and older deployments, you can always use the Azure App Proxy to implement the same organizational policies.
This Conditional Access also plays a pivotal role in Microsoft 365 as it acts as the policy conductor to make it easy to enforce the necessary controls. Further, it integrates well with all of Microsoft’s offerings such as Defender ATP, Intune, and Microsoft 365, for streamlined implementation of your security policies.
Advantages of Conditional Access
Some of the advantages that come with using Conditional Access in Azure are:
- Protects user accounts with strong authentication that’s based both on location and risk.
- Protects data as it allows only managed devices.
- Meets compliance requirements.
- Strikes a balance between security and productivity.
- Helps to enforce fine control with policies such as encryption.
Now that you have a good idea of what Conditional Access is, let’s move on to its implementation.
Deploying Conditional Access
Deploying Conditional Access varies greatly between applications, so let’s look at some common use cases.
Authenticating users
Here is a step-by-step guide for setting up Conditional Access.
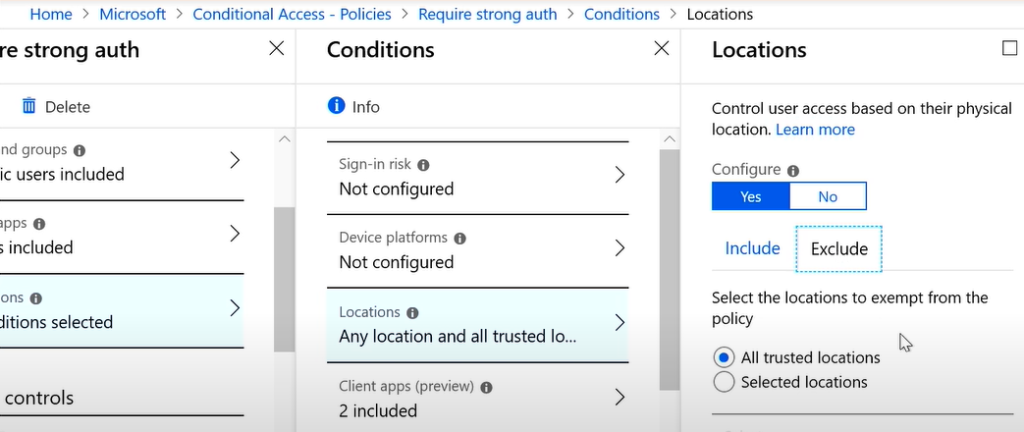
- As a first step, sign in to the Azure portal and navigate to the AD pane.
- Scroll down to the Security category and choose “Conditional Access.”
- On the right-hand pane, you’ll see a “+New Policy” option.
- This opens a form for Conditional Access. Give a name to your policy, as a first step.
- Next, decide the group of users and the apps on which you’re going to apply.
- Then, move on to the conditions. You’ll get a bunch of options such as the sign-in risk, device platforms, location, client apps, and more. Set your conditions accordingly. For example, to implement multifactor authentication for devices that are outside the organization’s network, go to the “location” option and choose “exclude” for trusted locations. This way, the condition will trigger sign-ins from unknown locations.
- Finally, make sure you choose “on” under the Enable Policy option. Save your choices and exit.
Thus, this is how you set up Conditional Access policies in Azure.
Ensuring device security
Earlier, we saw how to secure users. Next, we’ll talk about another scenario, which is to allow users to sign in only from a trusted device.

To do this:
- Follow the above steps and create a Conditional Access policy.
- Scroll down to “Access Controls” and on the right-hand pane, choose the “Grant access” radio button. You’ll get a list of options where you can decide if the device accessing your network is compliant with the established Intune policies or if you need to implement multifactor authentication.
- You can also choose to restrict access only to devices that are joined to your on-premise AD and registered within Azure Active Directory.
Combining policies
Now comes an important question. What happens when you have more than one policy that pertains to the same user or device group? Which policy takes precedence and what happens if there are conflicts?
Before we jump into the answer, let’s understand the basic difference between a condition and a grant.
Conditions vs. grants
Conditions are controls that are checked when authentication happens and access is provided when the authentication process matches the condition. Grants, on the other hand, are the required conditions that a device or user must follow to get into a system. In other words, if the conditions match, access is given. But the grants must match to gain access. So, grants are the finer controls within a condition.
In our above examples, location is the control while the specific rules that determine access are the grant.
Order of execution
So, how are the controls or grants executed?
First off, note that there is no specific order. All the conditions and grants are merged into a single policy. So, user access has to match all the grant controls from all the access policies to gain access to a resource within the network.
Now, the question is what happens in a conflict? The reality is that there is no possibility for conflicts because when the policies are combined, it will only make the access stricter. If you encounter a conflict in the rarest of cases, reach out to the Microsoft support team for a fix.
Here’s an example of such a conflict posted on GitHub that was eventually resolved by the Microsoft support team.
Conditional Access should not affect productivity
Thus, Conditional Access in Microsoft Azure is a feature that allows employees to access the company’s network securely. From an organization’s standpoint, it protects the company’s data and at the same time, allows employees to access it securely from any place, so their productivity is not affected.
We hope this gives you an idea of Conditional Access. Do let us know how you implemented it within your network.
Featured image: Shutterstock



