
Email is the most important means of business communication. It’s also the cheapest, fastest, and most accessible option. You can also use emails to communicate easily with individuals or groups. That said, due to its large-scale usage and accessibility, email is one of the largest cyberattack vectors. Clearly then, email security is very important.
That’s where the need to meet strict email compliance requirements comes in. Email security ensures the safety of the data, identities, and information transmitted over emails. Email compliance also ensures that the transmitted data in the email meets the requirements of all the regulatory and governing bodies involved.
In this article, I’ll explain what security and privacy steps you can take to help you stay email compliant. I’ll also walk you through creating an email compliance strategy and the top email compliance frameworks and tools. Let’s start with the definition first!
What Is Security and Privacy Compliance for Email?
As I mentioned, emails are an easy, fast, and efficient means of business communication. They’re not secure. In fact, anyone intercepting the emails can read their contents. Luckily, governments and regulatory bodies have set specific requirements to protect individuals and corporations. GDPR, CCPA, HRPA, and PCI DSS are some requirements. These regulatory bodies oversee the rules, regulations, and data security practices a company implements, including the emailing systems.
Any growing company leverages email marketing to acquire an audience and scale its business and operations. So, you need to know the laws around email marketing before you start doing it.
Email Marketing: 5 Regulatory Bodies and Frameworks
A large volume of personally identifiable information (PII) could be at risk of cyberattacks through unsecured email marketing. To prevent these mishaps, governments and governing bodies across the globe have defined their laws and regulations. Companies planning to do email marketing must also follow these guidelines. What are these guidelines, though? You’ll find different laws worldwide that guide the use of email marketing for commercial purposes in specific nations or provinces.
Here are 5 of the data regulatory bodies and frameworks:
1. HIPAA
HIPAA (Health Insurance Portability and Accountability Act) is a data security and protection law. The Department of Health and Human Services in the United States introduced this law. HIPAA’s main objective is to protect the patients’ data like medical and health information. This information could be about doctor visits, drug and medication details, etc.
2. SOC 2
The AICPA (American Institute of Certified Public Accountants) first introduced SOC 2 (Service Organization Control). This process provides effective security and compliance standards for a company’s security, integrity, privacy, and confidentiality. SOC 2 also cares about the availability of the services that the company offers.
3. GDPR
General Data Protection Regulation (GDPR) is a European law. It regulates the policies and laws in place for data privacy and protection in the European Union and the European Economic area. All companies dealing with European citizens’ data must also comply with the GDPR policies.
4. CAN-SPAM
The CAN-SPAM (Controlling the Assault of Non-Solicited Pornography And Marketing) is a law passed first in 2003. It serves as the United Nation’s first law in place to regulate commercial emails and email marketing. CAN-SPAM also covers all commercial messages and does the same for B2B and B2C companies.
5. CASL
CASL (Canada’s Anti-Spam Legislation) is a Canadian law that regulates and protects individuals (consumers) and businesses from digital threats and misuse of technology. This law has been protecting Canadian nationals from several forms of digital threats like SPAM attacks, malware, and phishing attacks since 2014.
Next, let’s look at ways to stay email compliant.
Practices to Stay Email Compliant
Some of the most important aspects of email marketing that allow you to comply with email marketing laws and regulations are as follows:
- Ensuring you have permission to email people
- Avoiding the use of misleading headers
- Avoiding sending explicit content
- Ensuring you identify your email as an advertisement
- Including your sender’s details like email address and registered address
- Providing users with a choice to opt-out of the email subscription
You must follow all laws and regulations. Moreover, it’s your responsibility to take ownership of the email marketing campaign even though you outsource it to a different firm. Assessing the rules corresponding to your business, educating your employees, and following industry trends are great ways to ensure email compliance.
Now, let’s see some tips you can use to set up a strong email compliance strategy for your company.

9 Tips for an Effective Email Compliance Strategy
Setting up and having an email compliance strategy is very crucial for any industry or business. This helps you stay safe against the growing cyberattacks. It also helps you avoid heavy fines and legal troubles.
Here are 9 of the best tips you should follow while setting up an email compliance strategy:
- Understand the global compliance landscape and the regulations that apply to you based on your areas of operations and the data you deal with.
- Ensure your users consent to you using their data in any shape or form.
- Have an email and data archiving solution in place that’s compliant.
- Maintain detailed record keeping of all the data.
- Use a dedicated IP address to send out newsletters to your subscribers.
- Update your list of subscribers regularly and churn the data as needed.
- Allow your target audience to opt in and opt out when needed.
- Use authentication protocols and strong web security practices.
- Schedule regular data audits.
Now, let’s look at some of the very widely used email security tools and providers.
The Top Three Email Security Tools & Providers
Email tools and providers help you better manage your audience and data. They can also help you stay compliant with laws and regulations. Here are the top 3 email security tools and providers:
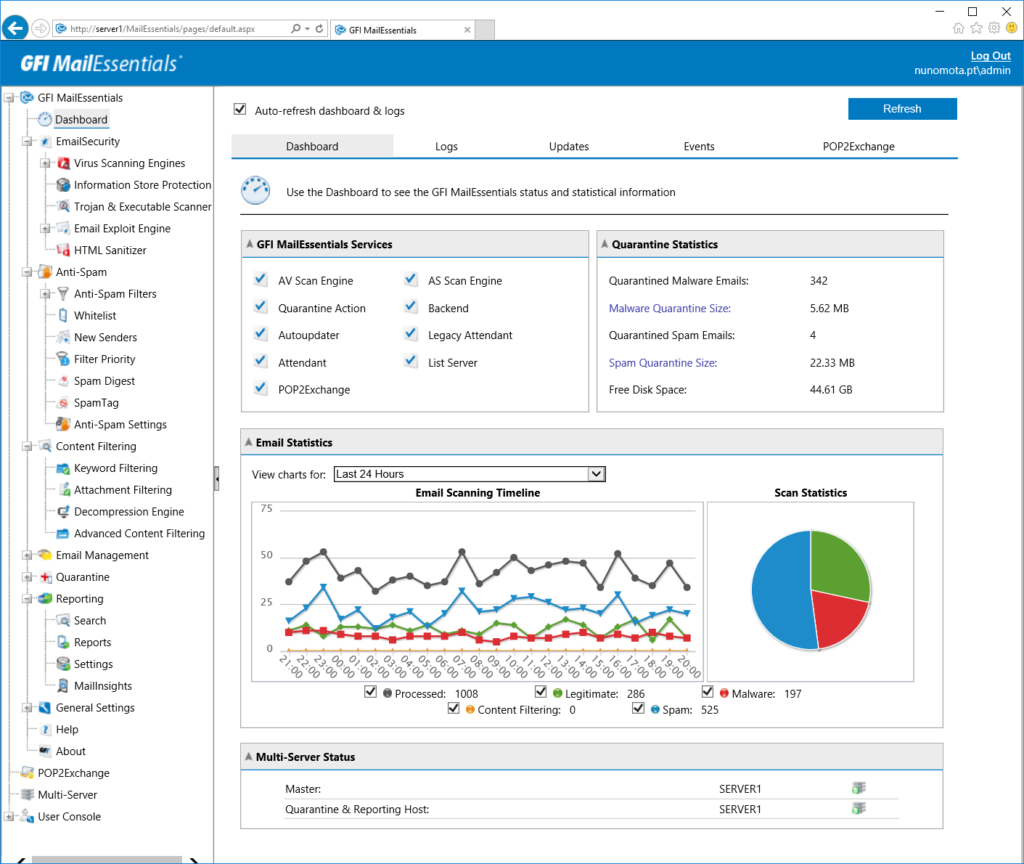
1. GFI MailEssentials
GFI MailEssentials is one of the most widely used, robust, and secure anti-spam and email security solutions for on-premise mail servers. It offers 14 anti-spam filters and 4 antivirus engines to protect you against malware. It also allows you to control and configure all these antivirus engines together for a hybrid security solution. Moreover, it offers several other features like advanced malware protection, integrated reporting, quarantine management, protection against email exploits and trojans, etc. Visit the GFI Mail essentials page to learn more about the product.
Pros
- Easy to install and configure
- Abundant pre-made templates and filters for protection against spam
- Sturdy archiving option
Cons
- Monitoring can be improved to provide more granular information
2. Mimecast
Mimecast is an AI-powered enterprise email security service that can help you protect your data and emails while providing a robust archiving option. This service works the best with Microsoft 365 and Google Suite. It can also help you prevent data loss, enhance brand protection, and prevent ransomware and other security attacks. Moreover, it offers several other security features like URL protection, attachment protection, browser isolation, and internal email protection.
Pros
- Ease of setup and integration
- Attachment sandboxing
- Impersonation protection
Cons
- SPAM and email filtering
3. Zoho Mail
Zoho Mail is an inexpensive yet powerful email solution that allows tight integrations with a full suite of collaboration tools. This solution is also known for its top security solutions and privacy protection for the users and the associated data. It also provides you with an executive control panel that serves as a one-stop shop for you to manage your entire service.
Pros
- Flexible data and email retention
- Available mobile application
- Easy email and calendar migrations
Cons
- Tricky application navigation
- Unintuitive storage capacity management
Final Words
Email security and compliance are crucial for any business across the globe. Understanding and establishing strong email security and compliance guidelines across your company can help you tackle several cyberattacks and potential data breaches.
In this article, you’ve learned the importance of email security and compliance. I also showed you some of the most significant security and compliance frameworks and authorities. You also learned some tips to stay email compliant and some of the top email solutions available in the market.
Have any questions about email security and compliance? Check out the FAQ and Resources below!
FAQ
What is data compliance?
Data compliance is a practice that ensures data protection. To achieve this, several governing bodies have set regulations in their respective countries. These regulations include rules and protocols for handling, storing, collecting, and using data.
What are some of the common email attacks?
The most common email attacks include identity theft, phishing, virus and trojans, and spam emails. These attacks can also lead to ransomware attacks, loss of data, and loss of service. They may also result in DDoS and several other cyberattacks.
What is PII?
PII (personally identifiable data) refers to the information used alone or with other relevant data to identify an individual. PII may refer to national or domestic identity documents like passports and driving license information. You should always protect your users’ PII.
What are B2B and B2C models?
B2B, business-to-business, refers to companies performing transactions with other companies for the business. This can be a company providing services to other companies. B2C, on the other hand, refers to business-to-consumer where a company offers services directly to individuals or consumers.
What is data archiving?
Data archiving is a process of preserving inactive or old data by storing it in dedicated databases or repositories for long-term retention and record keeping. You can use archived data to restore the data if it ever gets lost. This archive also can serve as a point of reference. You can also use it for audit, regulatory, and compliance purposes.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: News
Explore the latest news in the IT enterprise world.
TechGenix: Article on Governance, Risk, and Compliance
Learn more about governance, risk, and compliance and their role in securing organizations.
TechGenix: Article on Data Privacy Regulations
Discover more about different data privacy regulations and how you can walk through them.
TechGenix: Article on Data Management Challenges and Opportunities
Learn more about the key data management challenges and opportunities for SMBs.



