Introduction
Do you get remote support from IT professionals outside your company network? Do you provide remote support to users over the Internet? Have you evaluated the security concerns this may cause? One part of being an IT professional is to use remote support tools based on network access or screen sharing as a fast and effective way to help other people. There are many different tools but how do you make sure that these are secure and not compromising security?
I would like to take a look on some different types of remote access solutions that you can use for internal and external support. I will focus on what is possible to do with them and discuss how to choose a remote access solution that fits your company requirements and security policy.
What kind of remote access?
When I started as an IT consultant there were three ways to give support to customers, and the time spent on the different kinds was more or less like this:
-
46% on guiding the customer by phone
-
20% remote support from a terminal via a standard modem
-
33% driving to the customer
Security in the dial-up modem was based on credentials, phone number filtering and dial-back to a specific phone number of the username.
The remote support has changed quite a bit from dial-up modems to present online internet connection that most companies use for remote support. If I make the same evaluation on the support today it would look something like this:
-
23% on guiding the customer by phone
-
5% remote support from a computer via a standard modem
-
52% remote support from a computer via the Internet
-
20% driving to the customer
One of the main concerns today is not that time used for remote support percentage has gone up, but that the access to the customers has the possibility to also be used by “bad guys” if the security is not well configured and maintained.
Let us take a look on the different types of support tools in Figure 1. Notice that some of these can be combined for better security.
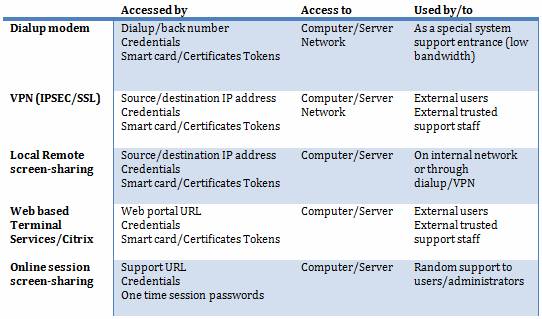
Figure 1: Different types of remote access solutions
For the dial-up modem and VPN connections you need additional remote screen-sharing programs if you need to connect to Windows computers and servers. Microsoft Remote Desktop is an excellent choice for this kind of access but do not allow the user to follow your movements on the screen. If only network communication to devices is needed, this kind of solution could be your choice (see Figure 2).
What do we need to consider?
To be able to choose a remote access support solution you need to know what requirements you will need for it. There are several things to consider before the choice of solution is made and I can give you a list of what to consider during the process.
-
Internal/external use
-
Launch Microsoft Office Outlook.Ink Security
-
Connection establishment
-
Cost of implementation
Internal/external use
Do you want to offer remote access support to your end users, external users or do you need to get support from external consultants? Defining the scope of users is important as you might increase security if connections need to be made over a public network such as the internet.
If external consultants need access to your systems, you need to plan on how much access you want them to have. If you want to provide/control the point of access and how flexible the solution should be this is of utmost importance.
For internal users that you need to help, consider how easily you can access their system and if this requires input from the user each time. If you support users that work from other offices and perhaps from home, where no direct connection could be established, then online sessions could be the choice of service.
Security
The main thing we need to consider is, of course, the security aspect. Both if you do or do not provide and manage the remote access solution yourself you need to evaluate the level of access delegated to external support staff. Before accepting remote support from external consultants please evaluate the following and related questions:
-
Secure Authentication
The remote user must be authenticated according to your company. Smart Card or certificate authentication with a password when establishing the connection is recommended for user identification. If normal credentials are used please have a good password policy or combine this with two-factor authentication. -
Secure Connection
Is the connection securely encrypted so no other person can get access to your information? -
Access level
Can the remote party access more resources than needed?
Is network access needed and to what scope of IP addresses/ports? -
File transfer
Is it possible to transfer files to/from your company network through the connection? -
Continuing access
When your current support session has ended, is it possible for the remote party to establish connection again?
In the solutions with network access, file transfer and access to remote local drives, you should be aware that worms and viruses have the possibility to infect your computers and servers. Screen sharing could be an excellent way of protecting you infrastructure both for internal and external users. As the customer you need to inform the remote party about the security requirements they need to follow.
Connection establishment
The next thing you need to examine is how the IT support staff connects to the destination computer/network. On internal computers you might want to connect to a computer/server with or without user interaction. For external consultant access, you will require some kind of interaction, control and logging of connections to your network infrastructure. If random support to or from other people can occur whilst they are on the phone, then I suggest an online session screen sharing with one-time passwords.
Cost of implementation
Some of these remote access types require more configuration and maintenance than others. You should examine how much time and money each of these require initially (for hard/software and installation) and if a subscription fee is needed.
Lining up the different remote access solutions
Below are some details about the solution, expanding on the overview I made earlier in Figure 2.
Dial-up modem
A point-to-point connection is made where network traffic is send through. Phone numbers can filter incoming calls and sometimes a pre-defined phone number used to callback. The dial-in servers usually has the ability to filter traffic based on access rules. This method has been used for many years but has a low bandwith.
VPN
Creating a secure tunnel for the traffic over a network connection is exactly what VPN does. VPN is mostly used for remote access but sometimes requires client software installed on the IT consultants’ computer. Sometimes multiple VPN clients can not be installed at the same time and it has different IP protocol/NAT requirements if used through firewalls, which can cause connection problems. The traffic that can come through the tunnel is controlled by the VPN device/firewall and can include subnets, single IP addresses and defined ports. VPN can be used internally and externally to secure network traffic.
Local Remote screen-sharing
This type of solution has a program installed (if not Microsoft Remote Desktop Services, a system service in Microsoft Windows, is used) on the destination computer/server. It makes it possible for the IT personnel to connect when this program is running. Typically, this is used if the IT consultant is using dial-up modem or VPN.
Webbased Terminal Services/Citrix
If remote users need to connect to company resources but direct access to the network infrastructure is disallowed, then, a Microsoft Terminal Services, Citrix or similar solution can be used. You can control the access to local and remote resources and minimize the danger of getting infected with e.g. a virus or worm.
Online Session screen-sharing
If you search the web for these types of remote support solutions you will notice a lot of different tools to choose from – some more secure and user-friendly than others. Common for most of these are the connection methods; the user that needs support accessing a webpage or launches a program that asks for a session ID/password. This will be provided by the IT consultant and the screen-sharing session will start.
Personally I like this kind of remote support as the end user accepts the connection, has the ability to see what is going on and it works in nearly any environment. Some of the solutions offer more features that can include connection afterwards without user interaction. Therefore you need to make sure that you trust the screen-sharing program that you or the external IT support staff offers. Check if the online service provider has been certified on the level that your company security policy requires. If file transfer and network access is disabled or not available threats from viruses and worms are minimized.
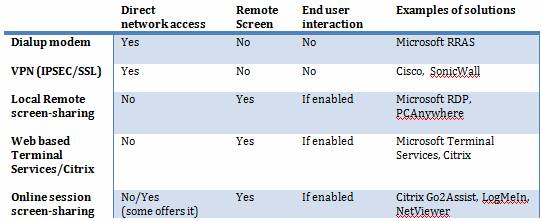
Figure 2: What the types of remote access solutions offer
Conclusion
Choosing the right remote support access solution can be a difficult task. I made a list of the most common choices of remote access and explained what these offer you. The questions can help you define the rules for remote access if your company gets support from external consultants or give support to others. Sometimes you choose between “very easy to use” and “completely secure” and my recommendation is to always go with the secure solution.
Dr. Thomas Shinder wrote an article about Microsoft’s Remote Access offerings that I would like you to read. He explains nicely the technical side of establishing secure connections and includes a bit of history also.



