To defend against something or someone, you first need to know everything about them. This also applies to the world of IT, which is constantly under the threat of devastating and expensive cyberattacks. The struggle between security professionals and cybercriminals is never-ending. To safeguard our digital environment, we first need to understand our own security mechanisms and how a cyberattack works. How can you defend yourself in this dangerous battleground? A cyber kill chain is a very effective means to conceptualize and understand the various phases and the workings of a cyberattack. It is a list of all the phases involved in an attack and describes every stage in a clear and systematic way. Here’s how a cyber kill chain can work for you.
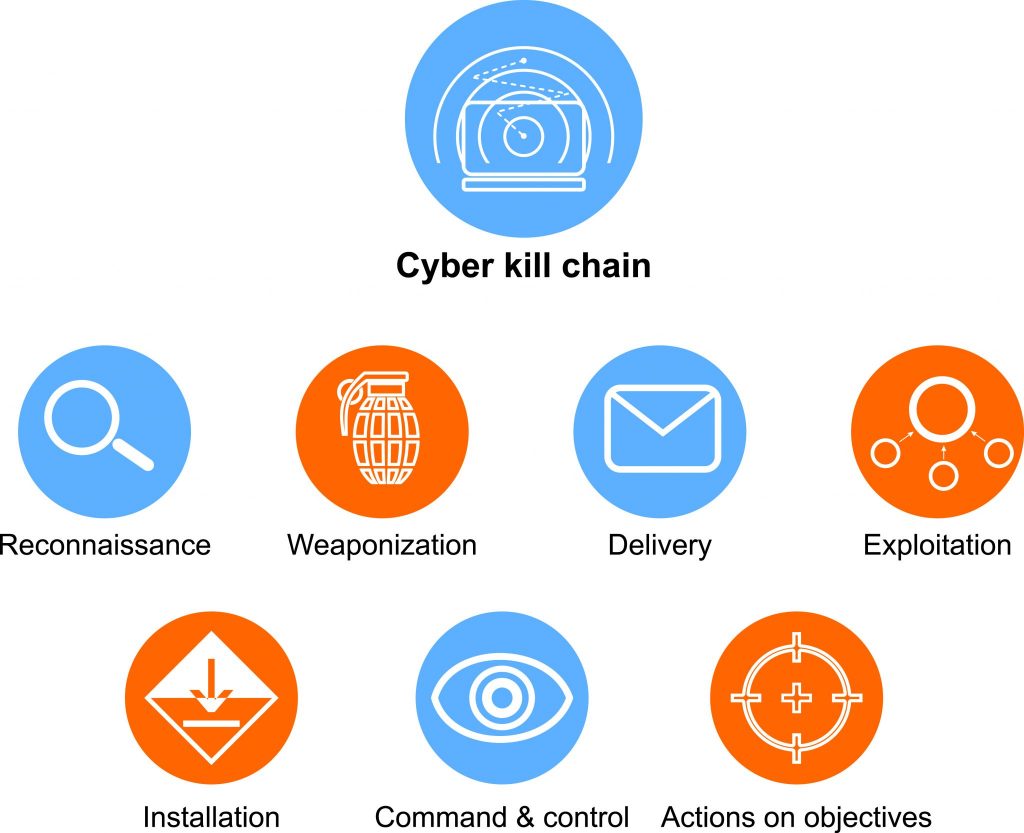
7 phases of cyber kill chain
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and control
- Actions on objectives
Reconnaissance
This is the first phase in the cyber kill chain, which usually happens long before the actual attack happens. As the name suggests, reconnaissance is the phase where attackers choose the targets. Before attacking, they usually, monitor the network system and try to understand the resources and other technicalities of the target.
In simpler words, reconnaissance is secretly viewing and analyzing your network from outside to find the vulnerabilities and loopholes. It is usually very difficult for an enterprise or a large organization to avoid this because the larger the number of employees and resources involved, the tougher it becomes to secure. In this phase, any employee within a company, any public network, an endpoint, even the social media information of the business, or any of its employees can be used to fetch the necessary information for the hackers.
Weaponization
Now that the hackers know about the vulnerabilities of their target, they start working on developing the weapons they will use to attack the victim. This is the phase where the attackers carefully craft an ideal cyber weapon such as a payload or malware to do the maximum damage to the victim. Like reconnaissance, weaponization also happens on the attacker’s side, without involving the victim.
Delivery
This is the transmission phase, in which the attackers send the malicious payload or malware to the victim by any of the possible intrusion means. There are several intrusion methods for the hacker to deliver the payload such as phishing emails, a web link, SQL injections, cross-site scripting, session hijacking, man-in-the-middle attacks, credential reuse, and more.
Exploitation
Exploitation is the first execution phase in a cyberattack. It is during this phase, wherein, the attackers start executing their malicious code in the victim’s environment by exploiting the victim’s weaknesses. Exploitation can be of a varied impact depending on the type of attacking tools or payload used. There can be simple burglaries such as exploiting minute configuration errors and on a larger front, they can exploit the vulnerabilities of the entire operating system and applications involved in an organization.
Installation
Now that the hackers have beaten the target’s security systems, they can start installing their malware and other malicious files in the victim’s environment. This is an optional phase in a cyberattack and comes into picture only when the attacker used a malware that installs on the target’s systems.
Command and control
During the command and control phase, the payload or the malicious files delivered and installed on the victim’s system starts creating a connecting channel to the attacker. The attackers can then remotely control the victimized systems and devices through the network and can take over the control of the entire affected systems from its actual owner/admin.
Actions on objectives
This is the final execution phase in a cyberattack. Now that the attackers hold the command and control of the victim’s system, what will be done is solely up to the attackers. They remotely start to carry out their intended goals to create chaos. The attack can be of multiple types: They can simply steal data, DDoS false traffic on the systems, demand ransom, or even collapse or corrupt the entire system. If the threat has got this far, there is nothing much that can be done by the victim.
Turning the tables
Rather than considering the cyber kill chain as just a model for understanding the structure and phases in a cyberattack, enterprises and their security professionals need to start weaponizing it against the cybercriminals. Every phase of a cyber kill chain not only explains a part of cyberattack, it also provides us with the valuable insights to stop the attack in its very tracks.
Enterprises need to be proactive when it comes to cybersecurity. No matter at what phase they are in a cyber kill chain, they need to stay strong and act accordingly. Among the seven phases of the cyber kill chain, reconnaissance, weaponization, and delivery phases are passive for the victims and take place behind the scenes at the attackers end. Since these phases are not relevant to the enterprise from an operational point of view, no direct actions can be taken against them by the security professionals. However, the remaining phases can cause severe damage to the business.

The visibility of a business has to be tightened for outsiders, and every employee must be given the right set of information and knowledge about best security practices. This way, modes of intrusion can be curbed, which will ultimately reduce the number of cyberattacks.
Security doesn’t solely rely on the firewalls, antivirus software, security architecture, or on security analysts. It takes everything to secure an organization from cybercriminals. A firewall might help you block malware from entering into your system, but if entered, a firewall is no longer of any use. Similarly, antivirus software has its own restrictions when it comes to performing malware checks. A security architecture can defend your company’s network systems, but all the endpoints of the enterprise will not be covered under it.
And always remember this: Even after taking all the right security measures, a cyberattack might still leave your organization devastated. So it is always advisable to have a proper backup of all essential data to at least minimize the impact and continue operating your business.
Photo credit: Shutterstock



