Endpoint Detection and Response (EDR) security is one of the methods you can use to protect your endpoints and reduce the risk of cyberattacks. Wait, but what is an endpoint and why do you need to secure it? Any device that connects remotely to a network is a network endpoint. Your company’s corporate network typically has several thousand endpoints. These include smart sensors, workstations, desktops, servers, printers, and other peripheral devices.
Employees also use personal devices like smartphones, laptops, and tablets to log in remotely, which further increases the number of endpoints. These endpoints create security vulnerabilities because cybercriminals can use them to gain unauthorized access to your confidential data.
In this article, I will explain what EDR is and discuss different tools you can use to improve your EDR security.
Let’s dive right in!
What Is EDR?
Endpoint detection and response is a cybersecurity solution that automatically detects and responds to endpoint threats. EDR tools monitor and analyze endpoint usage, identify suspicious behavior, and notify the company’s IT team, so they respond promptly to attacks. EDR security protects your network by detecting endpoint attacks, containing them, and preventing them from spreading further.
Now that you know what EDR is, you may wonder why it needs special attention from your company’s cybersecurity team. Let me explain.
Why Is EDR Security Important?
Due to their flexible working arrangements, most companies allow employees to access corporate networks through their personal devices. This means employees are responsible for ensuring devices are secure. Carelessness on the employee’s part creates a significant vulnerability for your company’s IT security.
For example, employees may forget to install antivirus updates and accidentally download a malicious virus. When they log in, the virus will mask itself as a trusted device and successfully bypass your usual security measures to wreak havoc on your network.
Cybercriminals then exploit endpoints and run malicious software that leaks data and encrypts or locks your IT systems. This disrupts normal business operations and causes substantial financial losses. EDR rsecurity protects you from attacks by giving your security team:
- Full endpoint visibility from a single console where the EDR security solution collects and displays data from all connected devices
- Faster investigation because your security team can rapidly gain context about security incidents from the EDR data collection
- Automatic remediation as EDR tools use predefined rules to respond to suspicious activity
Of course, you can’t implement EDR security without understanding the technology. I’ll explain in detail how EDR works and the different components in any EDR solution.
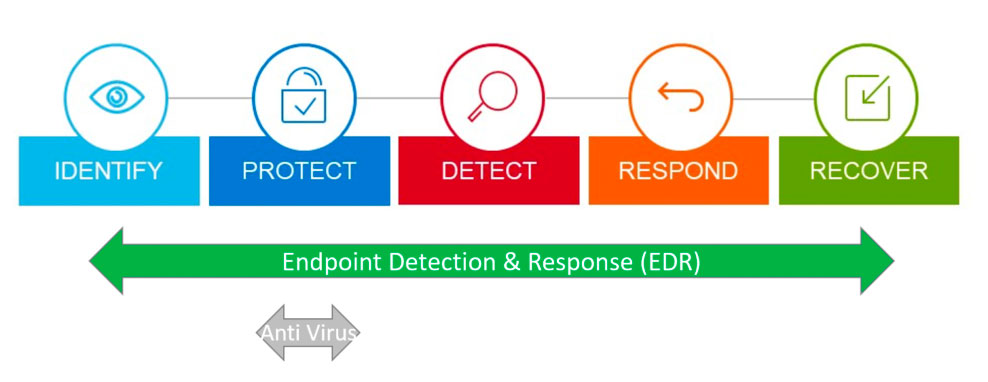
How Does Endpoint Detection and Response Work?
Any EDR security solution typically has 2 capabilities—detection and containment—that work together to secure all your endpoints. I’ll explain them in detail below.
1. Threat Detection
EDR security typically installs software agents on all endpoints, including new endpoints that join the network. The software agents collect data like authentication attempts, event logs, file data, and running applications from each endpoint. The EDR solution then uses machine learning and artificial intelligence to identify suspicious patterns in the collected data.
In turn, security teams get an automatic alert when any suspicious activity is detected. For example, if a file on an endpoint device starts exhibiting ransomware activity—like encrypting other files—EDR will detect the behavior. It’ll also alert your company so that you can take action.
2. Threat Containment
Once EDR security detects a threat, it immediately takes steps to contain the infection. For example, it can block the device, or isolate specific areas of the network. Prompt automatic action limits damage and protects your data before your cybersecurity team responds to the threat.
The EDR security solution also retains all data related to the attack for your team’s post-attack analysis. You can also use the data to implement new policies that prevent similar attacks from reoccurring in the future.
Now that I have explained how EDR works, I’ll review some tools you can use to get started with EDR security today!
Top 3 EDR Security Tools
After extensive research, I think the 3 best EDR tools on the market are GFI LanGuard, Crowdstrike, and Trellix.
1. GFI LanGuard

GFI LanGuard is a comprehensive EDR solution that lets you manage and maintain end-point protection across your network. It provides automatic visibility into all network elements, helps you assess potential vulnerabilities, and supports automatic software patching and updates. With GFI LanGuard, you can:
- Discover all network endpoints and elements automatically, including devices, virtual machines, switches, and routers
- Group your devices and distribute management responsibilities between different teams
- View all your endpoints from a central management dashboard
2. Crowdstrike Falcon Insight EDR

Crowdstrike’s Falcon Insight EDR continuously monitors all endpoint activity. This way, you can know exactly what’s happening—from a single endpoint to the entire company. You get:
- Continuous raw event recording for unparalleled visibility
- High-performance memory scanning of all endpoint devices to detect the most stealthy attacks
- Powerful response actions, including remote access to your security team so they can quickly remediate compromised systems
3. Trellix Endpoint Security

Trellix Endpoint Security (previously called FireEye) protects your endpoints against known and unknown threats. You can accelerate attack response because of their precise threat detection and unified endpoint management. Trellix Endpoint Security gives you:
- Improved EDR quality with relevant data
- Fully integrated malware protection and remediation
- Comprehensive analysis to conduct exhaustive inspection and investigation
I hope one of these will fit your EDR requirements. Now for a quick recap!
Final Thoughts
Endpoint detection and response is a cybersecurity practice for securing and protecting your network endpoint devices. EDR security solutions aggregate and automatically analyze data on endpoints to discover malicious activity and anomalies. They also enable security teams to identify, investigate and respond to incidents quickly. As a result, EDR security should be a high-priority component of your company’s cybersecurity strategy!
Have more questions on EDR security? Check out the FAQ and Resources sections below!
FAQ
What is the difference between endpoint protection and endpoint detection?
Endpoint protection (EPP) refers to cybersecurity solutions that prioritize threat protection before endpoints are attacked. On the other hand, EDR tools assume that you can never have complete protection and must prepare for an attack. EDR security helps you respond faster and more effectively to cyber-attacks and incidents.
What is the difference between EDR and MDR?
Managed detection and response (MDR) is a third-party service that helps your company respond to cyberattacks. In case of an attack, an external third party implements measures to stop the attack. On the other hand, EDR is a branch of cybersecurity that focuses on responding to attacks specific to network endpoints. You can implement EDR yourself or via a third party.
What is the difference between EDR and XDR?
XDR is the evolution of EDR. While EDR is limited to detecting malicious activity on network endpoints, XDR goes beyond that to automatically detect cyberattacks on servers, network devices, and the cloud.
Can EDR replace antivirus?
Yes. EDR security can replace traditional antivirus. EDR solutions typically include all traditional antivirus features, such as monitoring network activity and detecting virus patterns. But they also go above and beyond to include automatic threat detection and response.
Does EDR stop ransomware?
Yes. EDR solutions can stop ransomware and all other cyber threats. EDR security automatically detects ransomware behavior, like encryption, and notifies your cybersecurity team to take action. Finally, EDR can also block the ransomware and prevent it from spreading across the entire network.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: Article on Integrating EDR with a VPN
Read more about what to do when your SSO, EDR, and MDM solutions don’t play well with VPN.
TechGenix: Article on Managing Endpoint Devices in a Hybrid Cloud
Learn how to manage endpoint devices in the hybrid cloud.
TechGenix: Article on Endpoint Security Best Practices
Discover more endpoint security best practices.
TechGenix: Article on Implementing Endpoint Security within a Budget
Read about how to implement endpoint security within budget.



