If you would like to read the other parts of this article series please go to:
Introduction
In part 3 of this multi-part article series revolving around Exchange hybrid deployment based migrations to Office 365 or more precisely Exchange Online, we installed and configured Active Directory Federation Service (ADFS) 2.0 on the two ADFS servers on the internal network. After we configured the servers, we verified they worked as expected.
In this part 4, we will continue where we left off in part 3. That is we will deploy the Active Directory Federation Proxy (ADFS) servers that are required for external identity federation with Office 365. More specifically, we will deploy and configure two ADFS Proxy servers. In order to achieve high availability, the ADFS Proxy servers will be configured in an ADFS Proxy farm and load balanced using Windows Network Load Balancing (WNLB).
Let’s get going…
Configuring Windows Load Balancing on the ADFS Servers
When configuring rich coexistence between an Exchange on-premise environment and Office 365, it’s crucial identity federation that works all the time. As already mentioned in previous parts of this article series, if the identity federation service becomes unavailable, it means that the Active Directory users within the enterprise cannot authenticate against an Office 365 service such as Exchange Online. Since the user cannot authenticate he cannot access an Office 365 service as he does not know the password set for the Office 365 user object itself. Because of this, it’s highly recommended to load balance all ADFS servers as well as ADFS Proxy servers using Windows Network Load Balancing (WNLB), a virtual load balancing appliance or a hardware load balancer solution. Since ADFS doesn’t require layer 7 based affinity, WNLB is fully supported.
Before we configure ADFS on the two ADFS Proxy servers, we’ll configure them in a WNLB. To do so, first install the ”Network Load Balancing” component. This can be done by opening the Server Manager and launching the ”Add Features Wizard” as shown in Figure 1. On the ”Select Features” page, check ”Network Load Balancing”.

Figure 1: Selecting the Network Load Balancing component
When the component has been installed, click ”Close” to exit the wizard.

Figure 2: NLB component installed
Now launch ”Network Load Balancing Manager” from ”Start” > ”Administrative Tools”.

Figure 3: Launching the NLB Manager
In the NLB Manager, select ”Cluster” in the menu and then click ”New”.

Figure 4: NLB Manager

Figure 5: Opening the New NLB Cluster creation wizard
In ”New Cluster: Connect” type the server name of the ADFS server you currently are logged on to then click ”Connect”.
Select the interface name listed and click ”Next”.
Note:
In this article series I’ll configure the Windows NLB in unicast mode which is the reason why I only have one interface connected to the server.

Figure 6: Specifying the name of the first node and the associated interface
On the ”New Cluster: Host Parameters” page, leave the defaults as is and click ”Next”.

Figure 7: Host Parameters page
On the ”New Cluster: Cluster IP Addresses” page, click ”Add”.

Figure 8: Adding a virtual IP address to the NLB cluster
Now enter the IP addresses (virtual IP address) that should accept incoming sessions for the Windows NLB cluster. When done, click ”OK” and ”Next”.
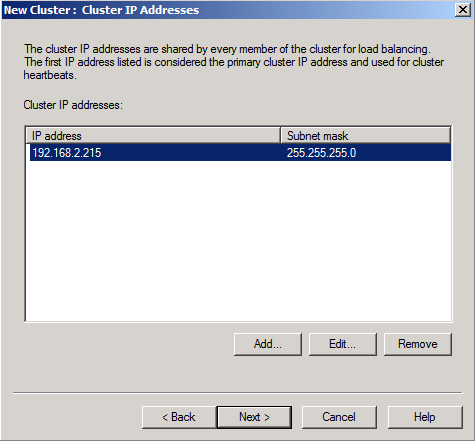
Figure 9: Virtual IP address
On the ”New Cluster: Cluster Parameters” page, enter the FQDN for the Windows NLB in the ”Full Internet Name” text field and then select the cluster operation mode.
In this article series, we use ”sts.office365lab.dk” as the FQDN and will run the Windows NLB in unicast mode.
Click ”Next”.

Figure 10: Specifying the full internet name and cluster operation mode
On the ”New Cluster: Port Rules” page, configure the NLB cluster to only listen on port 443/TCP.
Click ”Finish”.

Figure 11: Port rules
The NLB cluster has now been configured although only with a single node.

Figure 12: NLB cluster created
In order to add the other ADFS Proxy server as a node, right-click on the cluster name and then select ”Add Host To Cluster” in the context menu. On the ”Add Host to Cluster: Connect” page, enter the server name of the other ADFS Proxy server and then click ”Connect”. Select the listed interface and click ”Next”.

Figure 13: Specifying the name and interface of the other node
Leave the defaults and click ”Next”.

Figure 14: Host Parameters
Click ”Finish”.

Figure 15: Port rules
After a little while the other node has been added to the NLB cluster.
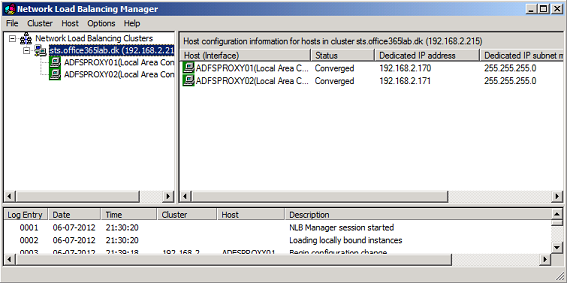
Figure 16: NLB cluster now includes two nodes
Okay, so although we now have a NLB cluster set with ”sts.office365lab.dk” associated with the specified virtual IP address, there’s no way traffic that hits ”sts.office365lab.dk” can be directed to the NLB cluster since the FQDN doesn’t exist in the external DNS.
So let’s open the DNS Manager on a domain controller in the Active Directory forest and add a new host record (A-record).

Figure 17: Creating a DNS record in external DNS
Name it ”sts” and then enter the public IP address that forward traffic to the VIP address that was set when the NLB cluster was created.
Adding ”sts.office365.dk” to the hosts file on the ADFS Proxy servers
Because the ADFS Proxy servers has been configured with the same virtual name (sts.office365lab.dk) as the ADFS servers on the internal network, we need to make sure that when the ADFS Proxy servers are going to route 443 traffic to ”sts.office365lab.dk” that it goes to the ADFS servers on the internal network. An easy way to achieve this is to add ”sts.office365lab.dk” to the local hosts file on each ADFS Proxy pointing to the VIP of the ADFS servers on the internal network.

Figure 18: Adding ”sts.office365lab.dk” to the hosts file on the ADFS Proxy servers
After having added ”sts.office365lab.dk” to the hosts file on both ADFS Proxy servers, open a command prompt and type ”nbtstat –R” to flush the NBT remote cache name table and then try to ping ”sts.office365lab.dk”. This should now resolve to the VIP configured on the ADFS servers on the internal network.
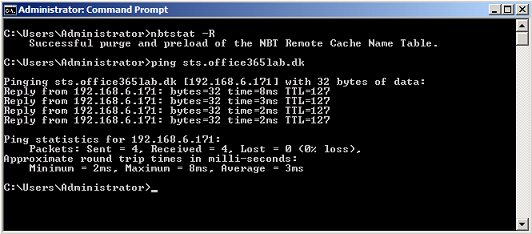
Figure 19: ”sts.office365lab.dk” resolving to the VIP configured on the ADFS servers on the internal network
Enable MAC Spoofing on the Hyper-V Virtual Machines
In this article series all servers including the ADFS Proxy servers are based on virtual machines in a Hyper-V environment. This means that we need to enable spoofing of MAC addresses on the interface for servers participating as nodes in an NLB cluster running in unicast mode. To do so, shut down each node and then open the property page for each respective virtual machine. On the property page, select the virtual network adapter, then check ”Enable spoofing of MAC addresses”.

Figure 20: Enabling spoofing of MAC addresses
Now start each cluster node again.
This concludes part 4 of this multi-part article in which I explain how you configure Exchange hybrid deployment followed by migrating to Office 365 (Exchange Online).
If you would like to read the other parts of this article series please go to:



