Introduction
To increase security in your terminal services environment, you should consider using Single Sign-On (SSO) technology. Because of the complexity of IT systems and network environments, many companies suffer from supporting multiple authentication methods across multiple (and sometimes disparate) systems. Distributed environments pose many challenges. Since distributed environments imply independent security domains, it is important to view SSO as a way to create one single security domain (adding all secondary domains) for ease of access and manageability. The goal is to create the appearance of a centralized system if you cannot create a single instance in the first place. Many users typically have to sign-on to multiple systems when they would only need to sign on one time with one set of credentials using SSO. SSO works to help to alleviate these issues.
What is SSO? SSO is defined as a process or solution that will create a single ‘authentication’ of a user valid to all other participating systems. SSO will allow a user to authenticate and have authorization to permit or access all computers and/or systems where he/she has access permission without the need to enter multiple passwords. The only main disadvantage to this design is that when using SSO technology, although you create an architecture that is ‘user friendly’, the issue you may face is that all users, hosts and applications must ‘trust’ the same authentication mechanism. If this authentication mechanism is secure, and you are testing it correctly, then you should not face any issues using SSO technology.
When working with Terminal Services, SSO can be very desirable to help aid the complexity of users trying to attach to a system and having to log on every time they attempt to connect to a system that requires authentication. With Windows Server 2008, SSO can be implemented with the Terminal Services Role very easily.
Using SSO with Terminal Services
Single Sign-On (SSO) is an authentication method that allows users with a domain account to log on once. They do this by using pre-established credentials (a password or smart card) to access systems without being asked for credentials multiple times. To implement single sign-on functionality in Terminal Services, ensure that you meet (and for production systems – exceed) the minimum requirements. The basic requirements needed to implement SSO are:
- You can only use single sign-on for remote connections from a computer running Windows Vista or Windows Server 2008 to a Windows Server 2008 Terminal Server.
- You must ensure that the user accounts that are used for logging on to the Terminal Server have appropriate rights to log on to both the Terminal Server and the Windows Vista/2008 client computer.
- Your client computer and Terminal Server must be joined to a domain. In this example, in this article we are using the TESTDOM domain.
Understanding what the basic requirements are, more specific requirements for setting up SSO, is as follows:
Servers:
- Windows Server 2008 Terminal Server with TS Server Role and TS Licensing Server Role enabled
- Windows Server 2008 Domain Controller (Active Directory)
- Proper Hardware Requirements
Note:
Although you can make a DC a Terminal Server, it is recommended that you split the roles and use separate servers based on the load that is expected. Obviously, whenever implementing a production system, you will want to make sure that you know what your application/traffic flows are and what load your users and the application puts on your network as well as the individual servers connected to it.
Clients:
- Windows Vista (or Windows Server 2008 used as a client system)
- Remote Desktop Client (RDC) with Network Level Authentication (NLA) Support. NLA support is only available with RDC 6.0 and with Vista or 2008.
- Proper Hardware Requirements (exceed as needed)
A layout of the test lab used to simulate this exercise is seen in Figure 1.
Figure 1: The Terminal Server Test Lab
To configure the recommended settings for your Terminal Server, complete the following steps:
Configure authentication on the Terminal Server, this can be done with AD, or locally on the server you want access to.
Configure the computer running Windows Vista to allow default credentials to be used for logging on to the specified Terminal Server(s) on your network.
You need administrative privileges on the Terminal Server you are configuring.
Now that you know what you need, let us begin configuring SSO with Windows Server 2008 Terminal Services.
Configure Authentication on a Terminal Server
First, verify you have a working Terminal Server. Check the Server Manager as seen in Figure 2 to verify that you have the correct Terminal Services roles installed and operational. Remember, you will need to have (at minimum), the Terminal Services Role and the Licensing Server Role installed and ready to configure SSO.
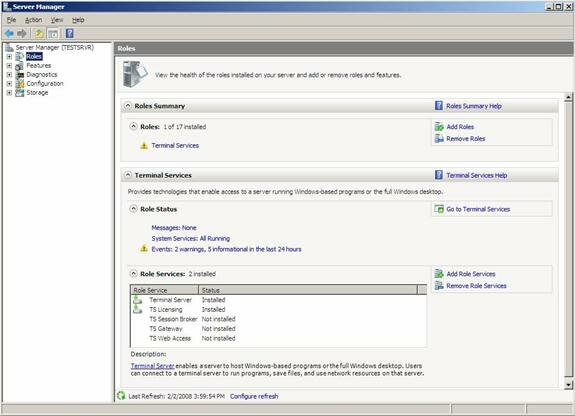
Figure 2: Viewing Server Manager
Next, we will configure Single Sign-On (SSO) on the Terminal Server by opening Terminal Services Configuration. Go to Start => Administrative Tools => Terminal Services, and then click Terminal Services Configuration.
Once you open the Terminal Services Configuration console, find the Connections pane. You should, at minimum, have the default connection in place which should be RDP-Tcp. To configure this (or any other connection) right-click the appropriate connection and then click Properties, as seen in Figure 3.
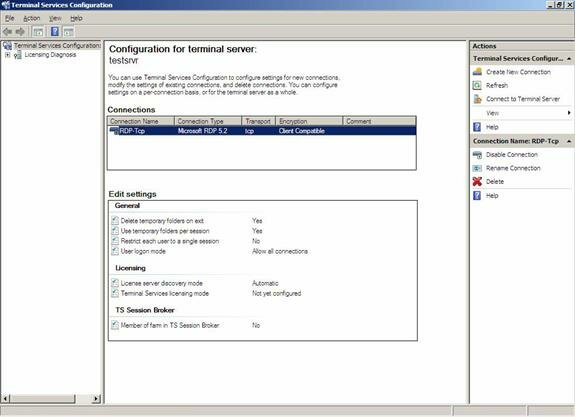
Figure 3: Viewing the Connection
Once you open the Properties dialog box, on the General tab as seen in Figure 4, you can verify that the Security Layer value is set to either Negotiate or SSL (TLS 1.0). Negotiation will allow the system to ‘negotiate’ with a client what type of Security Layer is needed.
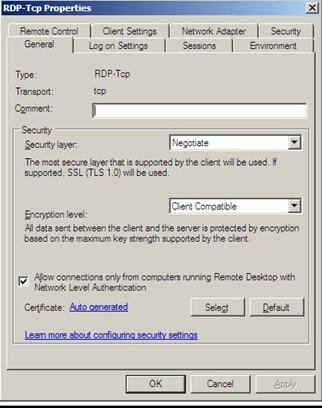
Figure 4: Configuring the Security Layer
Figure 5 shows you how to configure different Security Layers, to include RDP, SSL or Negotiate.
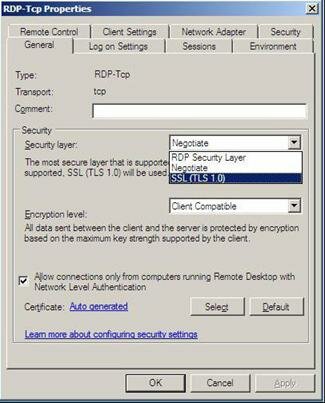
Figure 5: Adjusting the Security Layer for RDP, SSL or Negotiate
Once you finish selecting the Security Layer, click on the Log in Settings Tab as seen in Figure 6.

Figure 6: Configuring the Log on Settings
On the Log on Settings tab, ensure that the Always prompt for password check box is not selected or checked, and then click OK to close the RDP-Tcp Properties dialog box.
Now, you have configured authentication, next we will configure the default credential usage to be used with SSO.
Allow Default Credential Usage for Single Sign-On (SSO)
Now that we have authentication configured, we need to finish the process. To do this, you need to go to the client system (Vista, or 2008) and configure the Local Group Policy Editor. On your client computer open the Local Group Policy Editor. To open Local Group Policy Editor, go to Start, and in the Start Search box, type gpedit.msc and then press ENTER. This will launch the Local Group Policy Editor in a Microsoft Management Console (MMC) as see in Figure 7.
Figure 7: Configuring the Local Group Policy Editor (gpedit.msc)
In the Editor, look in the left pane and expand Computer Configuration => Administrative Templates => System => and then click Credentials Delegation. Double-click the Delegating Default Credentials setting to open it as seen in Figure 8.
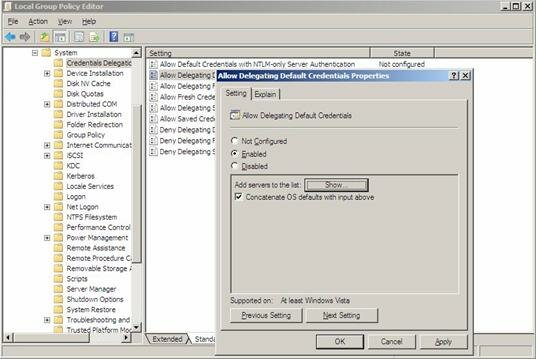
Figure 8: Configuring the Default Credentials Setting
Next, in the Properties dialog box on the Setting tab, select Enabled, and then select Show. In the Show Contents dialog box, click Add to add servers to the list as seen in Figure 9. In the Add Item dialog box, type the prefix termsrv/ followed by the name of the Terminal Server you will be connecting too. In this example we would specify it as:
termsrv/USNYTS01
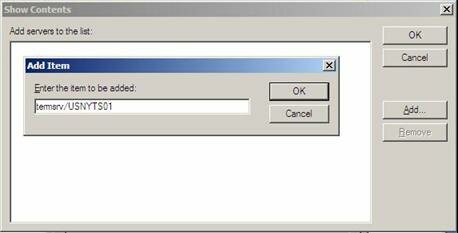
Figure 9: Adding a Server to the List
Once you have added the server name, click OK to close the Add Item dialog box. Click OK a few times until you are back in the Local Group Policy Editor and close the MMC.
Now you should be all ready to use SSO with Windows Server 2008 and 2008 Terminal Services.
Summary
In this article we covered the fundamental concepts of Single Sign-On (SSO) technology, how to use it with Windows Server 2008 Terminal Services and how to configure your Vista or 2008 based clients.

