Most imagine war in terms of bullets and explosives. This is only natural as it grabs your attention far more than, for instance, a command line in Linux. The problem is, the general population seems to put cyber warfare on the same level as obtaining a nuclear weapon or other weapon of mass destruction. Governments themselves do not take cyber threats as seriously as they should either, especially considering how often high-level government breaches occur.

To show that these words are not based on sheer paranoia, I would like you to consider some recent words of technology pioneer Steve Wozniak. In a recent interview, Woz stated that “we used to fear the atomic bomb when I was young… now we fear all the cyberattacks and hacking. Could they really take out our electrical system, turn off our Internet? How far can it go? And it’s getting worse and worse year by year, not better and better.”
Think of how all of our technological advancements have become more interconnected over the years. How much effort do you think a terrorist or enemy government would have to go through to shut down major power grids? What about destroying sensitive intel that may determine the safety of a city? How about hacking into a UAV’s controls and using it to use hellfire missiles on unintended targets?
The new age of warfare consists not only of advanced weaponry, but truly the battle for information and control or destruction of all technological interfaces. The cyber battlefield encompasses numerous parties (hacktivists, private contractors, military), but the end attack almost always involves a government entity. With this in mind, let’s consider a few possible cyber war scenarios to see just how dangerous the times we live in are.

Shutting down nuclear facilities
A great deal of the developed world runs on nuclear power. As has been shown from tragedies like the Chernobyl meltdown of 1986 and others, a malfunctioning nuclear power plant can kill a significant amount of people. In the world of cybersecurity, especially with regards to cyber warfare, we have to consider the reality that these power plants and other nuclear facilities can come under attack via malware.
A lot of this concern stems from cyber weapons such as the infamous Stuxnet worm. In what was likely a joint attack by Israel and United States, the Stuxnet worm’s most famous attack attempted to dismantle Iran’s nuclear program. It was transmitted via a USB drive into an Iranian uranium enrichment facility’s operating system. The Natanz-based facility suffered centrifuge destruction due to the nature of the worm’s attack; this eventually caused a massive nuclear accident.
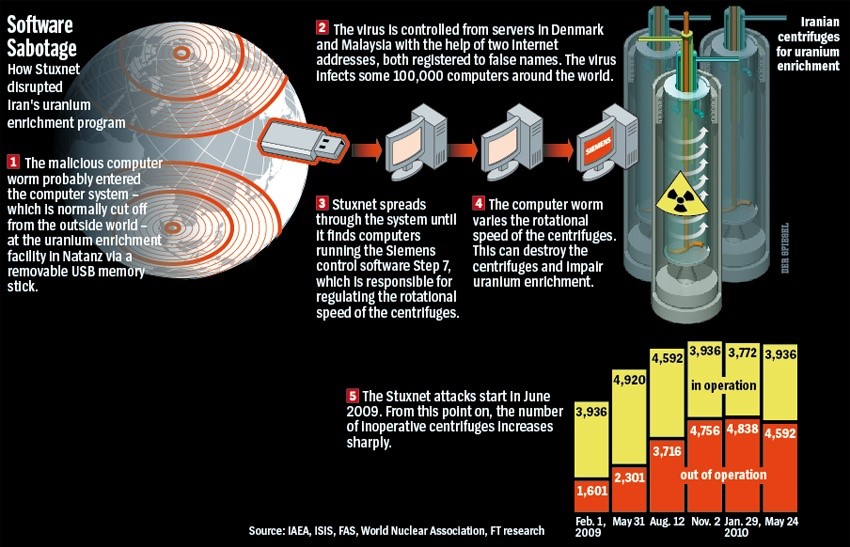
Anything related to energy is always a target on the cyber battlefield, and nuclear is easily the energy with the most catastrophic potential. The fact that a virus can cause a dangerous malfunction is just one cautionary tale of how serious cyber warfare has become.
Weapons systems
Understanding that anything technological can be hacked is the first step to comprehending the threat of cyber warfare. For some, however, this has not proven to be enough as countless systems have been compromised with nearly catastrophic results.
In this particular instance I speak of weapons systems, namely the technological networks that control them. One notable instance of a cyber-attack on weapons came in 2015. The German Patriot missile system, based along the Turkey-Syria border, started exhibiting the signs of a hack when it executed “unexplained commands.” The German government denied any such event, but many third party sources confirmed to the InfoSec community that there was a hack.
This is just one example, but imagine the implications here. We are talking about guided missiles coming under direct control from a hacker to be used for god-knows-what. The more the military has (justifiably) decided to rely on technology, the more vulnerable it has made itself. Most governments do not do enough to truly secure a system, even though they would like you to believe otherwise.

Stealing sensitive information
Arguably the greatest strategy in war is to fully understand your enemy, for then you will understand how to defeat them. In cyberspace, this translates to gathering (or rather stealing) classified data from rival nation-states. This type of attack occurs quite often and the examples are seemingly unending.
From the Chinese government stealing blueprints in American databases that show prototype weaponry, to the mass data dumps of whistle-blower organizations like WikiLeaks (who I admittedly support), the control of information is often the greatest weapon. Whoever controls information, for better or for worse, is truly in the position of having the upper hand in cyber war.
Information has, of course, always been an imperative, but now most of it is stored in massive electronic databases. Many of the governments that preside over these databases are generally unaware of the gaping vulnerabilities they have. The reason is a rather common one as it is commonly thought that strong firewalls will stop any would-be hacker. This a dangerous mindset to have, but it explains why the NSA and countless other agencies have been compromised.
Developing a global cyber war solution
Considering all of the inherent dangers that are present in the cyber battlefield, how can the global populace confront these issues? Frankly, answers are not totally apparent. It will require a meeting of numerous sections of society, from the government to independent security researchers and beyond.

The most logical place for finding solutions to cyber warfare globally is the United Nations. The U.N. has already put in some effort to address the biggest issue of war since the nuclear bomb. These efforts have led to some progress in dialogue, but the nations involved in said dialogue (China, Russia, and the United States) are consistently engaging frequent cyber-attacks.
This leads me to believe that more pressure must be placed on the United Nations to fully understand the threat of mutually assured cyber destruction. The countries that have a hand in U.N. resolution discussions must be brought to a consensus that we are on the brink of catastrophe. It will require either multiple disasters to facilitate this, this is the most likely reality. Perhaps, however the global InfoSec community can band together and convince their respective countries to fight for cyber warfare referendums.
The world is on the edge of a new age where our greatest threat can be also our greatest asset. Technology is a necessary and effective tool for life to continue advancing. It will, however, always be prone to exploitation by nation-states, terrorists, and other groups for destructive purposes. The sooner our planet understands this, the sooner we can find tangible solutions.
Photo credit: ExtremeTech



