
A business isn’t an island, so you can expect users on your network to be a mixed bag ranging from corporate bulls to cyberattackers. The question is who do you trust? Hopefully, internal business personnel should be trustworthy, yet what about those from outside your business? The answer comes in the form of a DMZ, also known as a demilitarized zone. This tool is a nexus where untrusted and trusted users can work on the network together.
In this article, I’ll delve into what a DMZ is and how you can use one to keep your business safe. First, let’s begin with what a DMZ is in the first place!
What Is a DMZ?
A DMZ is a perimeter network that protects your local area network (LAN) by assuming all users are untrusted by default. The DMZ provides an additional layer of safety and stops users from trying to access sensitive or valuable information on your business.
These networks allow you to use access control to protect your organization. They also prevent attackers from carrying out reconnaissance activities. Additionally, they help protect an organization from getting attacked through IP spoofing.
Now that you know what a DMZ is and how it protects you, let’s take a look at why you need one!
Why You Need a DMZ
A DMZ provides a buffer between an organization’s sensitive data and the outside world. This can be very useful when cybercriminals attempt to gain useful data for future attacks from internet-facing surfaces. If a cybercriminal web-scrapes a DMZ, they’ll only get exposed data in that zone. This could allow them to exploit the DMZ and gain access, but it won’t provide them with sensitive data.
DMZs have a zero-trust policy with everything configured to require explicit, and not inferred, trust to work. This means that even if an attacker gets into a DMZ, they have no choice but to try and find a way into your network from this location. Doing this in a zero-trust environment is challenging. Often, cybercriminals will look for weaknesses in your network to gain access to it, with them preferring the most simple route.
If they come across a DMZ, most cybercriminals would decide to use an alternative method of attacking you such as social engineering, email, or website injection attacks. Alternatively, you could try walking in through the door and attempting to leverage card reader exploits or a rubber ducky USB drop.
Now, you have knowledge of the power of a DMZ. Let’s talk about how you can create one for your organization.

How to Create a DMZ
An easy way to create a DMZ is by adding your DMZ servers or resources coming off the internet router and immediately after an external firewall. External parties will get routed to this DMZ’s location. You’ll also have your internal network connected to the same router using another firewall.
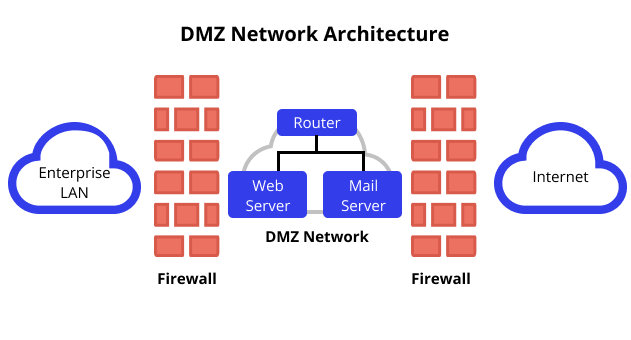
In the image above, you can see how a DMZ functions in your network. You can see the DMZ network right between your organization’s LAN and the Internet, with firewalls gatekeeping the DMZ on both sides.
Also, remember that you’ll need to create access control rules for outbound and inbound traffic for the ports used to stop external users connected directly to the internal network.
There you go! Now you know how you can easily create a DMZ! Let’s wrap up now.
Final Thoughts
DMZ networks are a staple for most businesses to help secure their sensitive and critical systems. In this article, I’ve discussed the benefits of a DMZ and how you can implement one successfully.
Make sure when creating a DMZ, that you configure the necessary access controls. The right access controls configured will provide a zero-trust environment. Also, don’t forget to disable ports that you’re not using. In any case, you should be doing that as part of your basic operation security procedure.
Do you have any more questions on DMZs? Check out the FAQ and Resources sections below!
FAQ
What is a DMZ network?
A DMZ, or demilitarized zone, network is a perimeter network that protects your local area network (LAN) by assuming all users are untrusted by default. It contributes to having a zero-trust policy in a controlled environment. In turn, this helps reduce attack surfaces on critical data. Also, a DMZ provides a buffer that stops users from accessing sensitive and valuable information on your business.
What does a DMZ network protect my business from?
A DMZ network prevents attackers from carrying out reconnaissance and scraping activities of personal or core targets. It also helps protect an organization from getting attacked through IP spoofing. Consider using a 4th-generation or above firewall as a service (FWaaS) to help protect your cloud or cloud-hybrid environments.
What is network segregation?
Network segregation lets you control where certain users or traffic can access and work. One example is the use of a DMZ. It assumes that all users within it are untrusted and configured to require explicit, and not assumed, trust. This helps keep away cybercriminals from sensitive or critical data in your business.
Should I use network segregation in my business?
It’s useful to have different types of network segregation depending on the level of trust. For instance, core business servers on-site may be both physically and digitally segregated from users other than administrators. A demilitarized zone (DMZ) network is a perimeter network that allows you to grant access to resources to untrusted users and acts as a buffer between trusted and untrusted users.
How do DMZ networks improve security?
DMZs have a zero-trust policy with everything configured to require explicit, and not inferred, trust to work. This means that even if an attacker gets into a DMZ, they then have to find a way from this location to attack the rest of your network. Doing this in a zero-trust environment is problematic for them, so you should consider using a DMZ for this reason.
Resources
TechGenix: Article on Firewall as a Service (FWaaS) Providers
Learn how FWaaS can help protect your cloud or cloud-hybrid business.
TechGenix: Article on Network Segregation
Discover how you can improve your operational security with network segregation.
TechGenix: Article on Zero-Trust Policies
Get more information about zero-trust policies.
TechGenix: Article on Network Migration
Find out what you need to migrate your local area network to the cloud.
TechGenix: Article on Types of Malware
Learn the malware you’ll see in the wild and how to protect against them.



